Quantum System One at IBM, Quantum AI at Google, Azure Quantum at Microsoft, Qian Shi at Baidu... Since the end of the 2010s, quantum computing has become increasingly important, both in terms of the protection of and threats to IT security, as, eventually, this computing revolution could considerably undermine encryption-based security systems - in other words, almost all security systems. The quantum threat is a new challenge for cybersecurity, as long as you understand the phenomenon and avoid preconceived ideas.
Foreword: in the interest of making this paper understandable, we will not go into Grover's or Shor's algorithms or all the nuances of qubits (whether stable, noisy, annealing or otherwise). The mental well-being of our readers is also at stake.
The promises of quantum computing power
From traditional to quantum computing
While quantum computing is fascinating, it is also an extremely complicated subject to grasp. Behind the veneer, there are in fact many uncertainties - summed up in the famous quote attributed to the physicist, Richard Feynman: "I think I can safely say that nobody understands quantum mechanics." A paradigm to bear in mind as you read this paper. "When it comes to quantum, you shouldn't use intuition to try to understand it," adds Yvan Vanhullebus, Technical Leader at Stormshield. "As our intuition is based on our past experience and is not at all trained in quantum; so much so that it seems easier today to explain what quantum is NOT."
When it comes to quantum, you shouldn't use intuition to try to understand it. As our intuition is based on our past experience and is not at all trained in quantum; so much so that it seems easier today to explain what quantum is NOT.
Yvan Vanhullebus, Technical Leader at Stormshield
It is a complicated subject that is of particular interest to the world of cybersecurity, especially as quantum computing could revolutionise computing as we know it today. How? Thanks to the 'quantum leap', namely, the possibility of benefiting from optimised computing power and, as a result, being able to carry out complex mathematical operations that were previously impossible. As Yvan Vanhullebus explains: "The quantum computer uses the properties of matter on an infinitely small scale to perform in a few minutes certain calculations that would take at least several thousand years with today's most powerful computers."
Quantum computing is closely linked to the computing of a new unit: the quantum bit or 'qubit'. This unit, as explained in most articles, can have two values (0 or 1), but it can also have both values at the same time, which would allow all values to be calculated simultaneously. "But, in reality, it doesn't work like that: we are closer to the reality of quantum computing when talking about probabilities," as Yvan Vanhullebus explains, while referencing a comic book on this subject: The Talk by Scott Aaronson and Zach Weinersmith.

Caption: speech bubble from The Talk by Scott Aaronson and Zach Weinersmith, published in December 2016
The applications desired from quantum computing
A lot of firms have embarked on a technological race to achieve quantum supremacy. But what is quantum supremacy? It is the moment at which a quantum calculation of a given problem will be faster than its computer equivalent. Although some firms regularly state that they have achieved quantum supremacy, the actual move to an era of quantum computing is still some way off. In this supercomputing race, several announcements have been made by private firms such as Google, IBM and Baidu, each of which has made numerous announcements on its (more or less experimental) advances in this field. So, who has achieved quantum supremacy? There is no consensus among experts on the answer to this question: it transpires that not all qubits are equal... The quantities of qubits in the various announcements are sometimes surprising, as they do not always represent the same thing. As early as 2019, Google announced that it had achieved quantum supremacy, before Chinese researchers in 2021 - but, in both cases, the results were disputed. Between the 54 qubits of Google's Sycamore processor and the 433 qubits of IBM's Osprey processor, the qubit contest is open and in full swing.
Public bodies are actively involved in this technological race. In the United States, the NSA has been interested in the quantum sector for years (in 2014, it spent its first $80 million on a programme called Owning The Net). For its part, Europe plans to invest at least €4.5 billion in quantum technologies by 2027. In January 2021, the French government released €1.8 billion for quantum technologies. "A significant budget, but lower than Chinese and American investments," qualifies Noël Chazotte, Product Manager at Stormshield. "When you consider that the amounts mentioned are 25 billion dollars for the United States and 50 billion for China, Europe is not on the same scale."
Europe plans to invest at least €4.5 billion in quantum technologies by 2027. In January 2021, the French government released €1.8 billion for quantum technologies.
