As you can see, we have been working on ransomware over the past few days. This time, we are talking about TeslaCrypt.
TeslaCrypt is a ransomware spread by e-mails or exploit kits. It encrypts your files and asks you to pay in order to retrieve the decryption key. The current version is 3.0. Many analysis are already available on the Internet. In this article we are focusing on two aspects of TeslaCrypt: the attack vector and the web callback.
Attack Vector - Bombila
Early in February 2016, Xylitol added an unknown panel on cybercrime-tracker.
After some research, we have found a binary file hosted on the server at the following address: hxxp://78.47.198.134/1.exe. More about it on VirusTotal: virustotal.com/en/file/6aa5fd384fbfe271a5000397e2e0c9d9e06dd5d041488e4f2de7ae3a4eb1589d/analysis/
This binary file is a bot which sends spam. It uses a list of compromised SMTP servers contained in the file hxxp://78.47.198.134/header/m.txt. This file (781 MB) contains around 4000 compromised SMTP accounts (Orange, SFR, Telefonica, Yahoo, Gmail, etc.). After that, the binary file retrieves a list of e-mails from hxxp://78.47.198.134/go_mails/botid-*****.txt. Directory listing was enabled on this directory, so we could find 139 text files for 792 256 e-mails.
The spam bot also retrieves some texts for crafted e-mails via several files in hXXp://78.47.198.134/header/. For example, some fake names: pastebin.com/3Xnn7krB and random text like:
Finally, the bot retrieves malicious attachments from the directory hXXp://78.47.198.134/go_attach/*****.zip. 200 zip files are waiting in this directory.
These Zip files contain malicious JavaScript droppers, each one dropping the TeslaCrypt ransomware.
Everyone has seen this type of attachment for the last few months in their mailbox.
Here is an example of these malicious droppers: virustotal.com/en/file/5acfac853e4ad0280be2bd44e4afb79d16cc7f5b4fd6ef45dde0007104f92c42/analysis/
This JS drops Malicious (TeslaCrypt) binary file from:
- hXXp://helloguysqq.su/85.exe
- hXXp://sowhatsupwithitff.com/85.exe
These servers are known for spreading the TeslaCrypt ransomware: virustotal.com/en/domain/sowhatsupwithitff.com/information/
When spamming, the binary file writes a lot of logs on the infected machine, such as:
And now let’s go to the funny part. After some guessing, we found an archive at hxxp://78.47.198.134/1.zip. This zip file (size: 468 MB compressed, 2 GB decompressed) is a full backup of the server. It contains all the files of this spamming server: source code, logs, payloads, etc.
For example, the source code of the spammer bot callback: pastebin.com/b9VWb5bk or index.php: pastebin.com/Tkh3UGfE. This archive contains also 45 millions of e-mails in different text files. This overview allows us to have a better understanding of how TeslaCrypt ransomware is spread. We can suppose that crooks carrying spam campaigns are different than the ones which manage the ransomware. I would like to thank the CERT Orange for their work and MalwareMustDie for their support.
