Between June and July 2021, two vulnerabilities were discovered around the Microsoft machine printing service. An update on a critical double vulnerability.
Attack context
Between 8 June and 6 July, Microsoft released two patches for vulnerabilities in the print service. CVE-2021-1675 is a vulnerability described as a Local Privilege Escalation (LPE), while CVE-2021-34527 is a Remote Privilege Escalation (RPE) vulnerability.
The second vulnerability is particularly worrying, as it concerns a service enabled by default on all Windows machines (workstations and servers; including domain controllers). It is reported that exploits are already available.
Technical details of the attack
The vulnerability is located in the spoolsv.exe service, specifically in the RpcAddPrinterDriverEx() function. This function is used to add drivers to a print server. This is notably called via an RPC (Remote Procedure Call).
The operation is simple: the client calls the function, with a file name (the driver) and a path (in UNC format) as parameters. This function "loads" this driver into the spooler, which can be stored on any network share accessible by the server.
The vulnerability lies in the ability to call this function via a specific flag in "dwFileCopyFlags", so bypassing the verification of privileges required to call this function. Thus, it is not necessary to be a privileged user to load potentially malicious drivers. In this vulnerability, the driver is an executable library (DLL) that will be loaded by the print spooler and executed with the SYSTEM account. Note that it is still necessary to be a domain user, which limits the scope of the attack.
What happens next with the attack then depends on the malicious load of the library that is loaded, which may be a malware dropper or a remote control tool.
Important note: By default, this service is enabled in all Windows systems, including Servers, so any non-hardened system is vulnerable.
Mitigation and correction with Stormshield
SNS and SES solutions can block attacks that exploit these vulnerabilities; here are the details of these protections.
Stormshield Network Security Protection
Due to the nature of the vulnerability, the RPC requests used to exploit it have the same characteristics as a legitimate DCE/RPC request. It is already possible to block all "RpcAddPrinterDriverEx" requests with the native application protection on DCE/RPC protocols, however the downside is that it blocks legitimate requests as well. This protection is configured here: Application Protection > Protocols > Microsoft Protocols > Microsoft RPC (DCE/RPC) > Predefined MS-RPC services > Microsoft RPC service spools
Additionally, we have developed the dcerpc:request:data.10 signature, updated automatically via Stormshield Auto-update, it is designed to identify malicious "RpcAddPrinterDriverEx" requests that specify the "APD_COPY_ALL_FILES | APD_INSTALL_WARNED_DRIVER | APD_COPY_FROM_DIRECTORY" flag combination as a parameter
Other requests, which do not specify this combination, will not be impacted.
It is strongly recommended to adapt the actions of this signature to your environment, as the default policy only blocks on high and internet profiles.
Stormshield Endpoint Security Protection
Based on what is currently known of the threat, Stormshield Endpoint Security 7.2 and Stormshield Endpoint Security Evolution block the exploitation of this vulnerability using a dedicated set of rules provided on the MyStormshield space. For both versions, these rulesets include:
- Network communications blocked for the spoolsv.exe process ;
- Connection to network shares blocked for spoolsv.exe ;
- Access to registry keys blocked for drivers known to be used by malicious tools exploiting this vulnerability.
In addition to the rules mentioned above, the advance in features of SES Evolution allows these rules to be refined further and to add additional protective barriers. This set of rules includes:
- Blocking the creation of child processes by spoolsv.exe;
- Blocking the loading of executable code based on the module owner.
The use of these rulesets is recommended until a patch is available from Microsoft and applied to correct these vulnerabilities. Note some rules may restrict the legitimate operation of print servers.
Other recommandations
Disabling Spooler Services
Check and stop the Print Spooler services on servers that do not need them, especially Active Directory servers. To do this, the Spooler service (spoolsv.exe) must be disabled at startup: Set-Service -Name Spooler -StartupType Disabled, and then stop the service: Stop-Service -Name Spooler
For user workstations, it is necessary to disable inbound remote printing requests. This can be done via GPO ; go to "Computer Configuration", "Administrative Templates", "Printers" and set the parameter "Allow Print Spooler to accept client connections" to "Disabled".
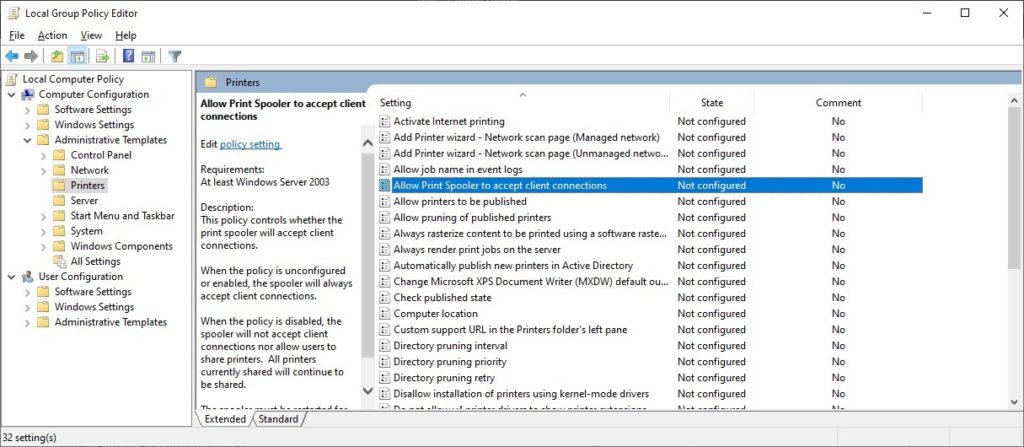
Fig 1 : GPO configuration
Server Updates
It is important to update the relevant servers (i.e. those with an active print spooler service).
The Microsoft KBs are as follows :
- KB5004945 for Windows Server 20H2, Windows Server 2004, Windows 10 20H2, Windows 10 2004, Windows 10 21H1;
- KB5004946 for Windows 10 1909;
- KB5004947 for Windows Server 2019, Windows 10 1809;
- KB5004950 for Windows 10;
- KB5004948 for Windows Server 2016 and Windows 10 1607;
- KB5004951 and KB5004953 for Windows Server 2008 R2 and Windows 7;
- KB5004956 and KB5004960 for Windows Server 2012;
- KB5004954 and KB5004958 for Windows Server 2012 R2 and Windows 8.1;
- KB5004955 and KB5004959 for Windows Server 2008 SP2.
Note that versions no longer maintained by Microsoft will not be patched.