The year starts strong with a critical vulnerability rated 9.8 (CVSS 3.1) discovered on Microsoft Windows 11 and Server 2022 systems as well as Windows Server 2019 and Windows 10 version 1809 (and later in some configurations). Here's an update on a critical vulnerability, with the Stormshield Customer Security Lab team.
Context of the attack
This vulnerability concerns the HTTP stack (http.sys) used in listening to process HTTP requests on IIS (Internet Information Services) servers. It is patched on the last “Patch Tuesday” of January 2022. In practice, sending a specifically crafted packet allows remote code execution (RCE) by unauthenticated users. The level of complexity is low and requires little or no user interaction.
There does not seem to be a Proof Of Concept available in the wild, and this vulnerability is, for the moment, not widely exploited.
Technical details of the attack
Technical details are currently under Microsoft embargo, we will provide an update when we are cleared to do so.
Windows 11 and server 2022 are vulnerable by default. This vulnerability is also present on Windows 10 v1809 and Server 2019 systems with "HTTP Trailer Support" enabled. This can be checked, and disabled, via the following registry key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\HTTP\Parameters\
"EnableTrailerSupport"=dword:00000001
Set to 0, this function is disabled and the vulnerability is no longer exploitable.
Means of protection provided by Stormshield
The vulnerability is covered by the Stormshield Network Security product (SNS). The SES solution is not suitable to protect against the exploitation of this vulnerability.
Stormshield Network Security
The following existing protections built into the static "http" plugin covers the vulnerability:
- http:53 Invalid HTTP Protocol,
- http:55 Possible buffer overflow in HTTP request/reply
In order to be effective, it is necessary to keep the "Other fields" value of the "maximum size of http header" menu below 1900 bytes (by default set to 1024):
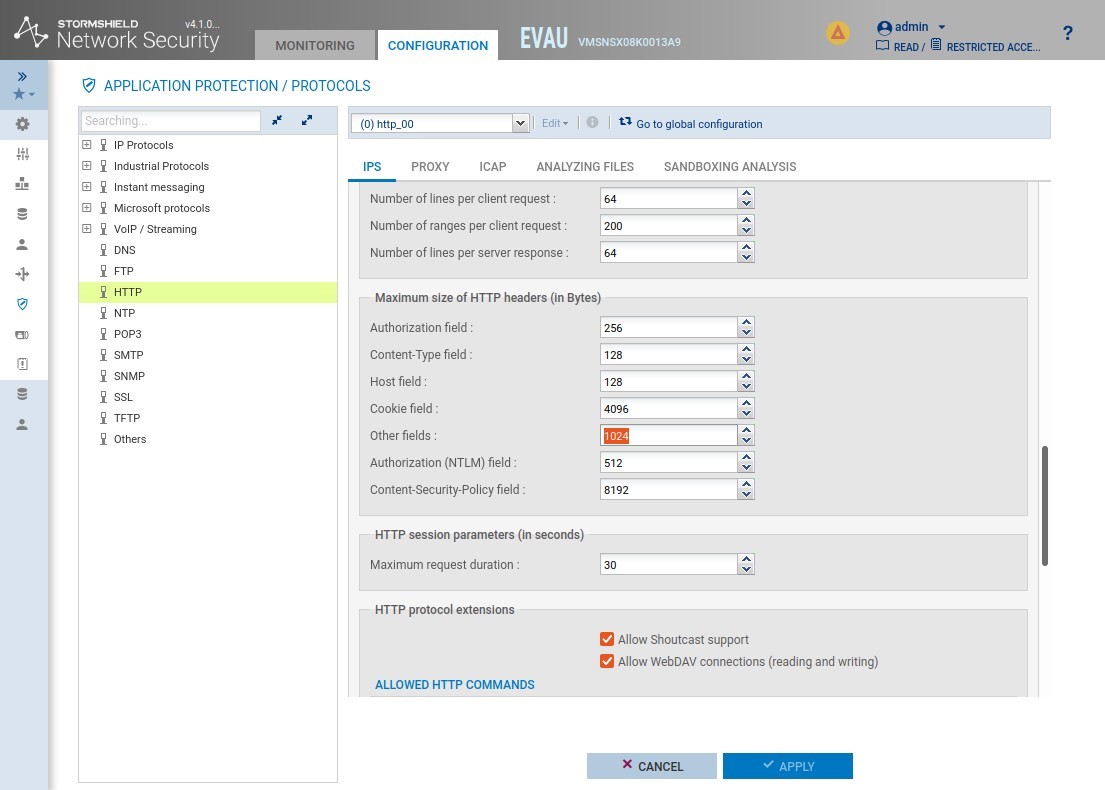
Fig. 1: configuration Other Fields SNS
In the case of an attack on a web server, the protection will be applied to the HTTP flow. For the HTTPS flow, an SSL decryption solution should be positioned before the IPS analysis performed by the SNS.

Confidence index of the protection

Confidence index of no false positives
Stormshield Endpoint Security
SES does not cover against exploitation of this vulnerability.
Recommandations
- Update your Windows 11 et Server 2022 systems with January “patch Tuesday”
- On Windows Server 2019, Windows 10 version 1809 and above, change this registry key value: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\HTTP\Parameters\"EnableTrailerSupport" to 0.
