The summer is shaping up to be hot for Windows machines, as a cybersecurity researcher has discovered a new vulnerability in Windows 11 and Windows 10 versions. Update on critical vulnerability.
The context of the attack
On July 19, a cybersecurity researcher found that on Windows 11, certain sensitive files used to store Windows security information had overly permissive access rights. Digging deeper, he realized that some versions of Windows 10 were also impacted.
The recoverable information included local groups and accounts along with their password hash and encryption keys used to ensure system security.
This vulnerability was officially recognized by Microsoft as CVE 2021-36934 and carries the name of “HiveNightmare”, establishing continuity with the “PrintNightmare” vulnerability.
The impact of the attack
In possession of these files, an attacker can try to "crack" the passwords of local accounts through NTLM Reverse Hash. Although the operation is normally long, it is theoretically possible to find the password of a more privileged account and use it to open a session.
Accounts protected by "simple" and very commonly used passwords are particularly vulnerable to this technique.
Technical details of the attack
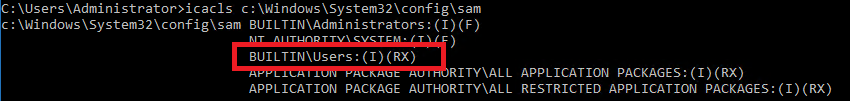
This vulnerability is a flaw in file permissions since explicit ACLs are set and expose the files for reading to any local user. These files are sensitive because they are used to store Windows security information. Here we are talking about the SAM and SECURITY registry hives.
Stored in "C:\Windows\System32\config\", on vulnerable systems, these files have permissions that allow any user to read them:
Luckily, these files are used in exclusive access by the system. Even if their ACLs did not block reading to any local user, access attempts would be rejected for exclusive access lock reasons.
On the other hand, if Shadow Copies (or restore points) are activated, these files are copied automatically by the system as they are (keeping the ACLs) to the backup volumes provided for this purpose. And it is precisely this location that the vulnerability targets because there is no lock acting as a second defence.
The attacker's scenario is therefore very simple: enumerate the Shadow Copies then copy the SAM and SECURITY files before analysing them with specialized tools. Although the path is not the most common, the copying of files is very much standard.
Means of protection provided by Stormshield
Protection Stormshield Endpoint Security
Confidence index of the protection offered by Stormshield
Confidence index of the absence of false positives
Being fully integrated with Windows, the SES solution provides a reliable and efficient response to the problem. The Stormshield Endpoint Security 7.2 and Stormshield Endpoint Security Evolution solutions make it possible to block the exploitation of this vulnerability thanks to a set of dedicated rules, provided in the MyStormshield space.
These rule sets include, for both versions, hardening of file ACLs on SAM and SECURITY located in the Shadow Copies volumes. The use of these rule sets is recommended until a patch is applied by Microsoft to correct the vulnerability.
Protection Stormshield Network Security
The SNS solution is not designed to deal with this type of vulnerability / threat.
Recommendations
In its page msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934,
Microsoft offers a manual method to eliminate the vulnerability. However, there is an impact to this: the possible loss of information that was present only in the restore points and above all the loss of restore points which may sometimes prove to be essential.
These recommendations are no longer necessary if the protection is imported into SES.

 Confidence index of the protection offered by Stormshield
Confidence index of the protection offered by Stormshield