A new group of cyber criminals, Black Basta, is making the news at the end of April, having already impacted more than 12 companies. The group is very young, as their first identified target only dates from the first half of April. But given their track record, it is very likely that this is an established group that has decided to change its name. Here is an update on the ransomware associated with the group, from the Stormshield Customer Security Lab team.
Context of the Black Basta attack
On 20 April, the French property management company Oralia announced that it had suffered an attack that paralysed its computer system. Very quickly, the attack was claimed via a showcase site on the darkweb, belonging to a new group of cyber criminals: Black Basta.
Although the deployment vector is still undetermined, the ransomware used is relatively classic: after hijacking a legitimate Windows service to run in safe mode, it exfiltrates the data on the computer and encrypts it. It also makes sure to delete all backups, resulting in the loss of data on the affected machines (server or workstation).
Ransomware technical details
To date, three variants of this ransomware are known:
- 17205c43189c22dfcb278f5cc45c2562f622b0b6280dcd43cc1d3c274095eb90
- 7883f01096db9bcf090c2317749b6873036c27ba92451b212b8645770e1f0b8a
- 5d2204f3a20e163120f52a2e3595db19890050b2faa96c6cba6b094b0a52b0aa
An inspection shows that there is no signature associated with these files. An Interesting fact is that one of the three files appears to be a prototype of the two others, with a different ransom note and encrypting the files directly without trying to destroy the machine's backups. It even allows the display of debugging logs to see the execution of the binary – a very rare occurrence, which would confirm the hypothesis of a test binary.
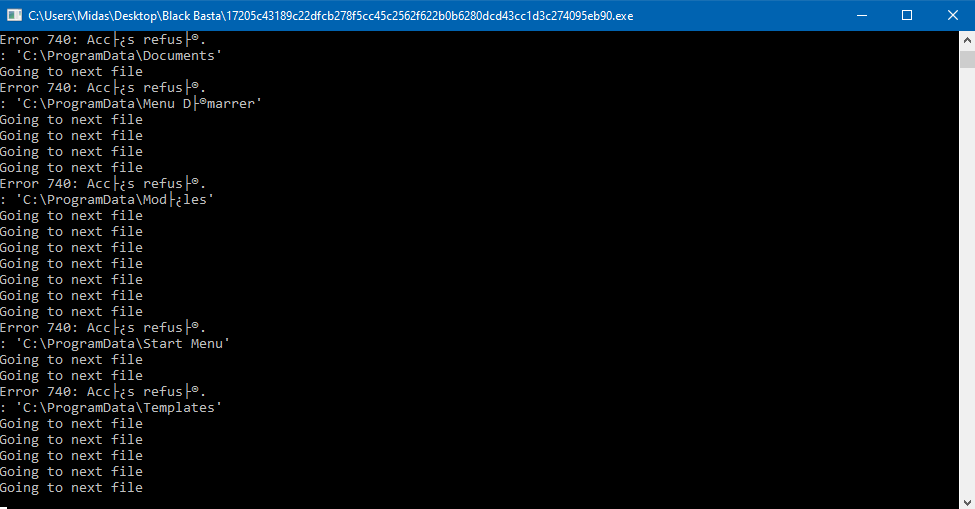
Figure 1: console display of file encryption
The malware has not been post-compiled to make it difficult to analyse. In this sense, it is not compacted (packaged) and the strings appear in clear text. Compared to the other two samples, it differs in several ways:
- The way of encryption is different: there is no reboot;
- The ransomware note is different and much longer;
- The screen display is different: no image is used.
The ransom note explicitly states the encrypted ransomware as "no_name_ransomware".
