Stormshield CTI team came across two servers during our active threat hunting. They share a lot of similarities with servers reported by Check Point on APT35. The servers are active and resolve multiple domains used for phishing purpose. This blogpost shows how we found them, and how other security teams can do the same.
The code behind the song
APT35, also known as Mint Sandstorm / Charming Kitten / Educated Manticore, is an APT group affiliated with the Islamic Revolutionary Guard Corps (IRGC), a branch of the Iranian Armed Forces. This group is active since at least 2015 and carries out espionage and surveillance activities. It targets government, military, media, academic and international organizations located in the US, Middle East and Europe.
We were interested in the HTML page mentioned in the Check Point report. It was displayed on some domains and looks like four coloured dots:
![Screenshot from viliam.ude-final[.]online, source: URLScan.io](https://www.stormshield.com/wp-content/uploads/screenshot-viliamude-finalonline-300x97.png)
Figure 1: Screenshot from viliam.ude-final[.]online, source: URLScan.io
The source code of the page is straightforward, as showed below:
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width,initial-scale=1">
<link rel="stylesheet" href="/styles/font.css">
<script defer="defer" src="/static/js/main.7e80d47f.js"></script>
<link href="/static/css/main.365793d0.css" rel="stylesheet">
</head>
<body><noscript>You need to enable JavaScript to run this app.</noscript>
<div id="rb">
<div class="wrapper-loading">
<div class="blue ball"></div>
<div class="red ball"></div>
<div class="yellow ball"></div>
<div class="green ball"></div>
</div>
</div>
</body>
We observed that this page is hosted on multiple domains associated with the campaign reported by Check Point, with only the paths to the JavaScript script and CSS style sheet changing. We wanted to see if we could create a query to hunt confidently for other pages in the wild. Using the SilentPush platform, we were able to craft a request that matches this behaviour, using the html_body_ssdeep attribute:
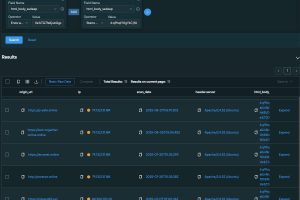
Figure 2: Query results in SilentPush UI
We found eight matches related to IPv4 addresses mentioned in Check Point report: 45.143.166[.]230 and 195.66.213[.]132. We also found matches for two undocumented IPv4s: one for 84.200.193[.]20 (rohand63[.]xyz) and four for 79.132.131.184 (arcanet[.]online, look-together-online[.]online).
Typo squatting melody
The server 84.200.193[.]20 (AS 214036 Ultahost, Inc.) resolved domains mostly in July 2025, for a period of two to 12 days. There is only one domain still resolving this IPV4: rohan63[.]xyz.
![Hosting timeline for IPv4 84.200.193[.]20, source: Validin](https://www.stormshield.com/wp-content/uploads/screenshot-14827-appvalidincom-300x191.jpeg)
Figure 3: Hosting timeline for IPv4 84.200.193[.]20, source: Validin
The server, 79.132.131[.]184 (AS 39378, SERVINGA), resolves 49 domains, all with the “online” TLD. This IPv4 is active since at least July 20th 2025 and is still used at the time of writing. The most recent resolving domain, proof-video[.]online, was registered on September 20th 2025. All domains seem to be used for phishing purpose, most of them masquerading as video conferencing related domains, with naming such as meet.go0gle[.]online or meet.video-connect[.]online.
![Hosting timeline for IPv4 79.132.131[.]184, source: Validin](https://www.stormshield.com/wp-content/uploads/screenshot-appvalidincom-300x187.jpeg)
Figure 4: Hosting timeline for IPv4 79.132.131[.]184, source: Validin
Using Google Meet, and more broadly the video conference theme, for phishing purpose is part of APT35’s TTPs since at least 2023 (see Google report).
Highways to hell
While investigating, we also found behaviours that could be used for tracking.
The first one is the URL query. We observed that searching on VirusTotal for URL with the online TLD and the query “?invitation” yields results. Here are all URLs we found with the following VT query entity:url url:online/?invitation.
URL | Submission Date | Submitted From |
hxxps://viliam.superlite[.]online/?invitation-ter-nsbs-oer | 2025-07-15 | Sweden |
hxxp://viliam.sky-writer[.]online/?invitation-caq-beqd-ery | 2025-08-03 | Israel |
hxxps://viliam.alpha-met[.]online/?invitation-ter-nsbs-oeht | 2025-08-10 | Israel |
hxxp://viliam.alpha-met[.]online/?invitation-tgr-nzfes-ohr | 2025-08-10 | Israel |
hxxps://meet.ell-safe[.]online/invitation-fgh-rewk-evg | 2025-09-17 | Israel |
We also found a very simple way to track new domains: just searching for subdomains starting with “viliam.” works well: entity:domain domain:viliam.*
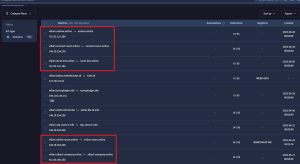
Figure 5: Screenshot of the query on VirusTotal with matching indicators highlighted
The query found 112 domains at the time of writing. Not all of them are related to APT35 infrastructure, but it seems to be a good way to start looking for it.
