Faced with growing threats to industrial systems and their IT infrastructures, the goal is primarily to reduce attack surfaces. Surfaces that can sometimes come from seemingly harmless things, like having a coffee from the machine when you arrive in the morning. This seemingly harmless action has already managed to put a whole industrial chain in danger. Can't we protect industrial infrastructure better using the multitude of technology that exists already? Answers at the link.
Everything started with a Reddit article. Written in July 2017, the author relates the difficulties his industrial (petrochemical) company had to face a malware infection. This company owns multiple factories in Europe, which have both local and remote control rooms. The author himself is working from the remote control room, and one day he receives a phone call from one of the factories: the local control room is down. After a short description of what the local operator sees, the author concludes to a ransomware attack (yes, one of the ones that hit the world mid-2017).
This should not be possible since no computers in the factory local control room are connected to the Internet. Nevertheless, the solution is easy; the author decides to remaster all the computers. Remastering is just wiping out the current memory and reinstall everything. Despite the reinstalling action, the computers were infected again a few minutes later. After serious headaches and a few less hair, the cause for the repeated infections was discovered: the coffee machine. A couple of weeks earlier the factory had a new smart coffee machine installed. It’s connected to the Internet and can place supply orders automatically. Unfortunately, it was also connected to the local control room network, instead of only being connected on an isolated Wi-Fi network. This was the entry gate for the malware. Fortunately, it didn’t prevent the factory to operate.
There are plenty of cybersecurity vendors and experts, how could a simple non-targeting ransomware reach such a critical environment? There‘s plenty of available strategies that could have prevented the infection by reducing the attack surface. In this article, you’ll find five solutions to reduce the attack surfaces. In addition, keep your industry safe.
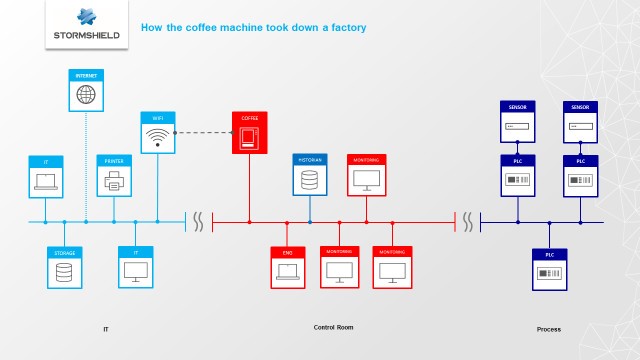
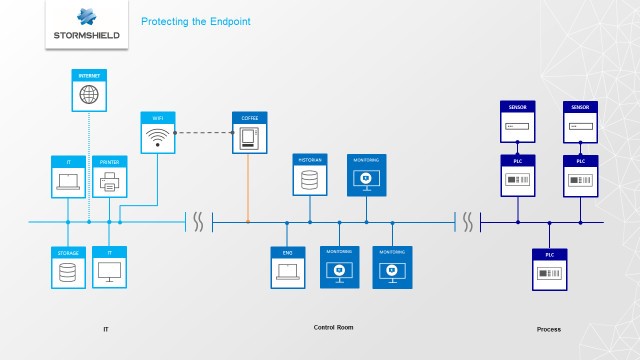
A quick schematic of the industry and the malware spreading in red.
Quick preamble for those who wonder what a surface attack is. According to “The Cybersecurity to English Dictionary”, surface attacks are “the sum of the potential exposure area that could be used to gain unauthorized entry to any part of a digital landscape. This area usually includes perimeter network hardware (such as firewalls) and web servers (hardware that hosts Internet-enabled applications). It can also include extended areas of the landscape such as external applications, supplier services and mobile devices that have permission to access information or services of value.” End of quotation.
#01st solution: Ensure the Endpoint Protection
Still according to “The Cybersecurity to English Dictionary”, Endpoint Protection is “a term used to describe the collective set of security software that has become standard for most user-operated digital devices. The security software may include anti-malware, a personal firewall, intrusion prevention software and other protective programs and processes.”
If the factory had Endpoint Protections on the local Control Room computers, the virus would not have been able to hit those computers.