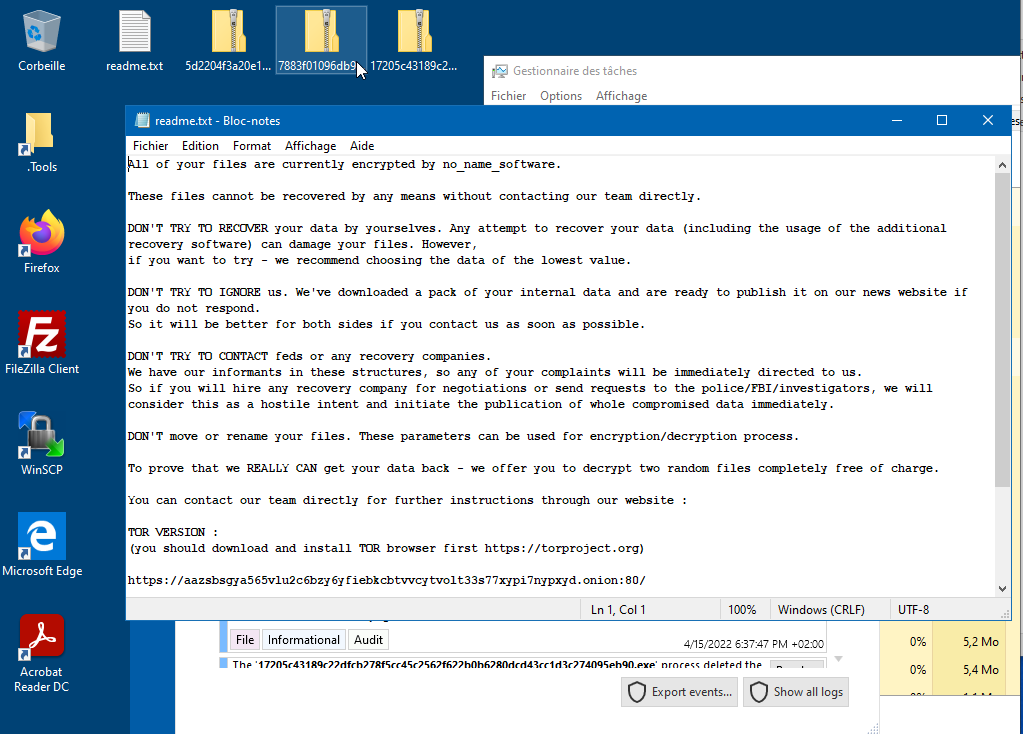
Figure 2: Ransom note when the prototype encrypts the post
In terms of operation, when the malware starts its execution, it encrypts the resources of the computer in addition to dropping the note.
The differences with the prototype end there, because unlike the first malware, the two following ones are much more accomplished. Their objectives are multiple: to bypass the computer's protections, to delete backups and to encrypt the computer. These two samples are processed at the same time because, although they have a different hash, they perform more or less the same actions.
The Black Basta strain performs the following actions:
- Deletion of the backup (Shadow copies) via the command cmd /c vssadmin.exe delete shadows /all /quiet
- Registration in the Windows boot manager to boot into safe mode with network support bcdedit /set safeboot network
- Expropriation of a Windows service started in safe mode
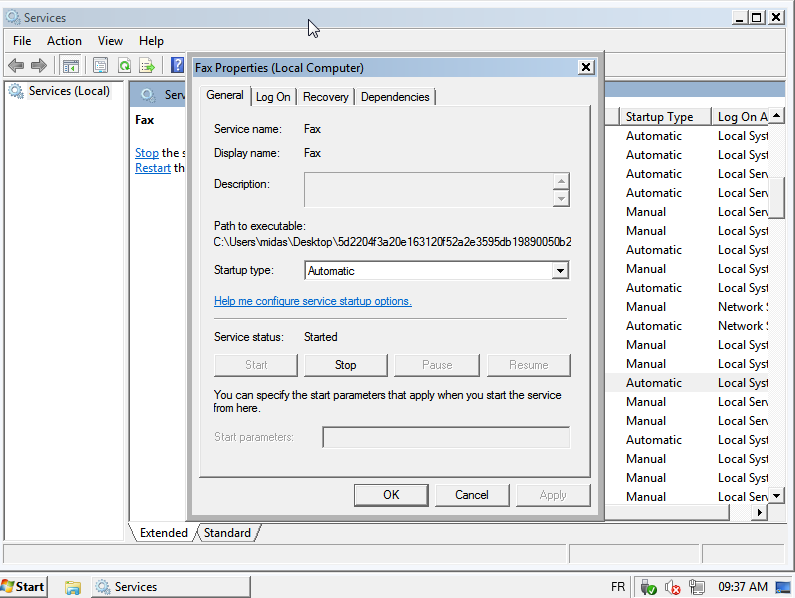
Figure 3: The Windows Fax service is redirected to start the malware when the computer starts up
- Restart the computer to make it go into safe mode shutdown -r -f -t 0
- Running the load in safe mode
- Exfiltration of files
- Encryption of files, the algorithm is ChaCha20 with a '.basta' extension
- Submission of the ransom note
- Change of the desktop background.