TeslaCrypt - Web callback
Now, let’s talk about a not really documented part of the ransomware: the callback web. When a machine is infected by TeslaCrypt, the malware sends some data to a web callback on a compromised server. For example:
- hxxp://biocarbon\.com.ec/wp-content/uploads/bstr.php
- hxxp://imagescroll\.com/cgi-bin/Templates/bstr.php
- hxxp://music.mbsaeger\.com/music/Glee/bstr.php
- hxxp://stacon\.eu/bstr.php
- hxxp://surrogacyandadoption\.com/bstr.php
- hxxp://worldisonefamily\.info/zz/libraries/bstr.php
This callback is just a gateway to the real C&C hosted in TOR. The source code of such a callback is available at: pastebin.com/d7CvSpF0
Firstly, the page kicks IP from Microsoft:
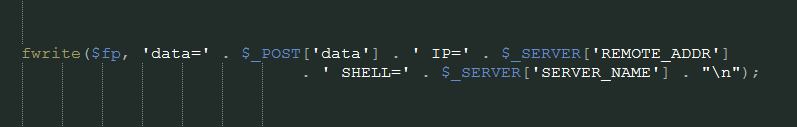
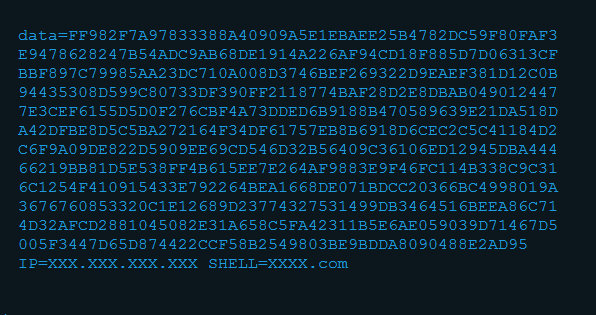
After that, the callback creates a file most.txt and logs all data received from infected machines in this file.
This file looks like:
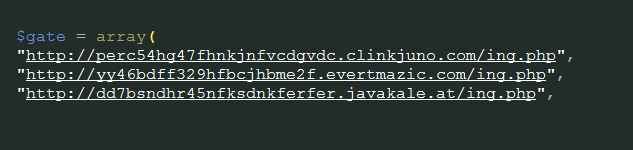
These data are also sent to three TOR callbacks:
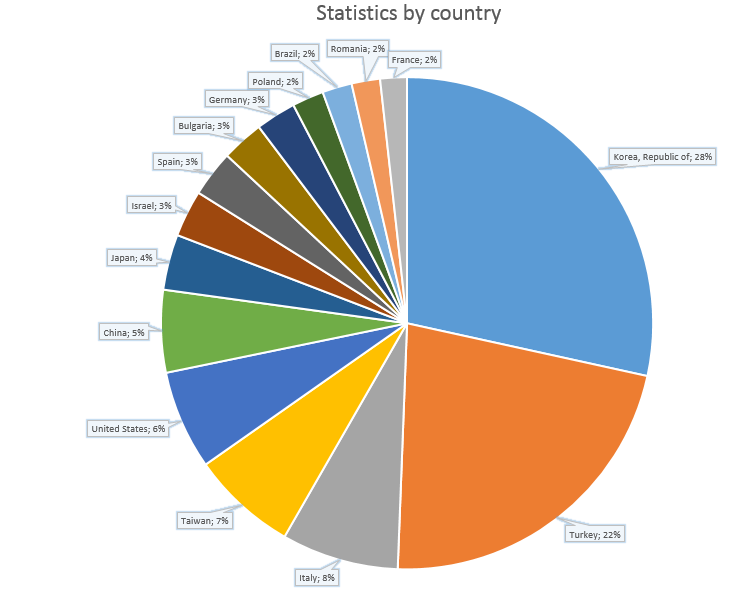
In the TeslaCrypt web kit, we can see another file named « cron.php » (source code available at: pastebin.com/LmtPT24L). The code compares three variables $_REQUEST['password'], $_REQUEST['re_password'] and $_REQUEST[login']. The aim of this code is still unclear. This information is perfect to follow the infection rate of TeslaCrypt. After grabbing most.txt file from different callback, we were able to do some statistics on a little part of this campaign and we retrieved 30 210 data raw:
- 15,290 unique IP addresses (due to NAT, one IP address can return several infected machine)
- 40 TOR exit node 🙂
Conclusion
We looked at another face of the TeslaCrypt infection: the attack vector and the web part. Both were interesting to analyse. These data are always interesting for estimating the infection rate of a campaign. The logged files show us that the infection rate is quite high, ransomware is definitely a lucrative business. The web part of ransomware is often forgotten; with different articles we will try to better understand the whole picture.