Ending the show
The campaign reported by Check Point is still ongoing. APT35 did not change the way they set up their phishing domains since their last reported activity. It makes the task easier for defender to track their activities. The submitted URLs suggest that this campaign is still targeting Israel.
Every indicator shared on this blogpost is already blocked on Stormshield products.
Appendix
Queries
Platform | Query | Confidence |
SilentPush | datasource = ["webscan"] AND html_body_ssdeep = "*Ve1LTG7faKjubGga" AND html_body_ssdeep = "6:q9hqIY0gYkC/fAbplGMuzT6palUvN*" | High |
VirusTotal | entity:domain domain:viliam.* | Medium |
VirusTotal | entity:url url:online/?invitation | High/Medium |
Indicator of compromises
Value | Type | Comment | Confidence |
79.132.131[.]184 | IPV4 | IPv4 hosting phishing domains | High |
84.200.193[.]20 | IPV4 | IPv4 hosting phishing domains | High |
viliam-live-identity[.]online | Domain | Phishing domain | High |
viliam.viliam-live-identity[.]online | Domain | Phishing domain | High |
proof-video[.]online | Domain | Phishing domain | High |
look-together-online[.]online | Domain | Phishing domain | High |
meet.proof-video[.]online | Domain | Phishing domain | High |
www.look-together-online[.]online | Domain | Phishing domain | High |
viliam.look-together-online[.]online | Domain | Phishing domain | High |
www.video-connect[.]online | Domain | Phishing domain | High |
meet.video-connect[.]online | Domain | Phishing domain | High |
video-connect[.]online | Domain | Phishing domain | High |
www.go0gle[.]online | Domain | Phishing domain | High |
meet.go0gle[.]online | Domain | Phishing domain | High |
go0gle[.]online | Domain | Phishing domain | High |
tensore[.]online | Domain | Phishing domain | High |
ell-safe[.]online | Domain | Phishing domain | High |
azdava[.]online | Domain | Phishing domain | High |
meet.azdava[.]online | Domain | Phishing domain | High |
meet.ell-safe[.]online | Domain | Phishing domain | High |
viliam.azdava[.]online | Domain | Phishing domain | High |
viliam.tensore[.]online | Domain | Phishing domain | High |
viliam.teslator[.]online | Domain | Phishing domain | High |
teslator[.]online | Domain | Phishing domain | High |
viliam.kuret-live[.]online | Domain | Phishing domain | High |
kuret-live[.]online | Domain | Phishing domain | High |
book.kuret-live[.]online | Domain | Phishing domain | High |
viliam.safe-lord[.]online | Domain | Phishing domain | High |
safe-lord[.]online | Domain | Phishing domain | High |
www.p-safe[.]online | Domain | Phishing domain | High |
viliam.p-safe[.]online | Domain | Phishing domain | High |
p-safe[.]online | Domain | Phishing domain | High |
into-support[.]online | Domain | Phishing domain | High |
villiam[.]online-speak[.]online | Domain | Phishing domain | High |
viliam[.]online-speak[.]online | Domain | Phishing domain | High |
online-speak[.]online | Domain | Phishing domain | High |
viliam.into-support[.]online | Domain | Phishing domain | High |
viliam.alpha-met[.]online | Domain | Phishing domain | High |
alpha-met[.]online | Domain | Phishing domain | High |
viliam.kuret-met[.]online | Domain | Phishing domain | High |
viliam.live-board[.]online | Domain | Phishing domain | High |
live-board[.]online | Domain | Phishing domain | High |
www.owner-rate[.]online | Domain | Phishing domain | High |
viliam.owner-rate[.]online | Domain | Phishing domain | High |
owner-rate[.]online | Domain | Phishing domain | High |
viliam.alpha-meet[.]online | Domain | Phishing domain | High |
alpha-meet[.]online | Domain | Phishing domain | High |
arcanet[.]online | Domain | Phishing domain | High |
viliam.arcanet[.]online | Domain | Phishing domain | High |
viliam.cppsg[.]online | Domain | Phishing domain | High |
cppsg[.]online | Domain | Phishing domain | High |
rohand63[.]xyz | Domain | Phishing domain | High |
www.rohand63[.]xyz | Domain | Phishing domain | High |
viliam.rohand63[.]xyz | Domain | Phishing domain | High |
robinthing123[.]online | Domain | Phishing domain | High |
viliam.robinthing123[.]online | Domain | Phishing domain | High |
viliam.superlite[.]online | Domain | Phishing domain | High |
superlite[.]online | Domain | Phishing domain | High |
dmn-inter[.]online | Domain | Phishing domain | High |
viliam.dmn-inter[.]online | Domain | Phishing domain | High |
www.toolfare[.]online | Domain | Phishing domain | High |
viliam.toolfare[.]online | Domain | Phishing domain | High |
toolfare[.]online | Domain | Phishing domain | High |
oranus.besatoo[.]online | Domain | Phishing domain | High |
viliam.besatoo[.]online | Domain | Phishing domain | High |
mickel.besatoo[.]online | Domain | Phishing domain | High |
live.besatoo[.]online | Domain | Phishing domain | High |
besatoo[.]online | Domain | Phishing domain | High |
