The Chinese group LuoYu, creator of the WinDealer malware, is back in the news recently. Active since 2008, this group targets foreign diplomatic entities operating on Chinese soil. Stormshield Customer Security Lab provides an update on the threat.
Context of the WinDealer malware
The GReAT cybersecurity research team at Kaspersky recently published an article detailing how the WinDealer malware works: securelist.com/windealer-dealing-on-the-side/105946/
In a nutshell, this malware is developed by a Chinese APT named "Luoyu" since 2014 and aims to spy on conversations of their victims. It collects information about Chinese residents and expatriates in order to identify "dissidents".
In its latest evolution, the malware targets even wider and opens up to other countries like Russia, the United States, Australia, Germany or Japan.
This malware has the ability to interact with its attacker via an atypical communication mechanism, involving the interception of HTTP and DNS requests. This would suggest the corruption of routers and DNS servers external to the company but on the path of Internet browsing network flows.
This principle allows the malware to be distributed in response to legitimate software that requests an update via unencrypted HTTP channels, but also to send information back to the C2 server without specifying the C2 address.
Technical details of the WinDealer malware
Malware delivery technique
In the case of intercepted HTTP requests "on the flow path", the malware can be distributed via spoofing responses to an HTTP request made by the client browsing a completely legitimate and uncompromised site. This mechanism tricks the user into executing the downloaded file
In terms of traffic interception, the decision whether to send the malware in response to a legitimate request is based on the IP address of the sender (which allows targeting of victims) and other unknown parameters.
The file is displayed to the user with an icon borrowed from the Google Chrome browser. Sometimes, the malware also borrows a name that reminds of some official programs that constitute Microsoft Windows:
The innovative point of the malware is undoubtedly its communication with its control server.
Communication with the C2 server
The communication between the malware and the control server is mainly based on the implementation of an agent capable of intercepting DNS requests in the network flow path.
Indeed, the malware has an ingenious mechanism to communicate with its C2 without ever exposing any IP address.
There is no magic. To send information to its C2, the malware initiates network communications to random IP addresses or to non-existent domain names:
- 62.0.0/15 (AS4134, CHINANET XIZANG PROVINCE NETWORK)
- 120.0.0/14 (AS4134, CHINANET GUIZHOU PROVINCE NETWORK)
- www.microsoftcom (note the absence of TLD)
Obviously, the C2 server is not directly behind all these IP addresses. Also, the domain name is invalid for an uncorrupted DNS server. The difficulty is then to reach the C2 server from these bad addresses.
However, depending on the properties and contents of the network packets sent to these destinations, the agent on the flow path can identify them and redirect them to the real control server.
In this way, it is possible to communicate with C2 without ever exposing the server address to the victims. The actual legitimate services hosted behind these destinations still remain functional and available to the rest of the world. Furthermore, no corruption of these services is required from the attacker's point of view.
Behavioral analysis against SES Evolution
We retrieved several samples of this malware and submitted to SES Evolution 2.2.2 using their names as they were encountered in the wild. Of the 10 files tested, 1 crashed (intercepted by WerFault.exe) and 9 were blocked by the "Flow Hijack" threat detection:
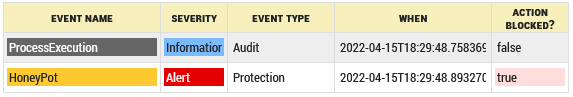
Figure 1: blocking log produced by SES Evolution
This situation occurs when programs try to execute complex processes that require system calls but from portions of shellcode.
In detail, the WinDealer samples in our possession were blocked when they discreetly called the "GetProcAddress" function (which returns the memory address of a function from a name provided as input, "LoadLibraryA" and "HeapAlloc" in the case of the samples studied). This complementary action is required for the good execution of the shellcodes since they do not benefit from the preparatory work carried out automatically by the PE-Loader of Windows on the normal EXE and DLL files.
The block is produced immediately after the malware starts since it begins with this attempt to evade the defense.
Protection means provided by Stormshield
Stormshield Network Security
A dedicated IPS signature has been published. It allows the C2 malware communication detection. The signature ID is as follow:
- udp:client:port.15 – WinDealer malware activity

Confidence index of the protection offered by Stormshield |
Confidence index of the absence of false positives |
Stormshield Endpoint Security Evolution
As previously mentioned, SES Evolution is able to detect and block the WinDealer malware at runtime thanks to the "Execution Flow Hijack" threat protection.
As this protection has been in place since SES Evolution 2.0 (summer 2020), all versions of the product with the security policies (all versions) provided with the product already respond to the threat. The malware process is killed before it can take any malicious action.
No action is required if Stormshield policies are in place.

Confidence index of the protection offered by Stormshield |
Confidence index of the absence of false positives |
Stormshield Endpoint Security 7.2
The SES 7.2 product is able to detect and block the WinDealer malware at runtime thanks to the HoneyPot Protection (HPP). With this protection, the malware process is killed before it can start any malicious action.
It is therefore necessary to activate this protection if you have not already done so.

Confidence index of the protection offered by Stormshield |
Confidence index of the absence of false positives |
IOC / Useful information
References of the samples studied for this analysis.
SHA-256:
- db034aeb3c72b75d955c02458ba2991c99033ada444ebed4e2a1ed4c9326c400
- 25cbfb26265889754ccc5598bf5f21885e50792ca0686e3ff3029b7dc4452f4d
- 1e9fc7f32bd5522dd0222932eb9f1d8bd0a2e132c7b46cfcc622ad97831e6128
- ea4561607c00687ea82b3365de26959f1adb98b6a9ba64fa6d47a6c19f22daa4
- ecd001aeb6bcbafb3e2fda74d76eea3c0ddad4e6e7ff1f43cd7709d4b4580261
- 318c431c56252f9421c755c281db7bd99dc1efa28c44a8d6db4708289725c318
- 28df5c75a2f78120ff96d4a72a3c23cee97c9b46c96410cf591af38cb4aed0fa
- 4a9b37ca2f90bfa90b0b8db8cc80fe01d154ba88e3bc25b00a7f8ff6c509a76f
- 08530e8280a93b8a1d51c20647e6be73795ef161e3b16e22e5e23d88ead4e226
- b9f526eea625eec1ddab25a0fc9bd847f37c9189750499c446471b7a52204d5a