The stakes are high: it is a question of mastering a technology that is presented as revolutionary. The applications are numerous and concern many industrial sectors: simulating the functioning of the universe or the behaviour of matter at a molecular level, finding new habitable planets, producing better weather forecasts, creating drugs capable of treating major pathologies such as cancer or Alzheimer's disease, but also combating bank fraud and, more generally, improving the security of information systems. However, while the promises of this industry are impressive, quantum computing also poses a new threat to the cybersecurity industry.
The new threats introduced by quantum computing
A cyber-state threat?
Before giving credence to reports of a cybercriminal quantum threat, the threat could first be geopolitical in nature. "Clearly, the first state to win the race to master quantum technology will have supremacy over other states," explains Arnaud Dufournet, Chief Marketing Officer at TheGreenBow. "There will be quantum powers in the world, like there are nuclear powers. Today, it concerns China and the United States. In the future, it will take even longer for non-state cybercriminals to get this weapon." Would quantum computing then become a new lever for industrial and state espionage, or even geopolitical destabilisation? It is tempting to reply 'yes', as this national-security issue is being taken very seriously by many countries. In a rare public speech by the head of MI6, the British secret service expressed concern that certain so-called rogue states were positioning themselves in the field of quantum computing in view of future conflicts.
Clearly, the first state to win the race to master quantum technology will have supremacy over other states. There will be quantum powers in the world, like there are nuclear powers.
Arnaud Dufournet, Chief Marketing Officer at TheGreenBow
This latent threat, namely, the malicious use of quantum computing, consists of attacking asymmetric encryption keys. This would lead to the collapse of all encryption-based information systems and is even called the 'quantum apocalypse', a phrase taken from a widely reported BBC article. What is it? For companies, imagine that, from one day to the next, the security of your information systems is no longer guaranteed. A very real prospect according to Ilyas Khan of Quantinuum and Harri Owen of Post Quantum, interviewed by the BBC: "Everything we do over the Internet today, from buying things online to banking transactions, is encrypted. But once a functioning quantum computer appears that will be able to break that encryption... it will be able to clear bank accounts, completely shut down government defence systems - Bitcoin wallets will be drained."
A cyber threat that already exists
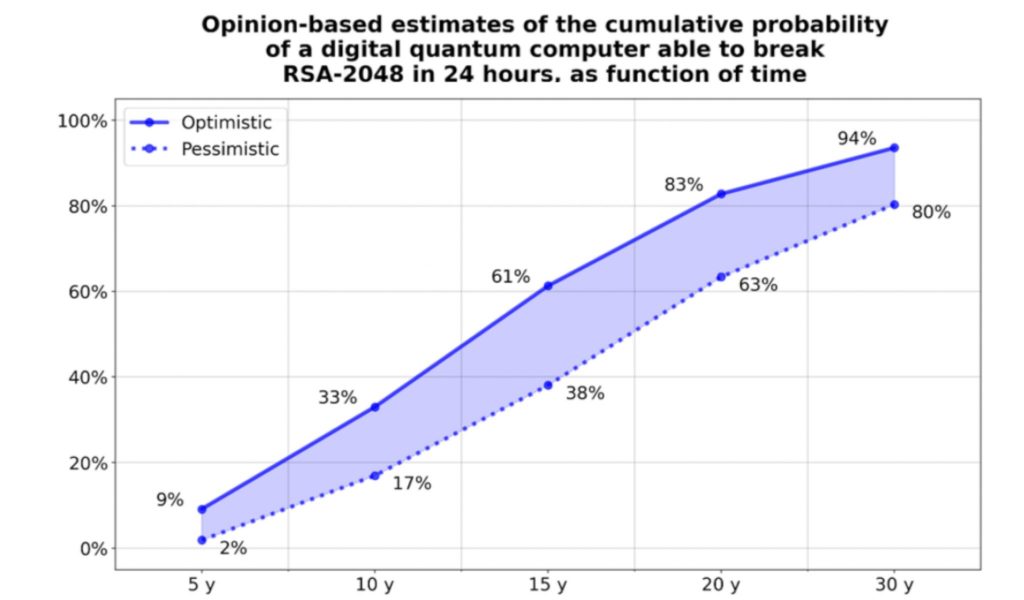
What is the nature of the new vulnerabilities brought about by the advent of the quantum era? They almost exclusively concern the security of cryptographic infrastructure, which could be undermined by quantum computing power that could bring down current asymmetric cryptographic systems (RSA, ECC, etc.), possibly leading to the hijacking of servers or entities involved in electronic exchanges and/or the decryption of data. To the point of making it possible to crack an RSA-2048 key in less than 24 hours? This was the question posed in the Quantum Threat Timeline Report in 2021, including estimates for the next 30 years. Between a five-year and a 30-year estimate, even pessimistic opinions rise from 2% to 80%! At the end of December 2022, a team of Chinese university researchers announced in a publication that it was able to decipher the RSA-2048 algorithm using a quantum computer. But such a public announcement raises questions: is it a real technological advance or a warning to Western countries? The question remains open.
