After a great deal of cyber activity in June there was a lull until the end of July - do hackers take vacations in July too? With the Breach Fighter tool, Stormshield’s Security Intelligence team detects and analyzes malware by examining millions of spams and targeted attacks. From the coast’s beaches to the return of Locky - from one type of wave to another.
On vacation in July and back in August?
Breach Fighter is a tool that is built into hundreds of thousands of Stormshield Network Security firewalls deployed worldwide so as to aggregate the largest number of samples. Using this tool, the Security Intelligence team was able to identify a real variation in the volume of cyberattacks. After several peaks which occurred almost daily during June, volumes fell during most of July, with a modest resumption during the last few days of the month.
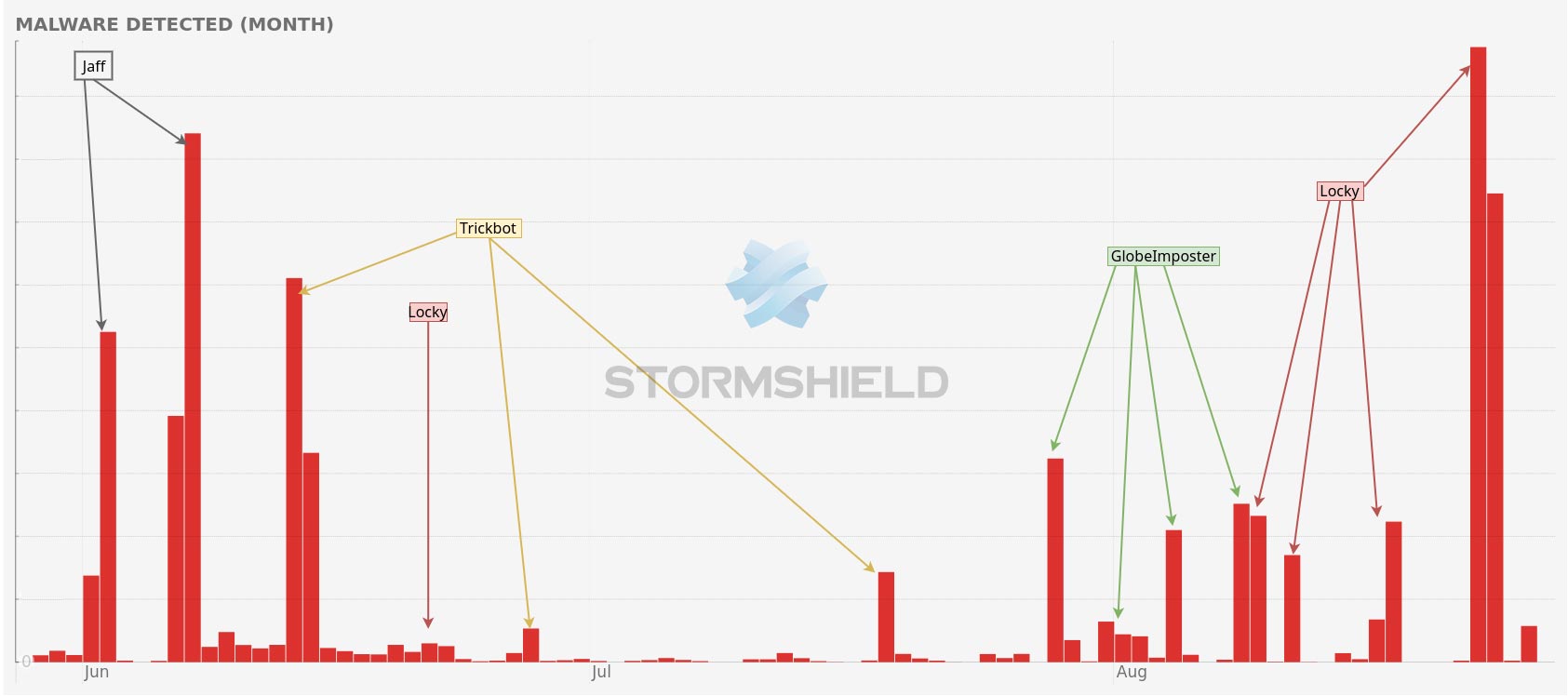
This considerable drop could suggest that web hackers, or their paymasters, take vacations too. Maybe they had to make a choice between their vacation budget and their malware budget.
We might also ask ourselves why cyberattacks resumed at the end of July-early August. Was it due to an overwhelming desire to see when Daenerys and Jon Snow leave the friendzone in Game of Thrones? Or a desire to influence FC Barcelona’s recruitment policy after Neymar’s departure? It’s anyone’s guess.
Cyber Threat Intelligence: prevention and reaction
Stormshield's Threat Intelligence team has two key missions. Not only does it study threats to gain an in-depth understanding and improve Stormshield's product portfolio, it also helps the cybersecurity community move forward by sharing expert opinions and working in close collaboration with professional organisations, including computer emergency response teams, administrative bodies and security specialists.