It is interesting to note that despite hijacking an automatically started service, the load will not restart and re-encrypt the files because the fax service is disabled afterward.
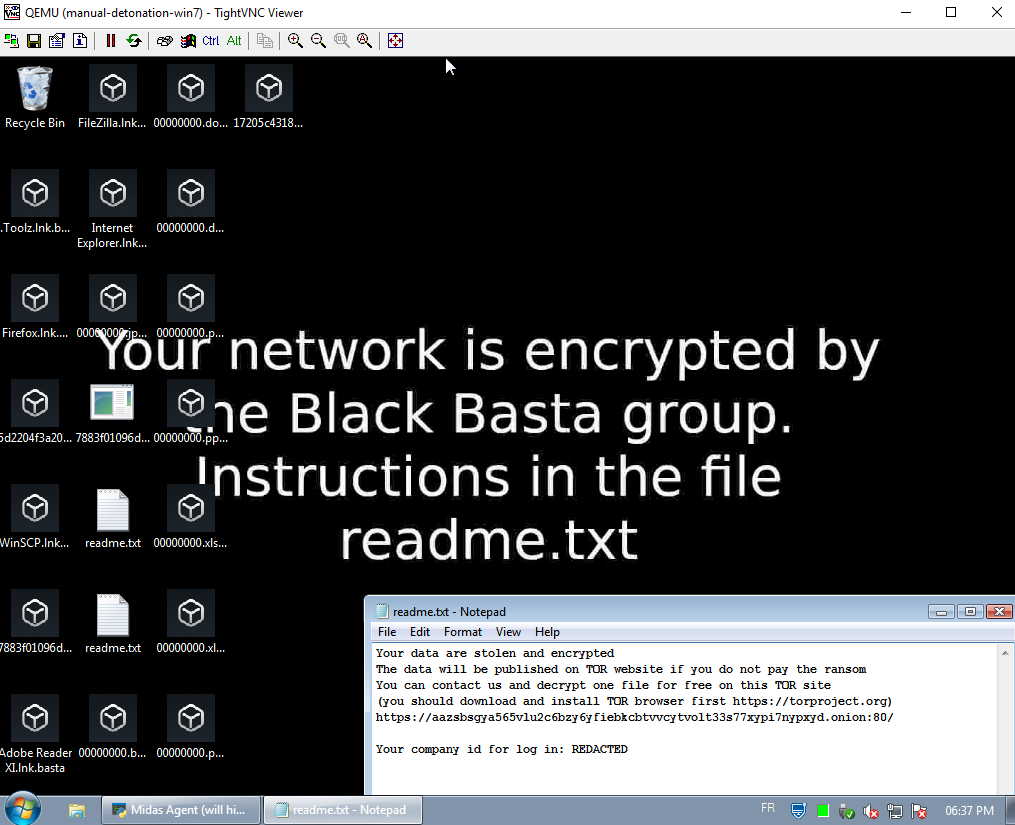
Figure 4: The endpoint is encrypted and unusable
Targeted systems
This malware attacks Windows XP, Vista, Seven, 10 and 11 systems, both 32-bit and 64-bit, regardless of the system language.
Other information
Administrator rights
This malware absolutely requires administrator rights in order to drop the driver and load it. This is not a problem for the cyber criminals, as in the attack vector observed, the deployment of the malware was done through an initial compromise of the fleet.
Execution time
The malware performs its malicious actions very shortly after starting up. Thus, as soon as its CPU activity drops to 0%, the system is already corrupted. Windows system files are preserved to keep the system running. Note that the malware ends after encrypting the rest of the system.
Reboot
The malware requests an immediate safe mode reboot of the machine after taking over a Windows service.
Miscellaneous
- The VSS service is asked to delete all backups of the machine.