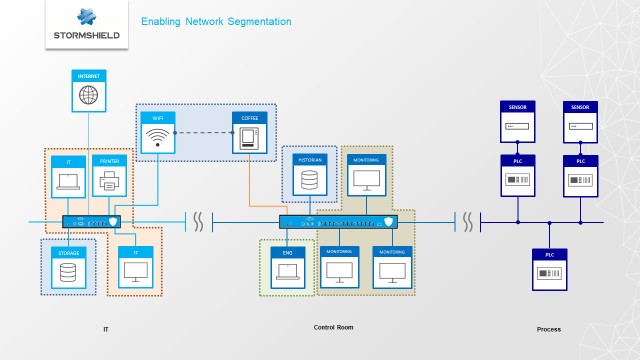
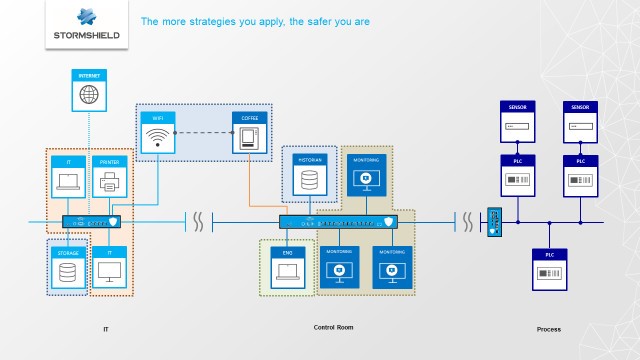
#02nd solution: Create a Network segmentation
To explain clearly what Network segmentation is, let’s not change of source: “Splitting a single collection of devices, wiring and applications that connect, carry, broadcast, monitor or safeguard data into smaller sections. This allows for more discrete management of each section, allowing greater security to be applied in sections with the highest value, and also permitting smaller sections to be impacted in the event of a malware infection or other disruptive event.”
With such a Network segmentation, since two zone could not talk one to another, the virus would not have been able to reach the local Control Room computers. Sadly for the coffee machine.
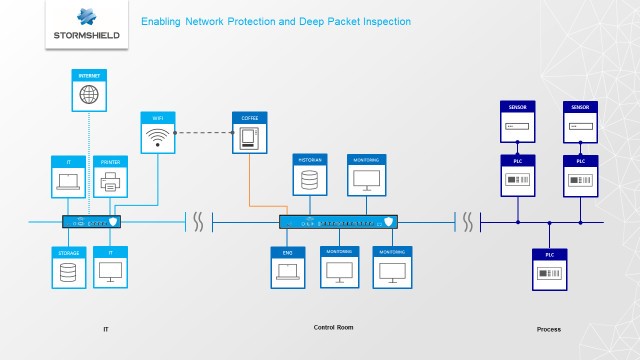
#03rd solution: Develop a better Network protection and achieve deep packet inspection
After the segmentation, the Network protection. It’s “the defensive and protective measures taken to secure a specific set of interconnected devices. Firewalls are an example of a network protection technology.”
And on top of these firewall, you can add a deep packet inspection mechanism. Also called DPI, it’s “a form of computer network packet filtering that examines the data part (and possibly also the header) of a packet as it passes an inspection point, searching for protocol non-compliance, viruses, spam, intrusions, or defined criteria to decide whether the packet may pass.” According to Wikipedia this time.
Through the firewall filter mechanism, a Network protection would have prevented the connectivity between the local Control Room computers and the coffee machine. In case of a needed connectivity, it would have been checked, via the deep packet inspection mechanism. In both cases, the virus would have been thrown to the garbage. Just like bad coffee.
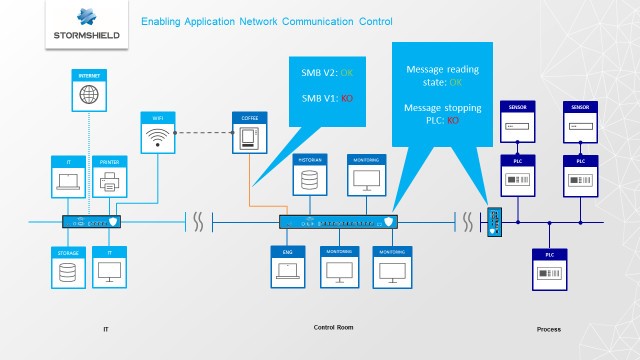
#04th solution: Establish Application Network Communication Control
Behind a complicated name, this solution is relatively simple as it deals with “the ability to ensure that only predefined or pre-allowed messages can go through protection inspection points”.
Do I really need to explain this one? Ok, with an Application Network Communication Control, not only you prevent the usage of undefined messages but you can also select among the legitimate messages (the ones that the DPI would not have blocked) the ones you want to pass through.
#05th solution: stop drinking coffee
Okay, that’s an easy one. And it deals also with tea drinkers.
But if you followed the previous solutions, you won’t need to go this far. Who wants sugar?
Conclusion: how to protect your industry from the coffee machine?
Add them all. The more strategy you’ll apply, the better protection you’ll get.