However, these future attacks can be prepared with current data: in its opinion of April 2022, the French cybersecurity agency, ANSSI, mentions the case of retroactive cyberattacks called 'store now, decrypt later' attacks. Also referred to by others as 'hack now, decrypt later', 'harvest now, decrypt later' or 'capture now, decrypt later', the technique consists of recording a very large amount of encrypted data and communication today with the aim of decrypting it later, once quantum technology has been mastered. "The United States has already seen this type of attack on data with a very long lifespan, which can concern the country's infrastructure and military data," notes Arnaud Dufournet. He goes on to say: "In the banking sector, it will always be interesting to have data on the terms and amounts of certain strategic transactions. In the defence sector, information on submarines will be valid for decades. But this also applies to the energy sector, the car industry, industrial secrets, etc. There is already an urgent need to protect ourselves because some countries are starting to store data in anticipation of being able to decrypt it." "In the French medical sector, the question also arises," adds Yvan Vanhullebus, "as the law stipulates that a health centre (whether public or private) may keep your medical file for 20 years - securely, of course."
In its opinion of April 2022, the French cybersecurity agency, ANSSI, mentions the case of retroactive cyberattacks called 'store now, decrypt later' attacks. The technique consists of recording a very large amount of encrypted data and communication today with the aim of decrypting it later, even many years later, once quantum technology has been mastered.
Finally, crypto assets, including Bitcoin, which has a high media profile, could also see their infrastructure corrupted, contrary to their reputation as a non-falsifiable technology. According to researchers at the University of Sussex in the UK, a quantum computer with 13 million qubits could hack the Bitcoin blockchain in just 24 hours. It would then be possible to divert transactions and empty digital wallets. Other research is less alarmist, explaining that it will take another decade or two to reach this amount of power. Today, the hacking of the Bitcoin network by a quantum computer remains theoretical.
The need to adapt security products
A gradual move towards post-quantum cryptography
Does the future demise of current data-security algorithms in the face of quantum computing mark the end of encryption? "If the whole sector does not react in a concerted manner, yes," says Yvan Vanhullebus. He then qualifies this idea of planned obsolescence of encryption systems: "There is no real alternative - algorithms, protocols and systems will have to evolve." Evolution requires the development of mathematical algorithms capable of resisting conventional attacks and future quantum attacks. Just like certain symmetrical encryption algorithms: if the AES128 algorithm is considered to be 'cracked' by a future quantum computer, the AES256 is considered to be weakened but still quite resistant. In the US, this national-security matter is taken very seriously. In 2015, the Canadian physicist, Michele Mosca, presented the results of his research on quantum computing and introduced the theorem that would bear his name: Mosca's theorem. Seeking to answer the question, 'when should we worry about quantum?', he produced a theorem on what was to become one of the precepts of quantum computing. If the sum of the time during which encrypted data must remain secure (X) and the time required to re-tool the existing infrastructure with a large-scale quantum-safe solution (Y) is greater than the time required to build a large-scale quantum computer or any other relevant advance (Z), then you should worry.
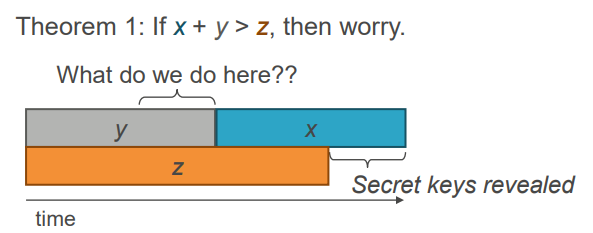
Caption: Michele Mosca's theorem from his presentation, Cybersecurity in a quantum world: will we be ready? in April 2015
Consequently, in 2016, the US agency, the NIST (National Institute of Standards and Technologies), launched a competition to develop post-quantum algorithms. The first four winners and their algorithms were announced six years later, in the summer of 2022, after several rounds of testing and analysis of all candidates. A second group comprising four other algorithms is still being studied. At the same time, the NSA's Director of Cybersecurity, Rob Joyce, explained that the agency had already classified its own algorithms that were developed in-house.