- The malware associates files with the extension '.basta' with an icon that it applies via registry changes
- The malware changes the desktop background with an image that it applies via registry changes
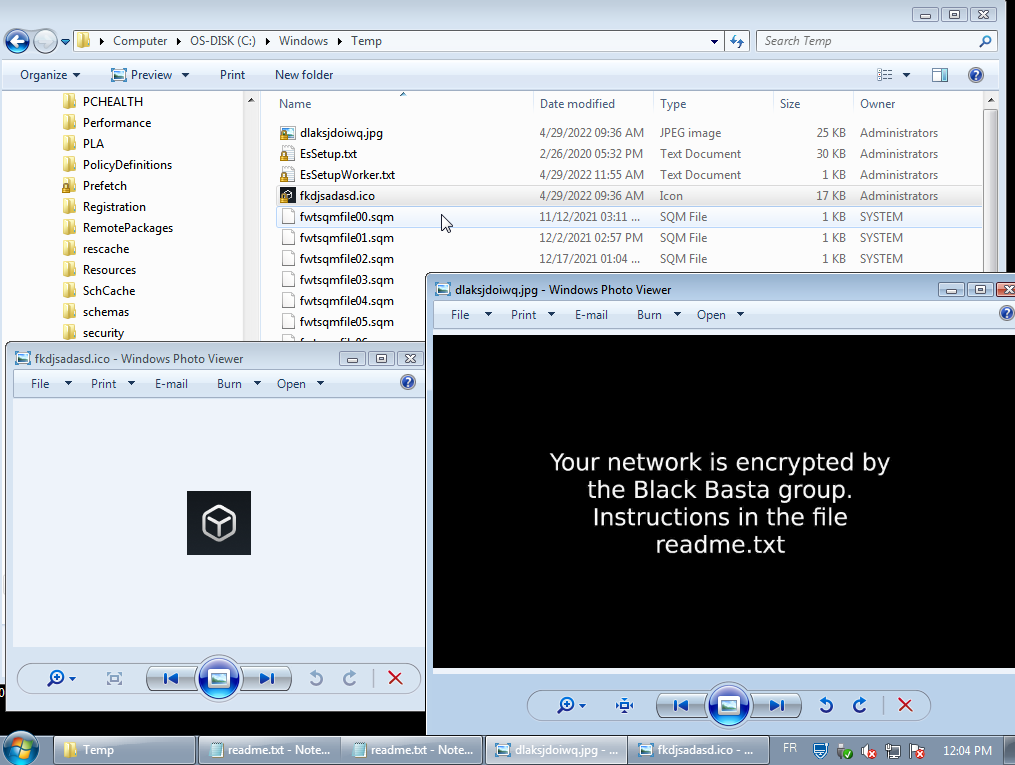
Figure 5: Resources deposited by the malware
Stormshield products protections
Stormshield Network Security
Breach Fighter, a SaaS sandboxing solution that complements SNS, detects all Black Basta type ransomware.
When a file passes through the relevant stream, SNS will perform a hash of the file and check its safety with Breach Fighter (in case of an unknown file, it will be sent to our cloud detonation environment). It will then be blocked immediately.
For this detection to be effective, you must:
- have the Premium Security Pack license and the Breach Fighter option;
- activate sandboxing on all file transporting flows (SMTP, HTTP, FTP).

Stormshield protection confidence index |
Stormshield confidence index of no false positives |
Stormshield Endpoint Security Evolution
The anti-ransomware protection rule set present by default in an SES installation can block these malware strains.
Specifically, the prototype binary is blocked by the anti-ransomware heuristic. The "real" Black Basta strain is blocked by the protection against deletion of shadow copies before a single file is encrypted.
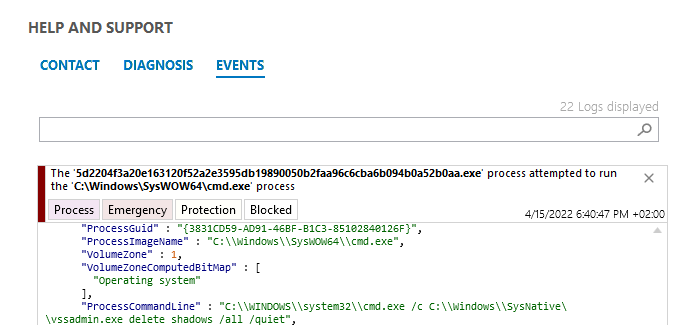
Figure 6: illustration of the blocking rule

Stormshield protection confidence index |
Stormshield confidence index of no false positives |
IOC / Useful information
Sha256:
- 5d2204f3a20e163120f52a2e3595db19890050b2faa96c6cba6b094b0a52b0aa
- 7883f01096db9bcf090c2317749b6873036c27ba92451b212b8645770e1f0b8a
- e64a1150535a823aa2d2c4c92ab8a3804703aae7126500fd000a4447233b65fb
Breach Fighter portal: