On March 23rd, Microsoft issued an advisory about two 0-day vulnerabilities in Adobe Type Manager (ATM) library, allowing to execute code remotely. These vulnerabilities are actively being used in targeted attacks. There is currently no patch available.
About the vulnerabilities
These vulnerabilities in Adobe Type Manager library (which, despite its name, is exclusively maintained by Microsoft and included in all vulnerable Windows versions) allow an attacker to execute code remotely in Windows by having it process specially crafted fonts files.
There are many exploitation vectors of these vulnerabilities, from a document (or executable, or script) file embedding a malicious font, to the browsing into a local folder or remote server (in the organization, or using WebDav).
Microsoft is currently working on a fix, but Windows 7, Windows 2008 (including 2008 R2) should not receive patches as they are not maintained anymore.
Affected systems
The following operating systems are affected: Windows 10, Windows 8.1, Windows 7 and Windows Server 2008 to 2019.
For versions Windows 10 1703 and higher, remote malicious code execution is more complex to achieve, and actions that can be done by the attacker are greatly reduced, as they will be able to get only limited rights and features.
Microsoft recommendations
Microsoft provides multiple recommendations in the published advisory.
How Stormshield Endpoint Security responds
Windows Server 2008 to 2016, Windows 7, Windows 8.1 and Windows 10 up to 1609
On these OS, vulnerabilities exploitation will be done by performing a privilege elevation from the kernel.
In that case the exploitation is detected when Protection against privilege escalation is Enabled (see SES Administration Guide, pages 139-140).
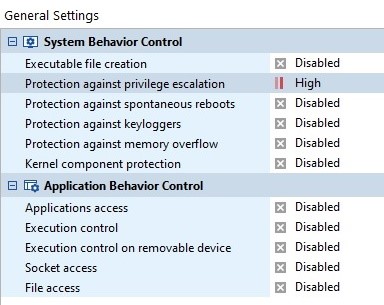
The protection against privilege escalation is disabled by default.
Windows Server 2019, Windows 10 1703 and above
On these systems the attack methodology is not the same and the exploitation of these vulnerabilities CANNOT be detected by SES.
As mentioned above, in this configuration it is important to consider that the malicious code will be much more difficult to execute, as more recent OS offer multiple efficient mitigations to detect and prevent such attacks. In case it can get executed anyway, actions that can be performed by the attacker will be greatly limited: no possibility to create a process or dynamic code, or to load a binary – only binaries signed by Microsoft and already present locally can be loaded.
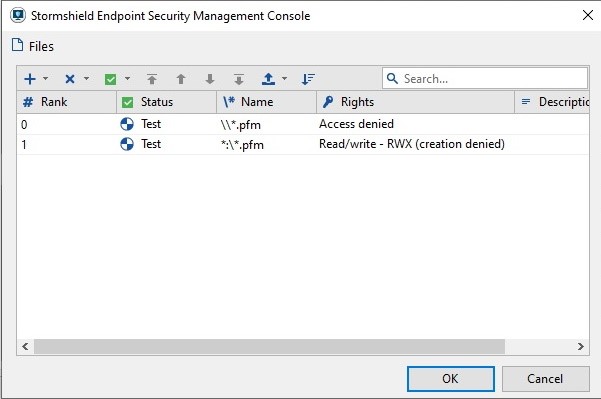
Corrupted files are font files ‘Adobe Type 1 PostScript’ and usually have .PFM extension. It is then possible to audit all when any .PFM file is created and read so that the administrator can be alerted of potential exploitation of these vulnerabilities. This is done by creating an extension rule for .PFM files (see SES Administration Guide, pages 126-127).
Such files can be used in a legitimate way by some applications (for exemple, Acrobat Reader DC contains 3 PFM files in subfolder Resource\Font\PFM). This audit rule allows mainly to detect a potential exploitation of vulnerabilities when a user is browsing with Windows Explorer in a folder with such a font.
How Stormshield Network Security responds
Breach Fighter
In case a file can be launched and is autonomous (whether a script, an executable or a document, each of them embedding a malicious font file), the exploitation of the vulnerabilities will be detected by Breach Fighter, as a privilege elevation from the kernel.
As a result, Breach Fighter offers partial protection depending on the attack methodology, for Windows Server 2008 to 2016, Windows 7, Windows 8.1 and Windows 10 up to 1609.
However, as mentioned above, more recent systems for which detection is not possible are also less vulnerable.
IPS Signature - 03/27 updated
A signature “Printer Font file download detection” is now available to detect downloads of PFM, PFB and PFA files, as well as email attachments with these extensions. It is configured by default in “pass” mode to avoid blocking potential (rare) legitimate downloads of such files, but we advise you to put them in “block” mode as long as a fix is not available.
Another signature “Malicious printer font file download detection”, based on the malicious content of files used in attacks is also available. It is configured by default in “block” mode.