In fact, it is the entire cybersecurity world that now has to hasten its move towards a post-quantum world. Several avenues are emerging. On the one hand, post-quantum cryptography, which aims to study new mathematical problems underlying encryption protocols, so as to make them more resistant to attacks that the emergence of large-scale quantum computers would make possible. On the other, quantum cryptography, which modifies the physical medium of information by using new quantum technologies. Post-quantum cryptography is, for ANSSI, "the most promising solution to protect ourselves against the quantum threat." However, ANSSI's position is more cautious than that of its American counterpart, the NSA, which is pushing for the earliest possible adoption of post-quantum technologies. In a comprehensive opinion on the migration to post-quantum cryptography, published on its website in April 2022, ANSSI advises industry to move towards post-quantum algorithms gradually. A hybrid mechanism has the advantage of combining "the calculations of a recognised pre-quantum public-key algorithm and of an additional post-quantum algorithm" and of "benefiting from both the firm assurance of the former's resistance to conventional hackers and the latter's hypothetical resistance to quantum hackers." What about publishers, will they also have to change their encryption protocols to comply with post-quantum encryption? For Noël Chazotte, this move will have to take place, but one major unknown remains: what is the roll-out schedule? And with which algorithms? "On this subject, we can only go along with ANSSI: it is not yet mature. And it is impossible to foresee how post-quantum algorithms will behave in five years' time," he notes. "For example, for a long time, the SIKE algorithm offered a very promising solution for quantum computing, before its vulnerability to a conventional attack was revealed in the summer of 2022 by Belgian researchers."
Quantum Key Distribution for specific applications
Alternatives to post-quantum encryption exist, but they are less promising as they are limited to specific applications. This is the case of Quantum Key Distribution (QKD). QKD is a set of protocols for distributing an encryption key between two remote parties, while ensuring the security of the transmission thanks to the laws of quantum physics and information theory. It is a group of methods based on physical principles, not mathematical ones which are used in conventional cryptography. It allows two correspondents to create a 'common secret' (a key) to communicate. QKD is generally put forward for establishing confidential and secure communications, i.e. not modifiable by a hacker. For this, two channels are needed: a channel with controlled physical properties (optical fibre or a direct open-air link) without any device interacting with the information transported, and a conventional network link.
QKD is therefore entirely dependent on the physical characteristics of the channels it uses, which makes its large-scale roll-out "complex and costly", according to ANSSI. Furthermore, ANSSI considers that QKD is not "the natural development path for secure communications." This is because the lack of a direct line between two points forces users to negotiate keys in sections on a path consisting of several nodes, which requires trust in these intermediaries. This is "a major step backwards in relation to current end-to-end key negotiation methods," the French agency notes. This technology could therefore only be used for niche applications.
From theory to industrialisation
While the era of quantum computing is just emerging, the challenges are already numerous. In view of this new threat, active monitoring, anticipation, agility and adaptation are now essential for navigating between quantum computing and cybersecurity. On the one hand, the technological race to the quantum computer is complex and costly. The budgetary investments - several tens of billions of euros - also constitute a major obstacle. The need for cryptographic protection against quantum attacks is also complex and expensive. For Yvan Vanhullebus, "while the theoretical stage has already been reached, there are still major steps to be taken before we get to the industrialisation stage." The standardisation of the first algorithms was one of these steps, but, as recent as it is, it still requires time to step back and really assess the algorithms' solidity and robustness. In parallel, it will also be necessary to produce other standards for their use in a hybrid context, as recommended by ANSSI. The question surrounding hardware components, which by their very nature are highly inert, also has to be addressed now. "This is a subject that Stormshield took very seriously at an early stage," explains Yvan Vanhullebus. "For our Stormshield Network Security firewalls, for example, we are already integrating the latest TPM Infineon, the only TPM component on the market to offer post-quantum protection."
It is important that all cybersecurity players put measures in place now to anticipate the era of quantum computing and that of post-quantum cryptography. The aim? Not to be victims of but actors in this major technological development. In this context, Europe is seeking its place.